Time to Patch | Google Issues Warnings for the First Two Zero-Day Vulnerabilities of 2023
Google has released emergency patches for two high-severity zero-day vulnerabilities affecting Chrome, CVE-2023-2136 and CVE-2023-2033, with the latter being actively exploited in the wild. Google is currently restricting access to further details until a majority of Chrome’s 3 billion users have applied the fix.
CVE-2023-2136 targets an integer overflow in Google’s Skia used in Chrome, allowing a remote attacker to perform a sandbox escape via a crafted HTML page if they compromised the renderer process. CVE-2023-2033 is a vulnerability targeting a confusion weakness in the Chrome V8 JavaScript engine. This type of flaw allows attackers to trigger browser crashes through reading or writing memory out-of-buffer bounds. It could also be exploited to run arbitrary code on vulnerable devices.
The latest version of the browser, v112.0.5615.137/138, includes a total of eight fixes. Currently, the stable release covers Windows and Macs and a rollout for Linux is scheduled to arrive in the coming days.
Data Exfiltration | Vice Society Ransomware Gang Uses New Stealthy PowerShell Tool
Notorious ransomware group, Vice Society, has been exercising a ‘rather sophisticated’ PowerShell script to automate data theft from compromised networks. The new tool employs living-off-the-land binaries and scripts (LOLBAS) designed to sidestep alarms from security software used by the targeted party so they can reach the encryption phase of the attack.
Researchers first observed this tool earlier this year when Vice Society began using a script named w1.ps1 referenced in a Script Block Logging event to exfiltrate data from a victim’s network. The script automates the data exfiltration process through multiple functions to identify vulnerable directories where data can be exfiltrated via HTTP POST requests to Vice Society’s servers.
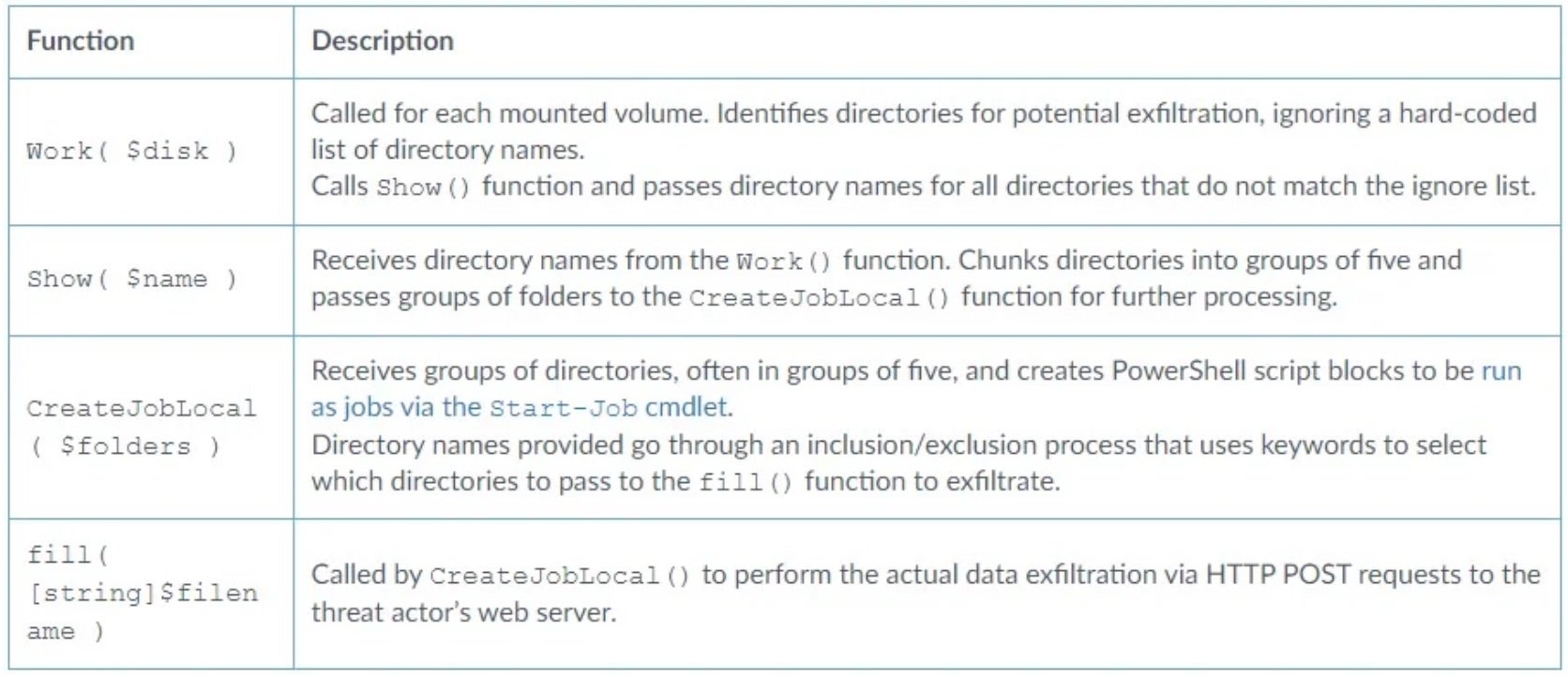
Threat actors often leverage stolen corporate and customer data to extort a higher ransom from their victims and resell to other criminals for additional profit. Vice Society’s newest script allows them to operate stealthily and keep their footprint small – all signs of further evolution since debuting their new file encryptor, PolyVice, back in December 2022.
Critical RCE Flaws | Sandbox Escape PoCs Available for VM2 JavaScript Library
Three recent sandbox escape proof-of-concept (POC) exploits have been released, all enabling attackers to execute malicious code on hosts running VM2. A specialized JavaScript sandbox, VM2 is commonly used by pen-testing frameworks and code editors to run and test untrusted code in isolation. All three flaws have been assigned a critical scoring of 9.8.
CVE-2023-29017 describes a case where VM2 does not properly handle host objects passed to Error.prepareStackTrace during unhandled async errors. Using this, attackers could gain remote code execution rights. CVE-2023-29199 affects VM2’s source code transformer. If exploited, it allows attackers to bypass sandbox protections and gain remote code execution rights on the host running the sandbox. CVE-2023-30547 prevents the handleException() function from sanitizing exceptions discovered in the sandbox. By escaping these sandbox restrictions, attackers can perform arbitrary code execution in the host and potentially set up severe cyberattacks.
VM2 strongly recommends all users and developers using the VM2 library to upgrade to version 3.9.17 to address the security flaws.
LockBit Ransomware | New & Incomplete Samples of macOS Variant Surface
Researchers this week revealed details of a LockBit ransomware sample compiled for Apple’s macOS arm64 architecture. As of now, there are no reports of LockBit for Mac being exploited in the wild, nor any associated distribution method.
The discovered samples use “test” as a hardcoded password for execution, inviting speculation that the threat remains in its development stages. Researchers found that the Mac variant is a direct descendant of the Linux version, recycling much of the same code. Further, the Mac samples do not appear to be capable of exfiltrating the data it locks and has not been shown to have any method of persistence.
A breakdown of the variant shows that there is yet to be a credible threat to Mac endpoints at this time. Though the samples are underdeveloped, a LockBit spokesperson has said development of a Mac ransomware payload is an active project, raising concerns that more effective payloads targeting Apple Mac devices may be not far over the horizon.
Operation DreamJob | Tools Found in Linux Malware Found Tied to 3CX Supply Chain Attack
Operation DreamJob, a long-running campaign led by Lazarus group, has been observed targeting Linux for the first time this week. Using social engineering tactics to target job searchers on various platforms, victims are tricked into downloading malicious files disguised as files containing job opportunities.
After dropping malware on the victim’s device, a ZIP containing a Go-written Linux library is distributed masquerading as a PDF file, prompting victims to double click and launch the “OdicLoader” malware. A second-stage, C++ backdoor called SimplexTea is then launched.
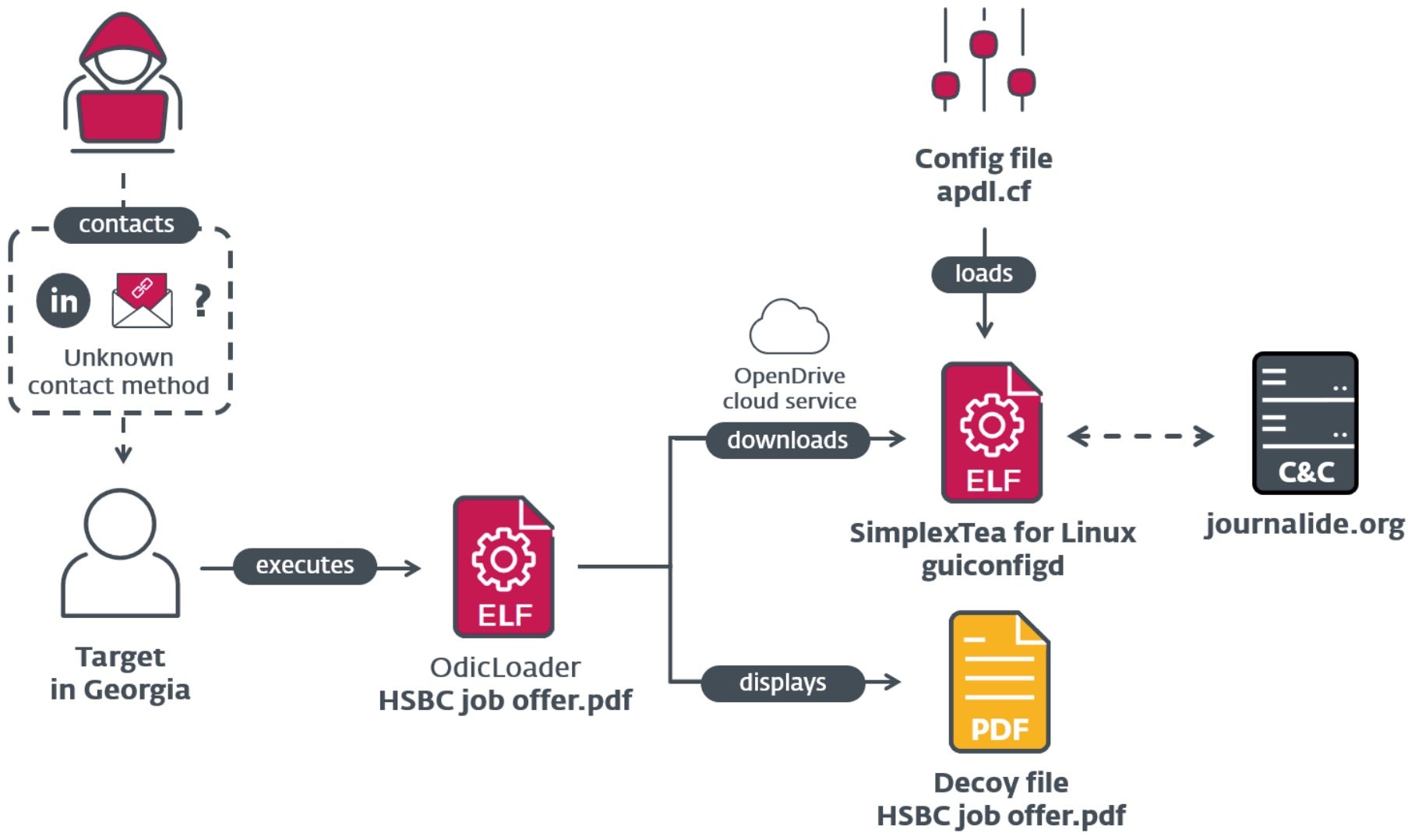
The use of this backdoor and other common artifacts have resulted in researchers linking Operation DreamJob to Smooth Operator – the recent supply chain attack against VoIP provider, 3CX. The attack on 3CX has garnered major attention from the cyber defense community over the past four weeks; the most severe in the growing trend of supply chain attacks.
This Linux-based malware attack attributed to Lazarus is evidence of how threat actors are continuing to grow their arsenal and tactics, expanding their malware variants to target more systems than before.
from SentinelOne https://bit.ly/3N6KHom
via IFTTT


No comments:
Post a Comment