Today, Talos is publishing a glimpse into the most prevalent threats we've observed between March 31 and April 7. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
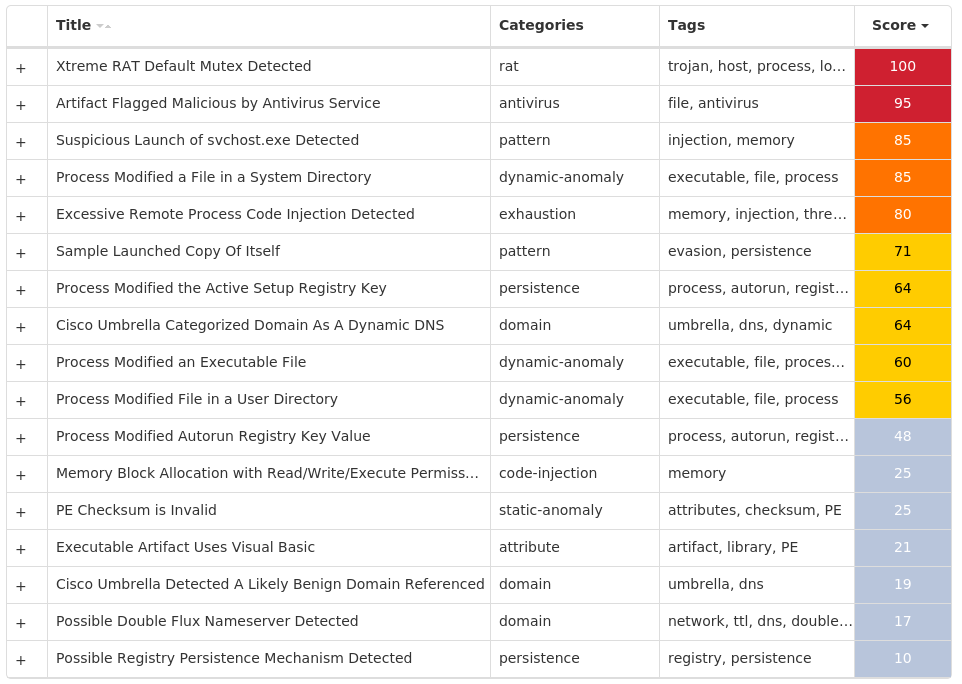
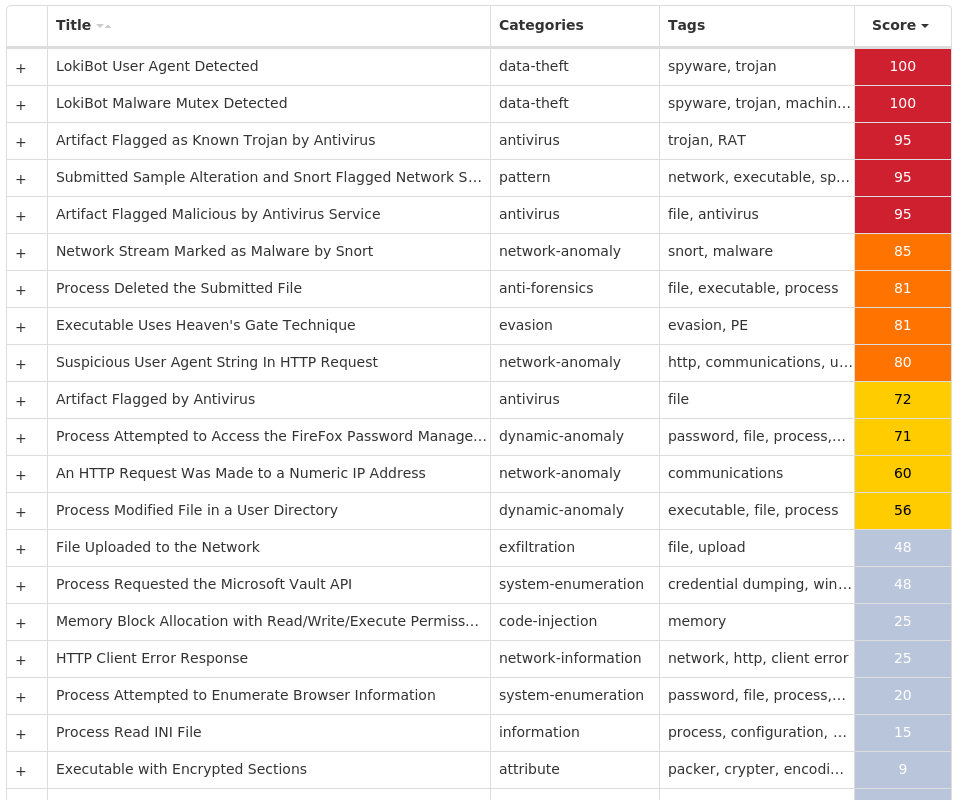
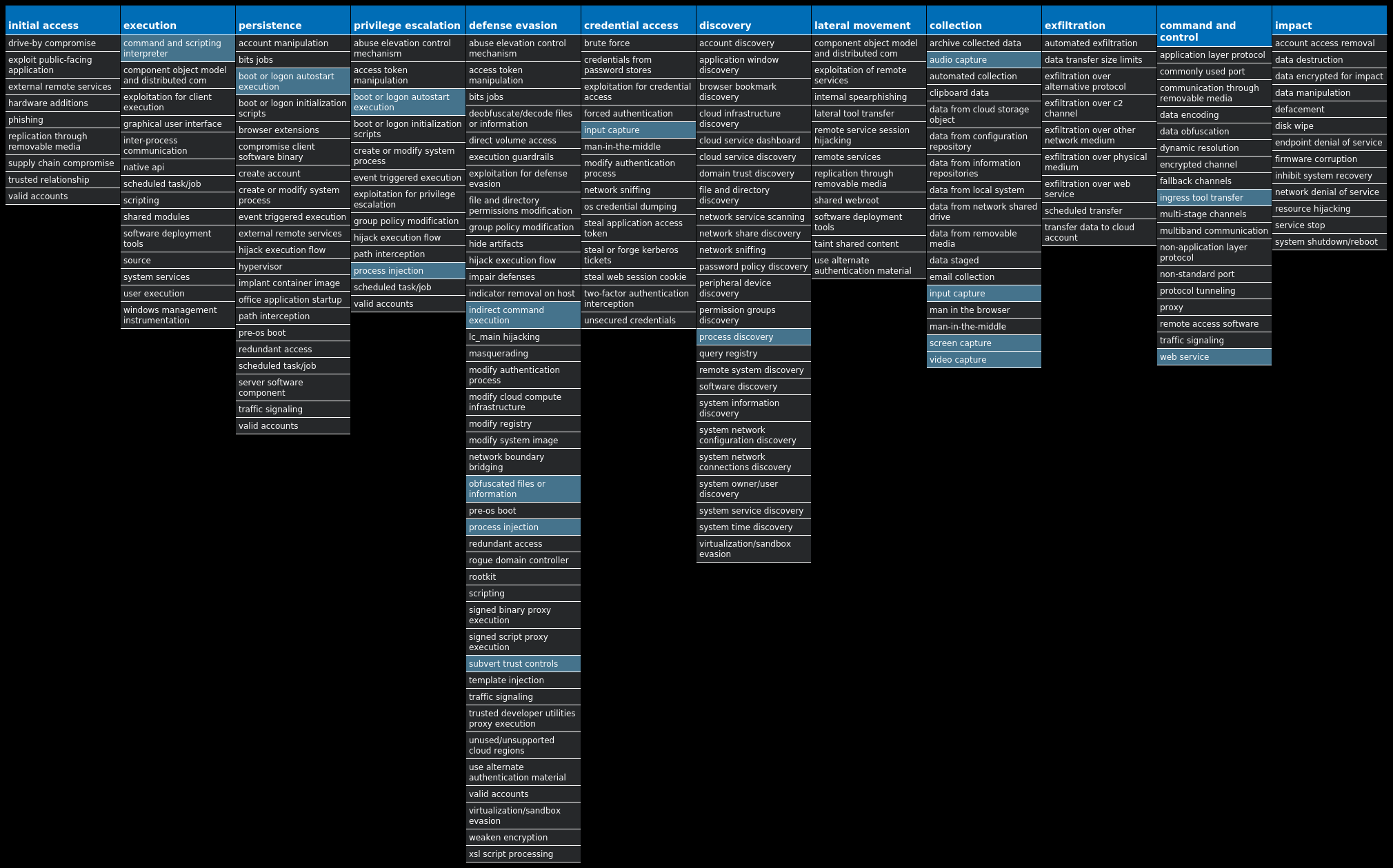
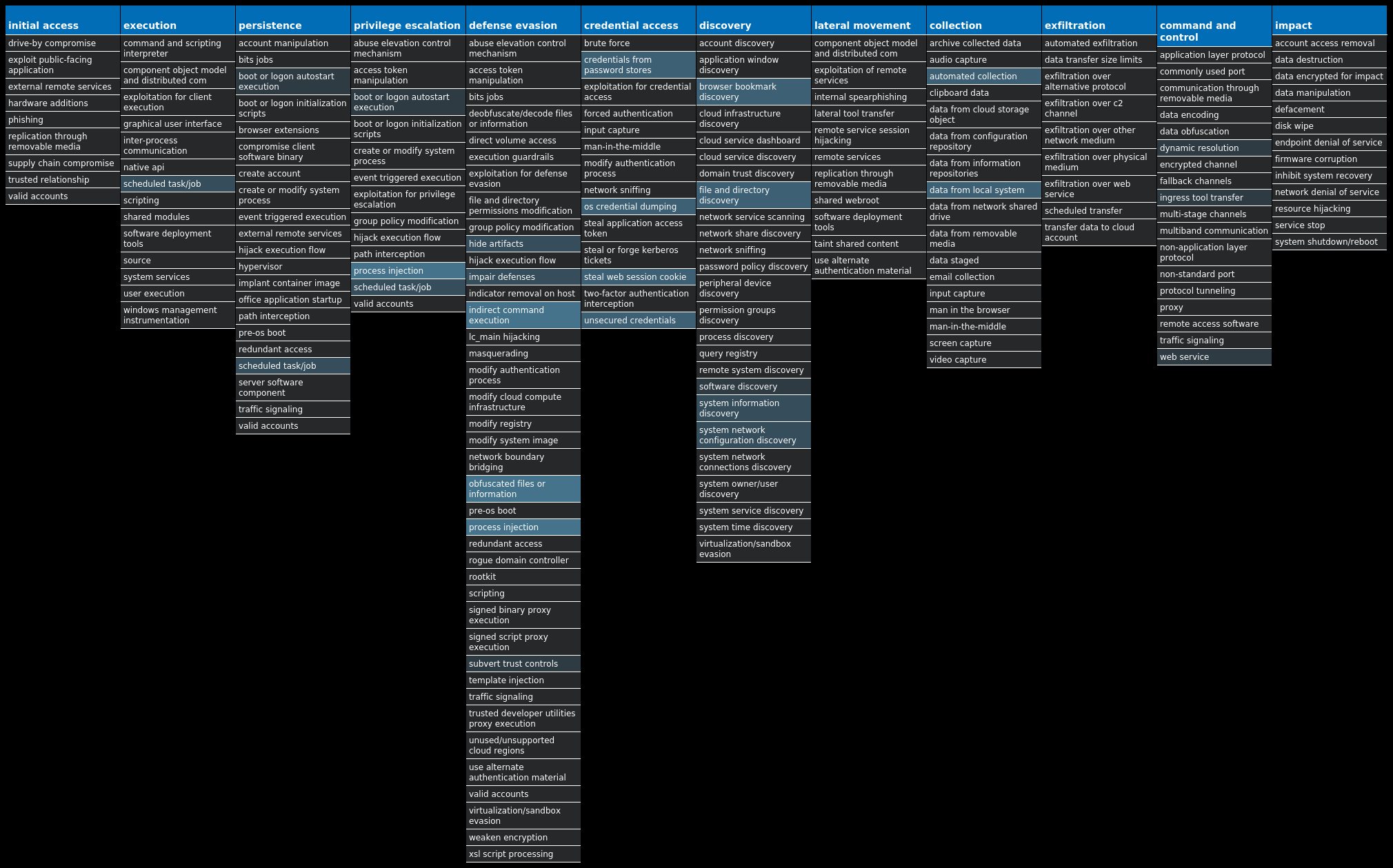
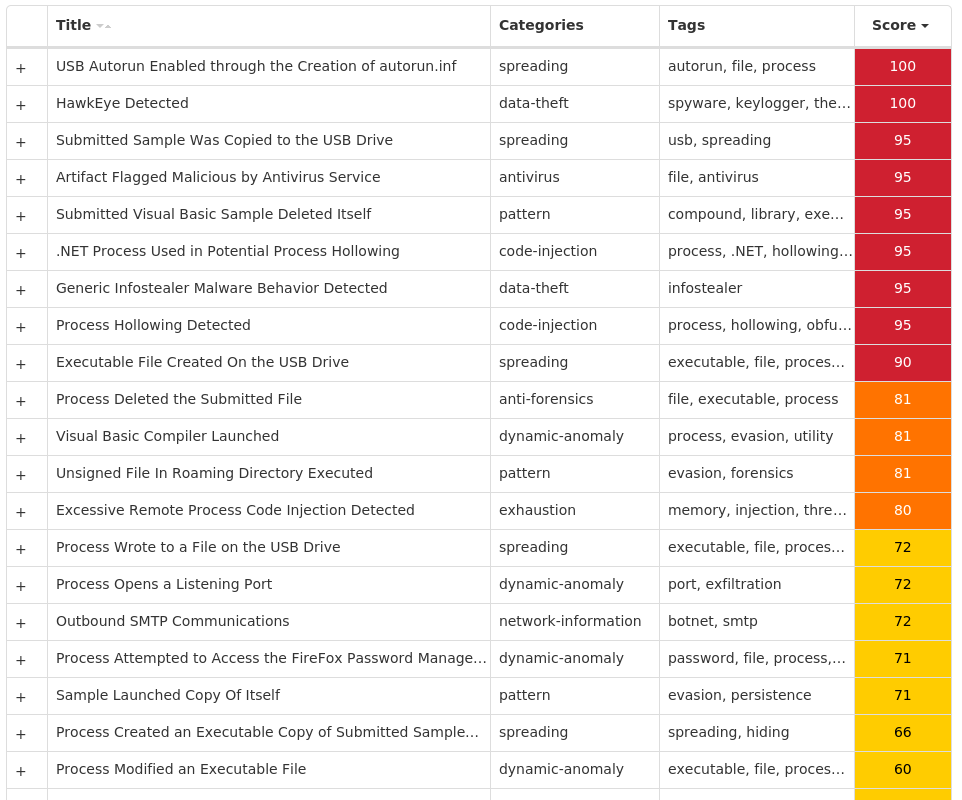
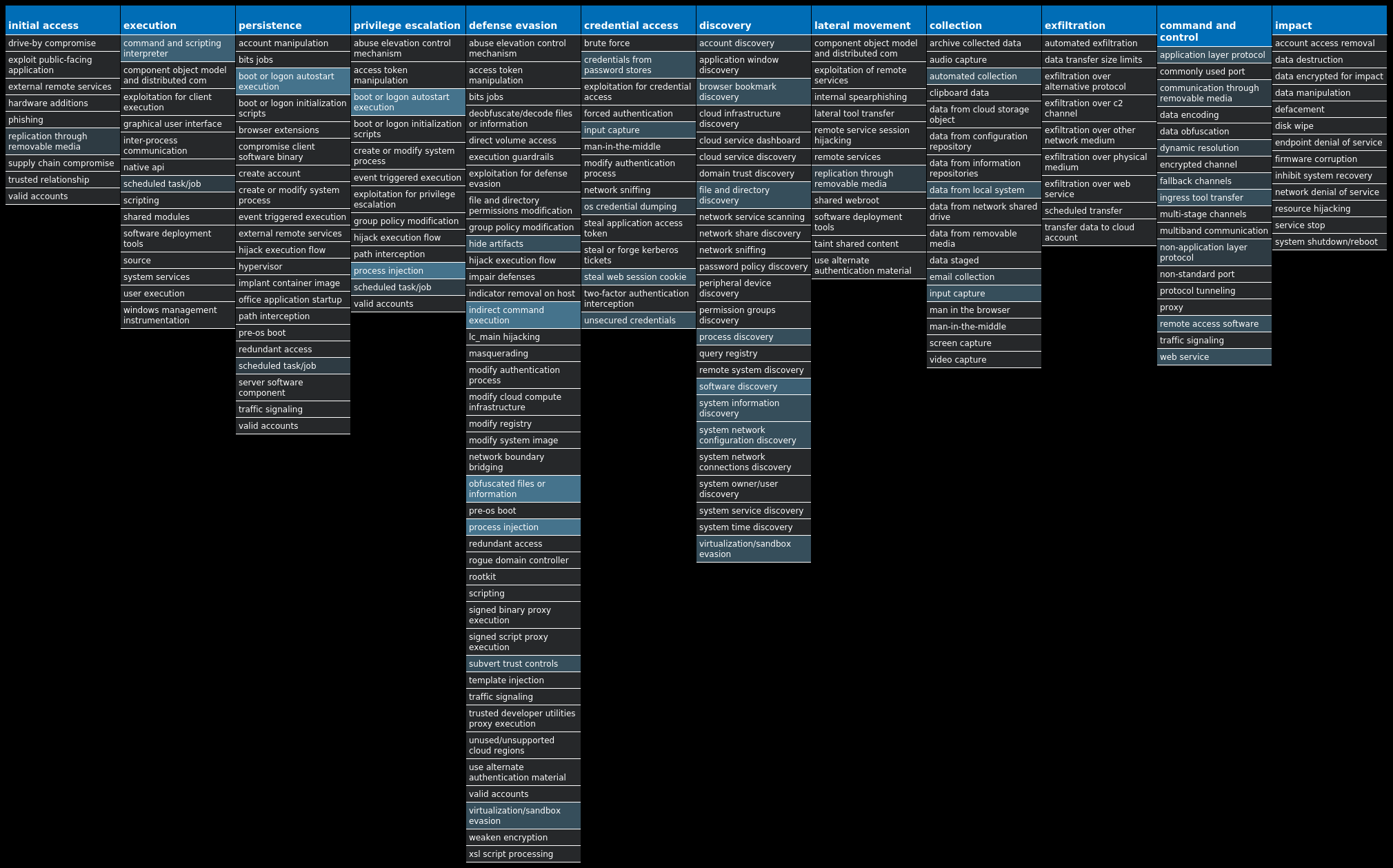
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name
Type
Description
Win.Dropper.XtremeRAT-9995385-0
Dropper
XtremeRAT is a remote access trojan active since 2010 that allows the attacker to eavesdrop on users and modify the running system. The source code for XtremeRAT, written in Delphi, was leaked online and has since been used by similar RATs.
Win.Dropper.LokiBot-9995267-0
Dropper
Lokibot is an information-stealing malware designed to siphon sensitive information stored on an infected device. It is modular in nature, supporting the ability to steal sensitive information from a number of popular applications. It is commonly pushed via malicious documents delivered via spam emails.
Win.Dropper.Shiz-9995265-0
Dropper
Shiz is a remote access trojan that allows an attacker to access an infected machine to harvest sensitive information. It is commonly spread via droppers or by visiting a malicious site.
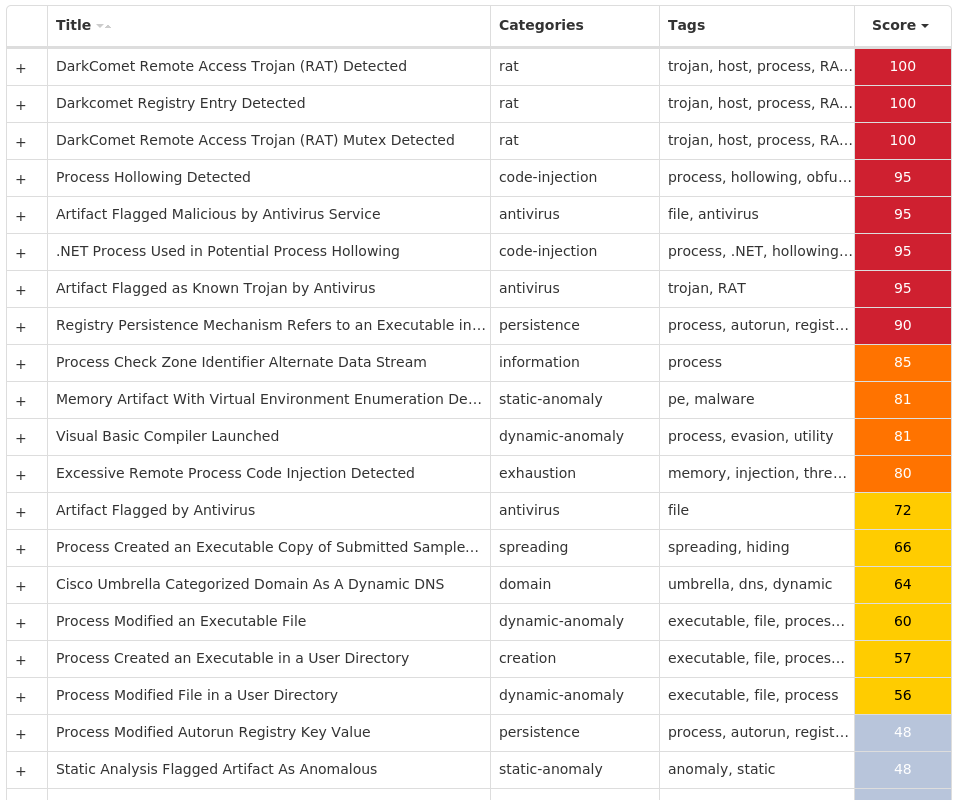
Win.Packed.DarkComet-9995076-1
Packed
DarkComet and related variants are a family of remote access trojans designed to provide an attacker with control over an infected system. Capabilities of this malware include the ability to download files from a user's machine, mechanisms for persistence and hiding, and the ability to send back usernames and passwords from the infected system.
Win.Dropper.Remcos-9994988-0
Dropper
Remcos is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes, interact with a webcam and capture screenshots. This malware is commonly delivered through Microsoft Office documents with macros, sent as attachments on malicious emails.
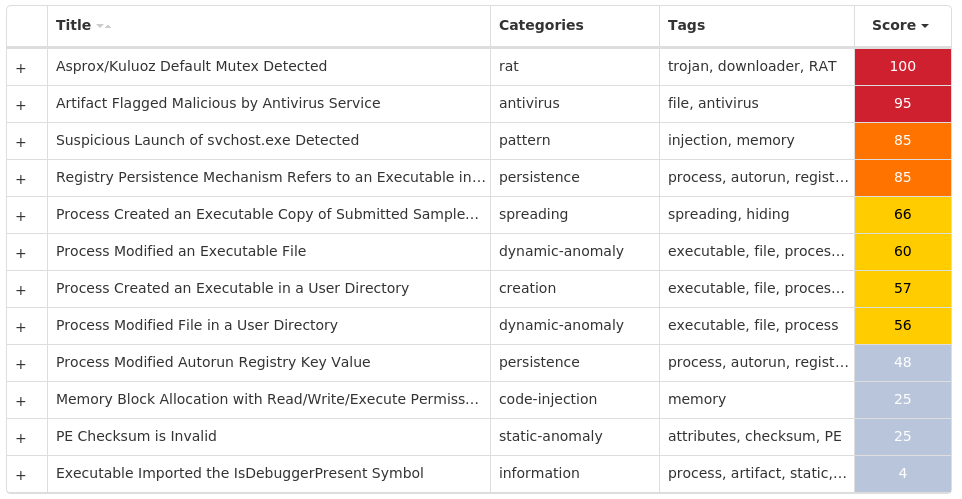
Win.Dropper.Kuluoz-9994888-0
Dropper
Kuluoz, sometimes known as "Asprox," is a modular remote access trojan that is also known to download and execute follow-on malware, such as fake antivirus software. Kuluoz is often delivered via spam emails pretending to be shipment delivery notifications or flight booking confirmations.
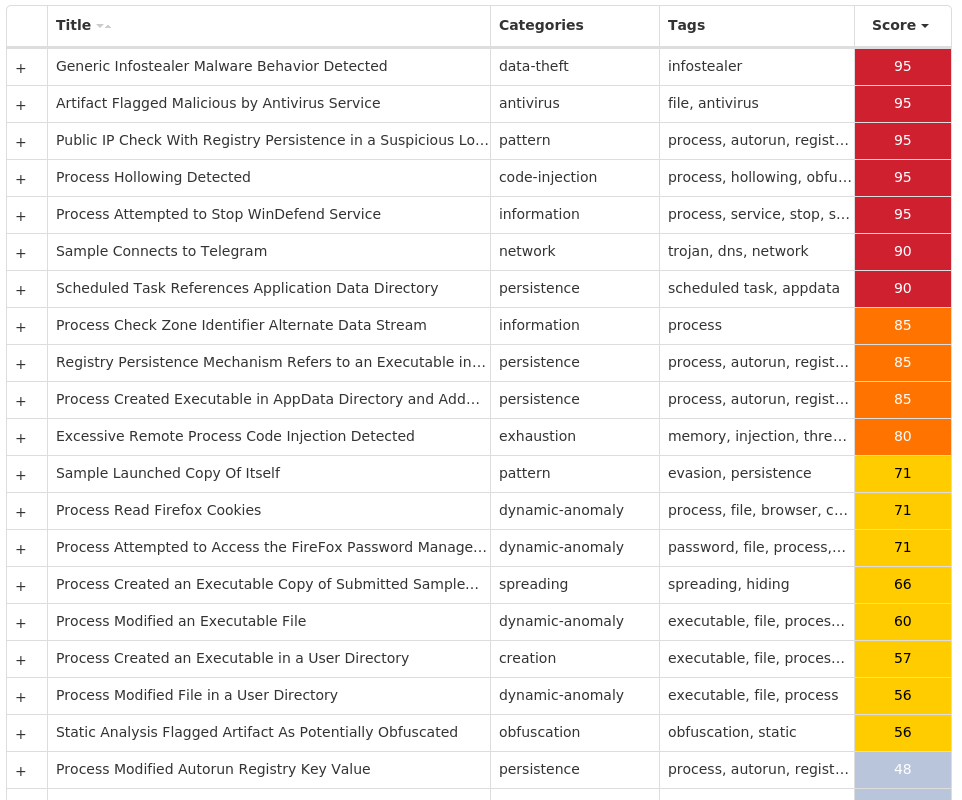
Win.Packed.Formbook-9994793-0
Packed
Formbook is an information stealer that attempts to collect sensitive information from an infected machine by logging keystrokes, stealing saved web browser credentials, and monitoring information copied to the clipboard.
Win.Dropper.Nanocore-9995112-1
Dropper
Nanocore is a .NET remote access trojan. Its source code has been leaked several times, making it widely available. Like other RATs, it allows full control of the system, including recording video and audio, stealing passwords, downloading files and recording keystrokes.
Win.Dropper.HawkEye-9995256-0
Dropper
HawkEye is an information stealing malware that specifically targets usernames and passwords stored by web browsers and mail clients on an infected machine. It is commonly spread via email and can also propagate through removable media.
Threat Breakdown
Win.Dropper.XtremeRAT-9995385-0
Indicators of Compromise
IOCs collected from dynamic analysis of 15 samples
Registry Keys
Occurrences
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: HKLM 12
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: HKCU 12
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{5460C4DF-B266-909E-CB58-E32B79832EB2} Value Name: StubPath 12
<HKCU>\SOFTWARE\((MUTEX)) Value Name: InstalledServer 12
<HKCU>\SOFTWARE\((MUTEX))12
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{5460C4DF-B266-909E-CB58-E32B79832EB2}12
<HKCU>\SOFTWARE\((MUTEX)) Value Name: ServerStarted 12
Mutexes
Occurrences
XTREMEUPDATE12
((Mutex))12
((Mutex))PERSIST12
((Mutex))EXIT12
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
patrickhacker360[.]no-ip[.]biz12
Files and or directories created
Occurrences
%SystemRoot%\SysWOW64\InstallDir12
%TEMP%\x.html12
%APPDATA%\Microsoft\Windows\((Mutex)).cfg12
%APPDATA%\Microsoft\Windows\((Mutex)).dat12
%SystemRoot%\SysWOW64\InstallDir\server.exe12
File Hashes
1665e7cc8465122f23aa001de3f69d41e580c7d2db75a34da8525a95d65a61b43c7b6b60c444fdd79d074b8ba34644a732cc2983b0b77026ee3b2aee07542c014444be8235b07a7528f111d3536e53f99c0d53dab2951f22de20219515fe8242499a60e3be3aeeb69b8e8466322f86471ada67633ce9833298c3db989866c33e52903f4d467243d22524f4debc6a3c34d435d9837208989d1080f8c18456f1aa681996e3e20f98499fc512dd1d5627cf52d0fd1b39ee8071df3246d22d249bb06a041d3aa2b070ac1a6a422a36a670da0c9003ee8cf0f8b1aa6094b8eb86b9c990dc84228efa527f47416c1ed04b4dd70c7232c21d05ffb3dfc58f9db7679862a47478698fec25818bf5ccafb2b39aceaa3199092cd1bd8217ed314e47b5d519baef80b3ad9f039e30a5951bdd740b56b2c7633a9971edaf6721ed0200249cf2c07b2bac3d957040c25f06d8bc351788da435824429dace97b2df8cdc366dfc9c8628d0972489c416e3f215a98c1aed5fe1b2c33808a523e55fcc04eb9195efbcb2bc3233fd60c70478933263fcb90805e7667744d7bd0096d3944cd154215c3dbcc3e2d3cf8423c7572380389a5321fbbf6f9cc49724c7f5341ee376974eaa5f435cfe891cab8b5b95c9c5327c255fa0274e43b58c8601eaab959fe401382e7
Coverage
Product
Protection
Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection
Secure Endpoint
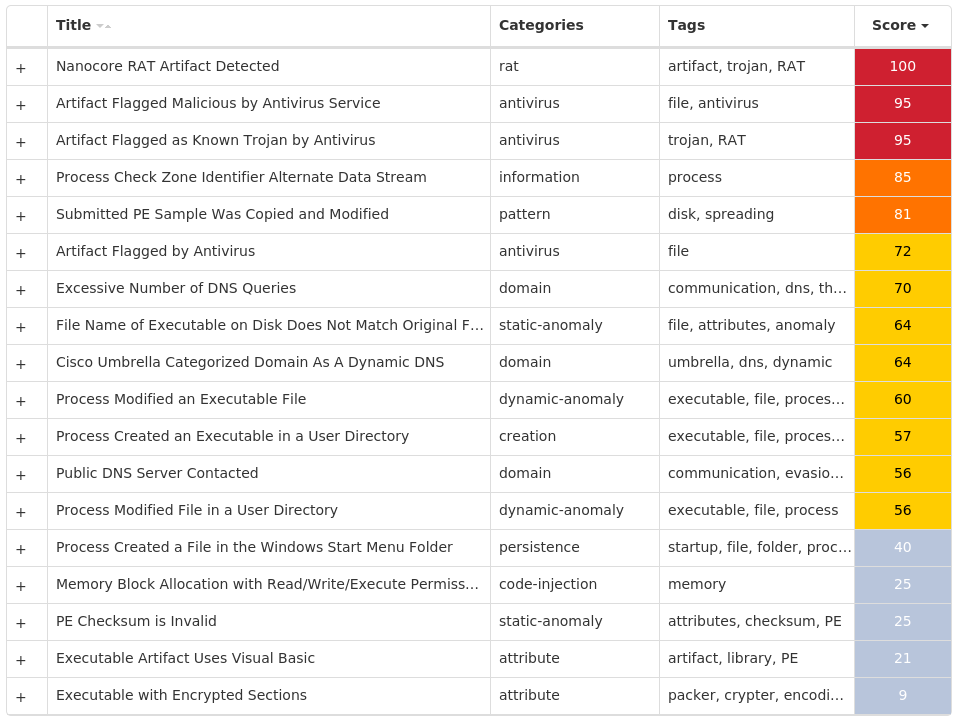
Secure Malware Analytics
MITRE ATT&CK
Win.Dropper.LokiBot-9995267-0
Indicators of Compromise
IOCs collected from dynamic analysis of 38 samples
Registry Keys
Occurrences
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER Value Name: DisableAntiSpyware 26
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND Value Name: Start 26
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU26
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: NoAutoRebootWithLoggedOnUsers 26
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV Value Name: Start 26
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: NoAutoUpdate 26
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableBehaviorMonitoring 26
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableOnAccessProtection 26
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableScanOnRealtimeEnable 26
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableIOAVProtection 26
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER26
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION26
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE26
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS DEFENDER\FEATURES26
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS DEFENDER\FEATURES Value Name: TamperProtection 26
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableRealtimeMonitoring 26
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER26
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: AUOptions 26
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: AutoInstallMinorUpdates 26
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER\NOTIFICATIONS26
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER\NOTIFICATIONS Value Name: DisableNotifications 26
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: UseWUServer 26
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE Value Name: DoNotConnectToWindowsUpdateInternetLocations 26
Mutexes
Occurrences
Random name7
MSCTF.Asm.{00000009-4fb3f26-9d18-66b568-627b8a85e4b6}7
Global\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}7
Session\1\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}7
Session\2\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}7
Session\3\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}7
Session\4\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}7
Session\5\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}7
Session\6\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}7
Session\7\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}7
Session\8\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}7
3749282D282E1E80C56CAE5A1
Global\6f69f321-d229-11ed-9660-001517ddad261
Global\dac866a1-d207-11ed-9660-0015173837571
Global\c87f3f81-d218-11ed-9660-0015171e0af01
Global\b1b3e1e1-d275-11ed-9660-0015170cc5561
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
179[.]43[.]154[.]2167
208[.]67[.]105[.]1481
Files and or directories created
Occurrences
\{09389d67-f724-2900-fb77-cb0d3fc9f9b2}2
%APPDATA%\D282E11
%APPDATA%\D282E1\1E80C5.lck1
%APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c51
\{52d6d7ab-f540-6c27-890a-af500adc9a0d}1
\{4fa167ab-f7e2-ff24-2e48-647ef8633960}1
\{ef6007c6-a5d2-ddd4-8b35-1c2c1f5d4a96}1
\{1e0b0e53-9094-b1ae-cc0d-9f9c10035e4c}1
\{4d62b927-3e23-4273-ae85-f2b51f4bef63}1
File Hashes
003ba45ad5bf2c841859c43721b6bcbb4e1002d9630cc0dd1e1ea8ff2456fd56011a3b2df7bdd0af5098314a22b2c611ca06ddcaa43620d67d53f4933bf8b74204f4ed5fe2e0464f494d03003d29bfa42ca7bca411a13890419a9e023c1dc3c2062cebd1abc7f7adfc8e01683ef0ea34865440c37fc08c06b28fbecfc0b4bd7b07a221bef3d6ab41f7d234a345d1600491f08ee8e1e7a933518ba86b32033731088cda450c0b4bdb9c1b913a73a47a85bd01967c0c94de5bf0045a337e96bb4b0b2174aaa22f46766725e8551d8191ebb66ff12156f5e337438f0e9a00ec0d2a0e0744013438fd9feade11a2bece21edecdccaf75cb4823dcc96a8679023e19a0f434385e7eba23c2f0887f47b3409fe63f15961bd19787e156a43527fa2e06c10a708ad870990986a59f003b7c4ee81f786ef44d182be19e567bc56f7dda26610dc6c1faa1fe94fd3c0aefb39ef1a81d2b8b5013c5fd6518e46ff6bab08adcb11634ea3ef30d4beeb73c51ac5153cbfac5bd12163a8d3f27ef239ce20d4323913fe66d0f85b75af9b4c2ecf8251fa7d1800d7ce0c98210ed09414eb496369bb1476d9a6bdedd18b40867ee7d6d65b2fa85f2824205602dc646594852165e02318577a46633f206d96d4a4d06f8adbcae6fa09f4500db6c5efe820ca6ebe00bf187c183f7991b7527f61460bb2c8632e4a8ff83cadcccd2cb172fc09becf960b1ac4a65da5b8fe68fc3dd892b42e90c861566d754f78965b29428f1b387caf701bbb4374528cf6ca5e75201057498b025cd86af3aadd055eeab1f8df63e060f41cf4020e66e2bfd278b034441991ab9c4b86d90b92d2b70c55eaf9fdf4e4c1d31e8784959fb81f7b1ef0bfa506e34296567683428c4c99421d99c6900a83db8a1f732f2aedbdf313f8d692a263e175d8d433c64177f4186ac086c8124577ccf61f91f110d669e00d2f517ca2a33a19bad9e58e24ed7361099d541a230c61454f1fe4d1be4744591ed9ec166a6ec42082b5f546dd7183d8642b78f5480052c69620205c342c9355306d21950e3a85032de8d3ac6649aab1ffe6c485ac05b4b4a72025af7b32fd101deaaa976af199bb524916da9203fe6d7edeb7cfce0d41ac0b
Coverage
Product
Protection
Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection
Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK
Win.Dropper.Shiz-9995265-0
Indicators of Compromise
IOCs collected from dynamic analysis of 26 samples
Registry Keys
Occurrences
<HKLM>\SOFTWARE\MICROSOFT Value Name: 67497551a 26
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: 98b68e3c 26
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: userinit 26
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: System 26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS Value Name: load 26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS Value Name: run 26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: userinit 26
Mutexes
Occurrences
Global\674972E3a26
Global\MicrosoftSysenterGate726
internal_wutex_0x000004b426
internal_wutex_0x0000043c26
internal_wutex_0x000004dc26
internal_wutex_0x<random, matching [0-9a-f]{8}>26
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
85[.]94[.]194[.]16926
13[.]107[.]21[.]20011
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
jelojujopen[.]eu26
qekafuqafit[.]eu26
ryhyruqeliz[.]eu26
kejepujajeg[.]eu26
tufibiqunit[.]eu26
lygumujycen[.]eu26
xudoxijiwef[.]eu26
pupoliqotul[.]eu26
citahikodab[.]eu26
direfiwahur[.]eu26
vowypikelaf[.]eu26
foqurowyxul[.]eu26
nomimokubab[.]eu26
ganovowuqur[.]eu26
mavaxokitad[.]eu26
rylupalyxad[.]eu26
jecekorosuk[.]eu26
lykiwaryvuk[.]eu26
kezydorekuw[.]eu26
qexeholagav[.]eu26
cilicofahev[.]eu26
vojajofyced[.]eu26
dikolobeliw[.]eu26
fogefobunik[.]eu26
gadurabotiw[.]eu26
*See JSON for more IOCs
Files and or directories created
Occurrences
%TEMP%\<random, matching [A-F0-9]{1,4}>.tmp26
File Hashes
01dfdcbc1c5a712ad5719072756748055311914c08458c9bf451affb40581212041dabd9edcf3c6e11e2f6dc0b5fa876e1cc9b57454df89f77850bf409da681e04b3192daa2bc747a2269e11be69e94ad4b46aac1a3ce833b2b35fc8ae526e530d3c78ebbcbbf8f131eca632bea413e418b491edbb82cc4f5aaa0e7590573f1c126bfe53eb3e3d1c05c827ba28d4d14bc200dc6dfb07d42319b589e3b794f3891275e3cfeb6bcd1f45c4b7d8c894a8439eafde92232ef63451823093437a07881418230802ed9bf38342d91015376a168bb604d47fd9dddc4e15d8c055c2d47b1a72c392397f85b0750f5487ed5342094353f1d87ca88711e27ab7d638b3d41d1bc6e1b9e060db9efb8fb508c9d14fff6ca84ae61e2dbe7a89aa44b71ca5e1ef1de3d63376eb25be9556b2dc07ef6d1746cc653733bc751afe0f275ad3f668831ed4eb3a205a157fa0861b6f8f925b15923ee31215a16dfde29c5cba7e7598771f06519b71ee74ed5ab485355ec031c165dbf0cc68e2550705e9648548d3c9be1f5e7561abc5a3419c4770c0c1717012848a8e4a8e3d31f237af51fcf927584421a919ce78c3911b87b904d9c7a91b3c21c0439b30f851e6119b3f3e0a02330e23fc4e653d62151714cc182e969f09dfb0b2c8e8b23ee1e8d370c937235d577b257456f0582a9387e104e919695dbd09479ea3d1b91535a5d185de28364d0f0c2a3427057a865172a65af32928e71f316d86ab21cd3891a29c99cc2152594d792b22416fdc05a7a2be27f1c2c776232a412af0d53739bb36f2272867ff486dae2b84d2ee8e5e3db10522cdd4a95f6ebf4f281b5581af6efb090848a43d6b46df2bf5783ce8934164208cbd876a282fa87a18dc1a8c85f3880f770f64cdf48ce12ee6780c728fe0d17f0e49a2fc5081701cabb6709830dc5ddd48d57ecf1da154327ec487335d74e4cb2274fda32584646592cb465cb9933983d567543c33bae033a85f67668d59accd4fcb7ad94bec55815c3efebf26a302875a7e29947b44f937377bd36d7d46bb717a42d959114231165ef80cb43aed53cfb315b9cfaee693384a88aa045a2bdff9d8f4c559c2339a2dc9fe09a51e4cada6ce678de99e35e5
Coverage
Product
Protection
Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
WSA
Screenshots of Detection
Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK
Win.Packed.DarkComet-9995076-1
Indicators of Compromise
IOCs collected from dynamic analysis of 14 samples
Registry Keys
Occurrences
<HKCU>\SOFTWARE\DC3_FEXEC13
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: UserInit 5
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: MicroUpdate 3
<HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: LanguageList 3
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: vbc 3
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Visual Basic Console 2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: DarkComet RAT 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: sdfsdf 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: test 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: svchost 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: wupdate 1
Mutexes
Occurrences
DC_MUTEX-<random, matching [A-Z0-9]{7}>7
DCMIN_MUTEX-UXH4D501
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
bakel[.]zapto[.]org2
voss-water[.]no-ip[.]biz2
jesus123[.]no-ip[.]biz1
thunderbluet97[.]no-ip[.]org1
d0nuts[.]no-ip[.]biz1
srv4006607[.]uppcdn[.]com1
ec542356yg[.]no-ip[.]org1
Files and or directories created
Occurrences
%TEMP%\AppLunch13
%TEMP%\AppLunch\Cho.ine13
%APPDATA%\dclogs7
%HOMEPATH%\Documents\MSDCSC3
%HOMEPATH%\Documents\MSDCSC\msdcsc.exe3
%TEMP%\vbc3
%TEMP%\vbc\vbc.exe3
%TEMP%\Visual Basic Console2
%TEMP%\Visual Basic Console\Visual Basic Console.exe2
%HOMEPATH%\Documents\DCSCMIN1
%HOMEPATH%\Documents\DCSCMIN\IMDCSC.exe1
%TEMP%\svchost1
%TEMP%\svchost\svchost.exe1
%TEMP%\test1
%TEMP%\sdfsdf1
%TEMP%\sdfsdf\sdfsdf.exe1
%TEMP%\tmp91.exe1
%TEMP%\wupdate1
%TEMP%\wupdate\wupdate.exe1
File Hashes
131003a2e0f0dc3733981dd29800bfde5eac304eb28d73d026589d4901c1c18d274e98365987db708a9f4f279f19c6f70383cbf18410fd601ffd7fefa16aaab430baaca5ee5a35349d194a6d64fcd398ee4e675303db3e1d4ff0018a374c14d048b1c0ae81d355b8134e75c6a8de91b262e917e5e9c60e620a8d31e5cd53ce7d514eb2f78c985682439cdfa719969687f7067dabe438fb7ba8b31f4be4cb05905ed3653e12a0fc82c9baa31ac4b7342ccb1a141e253689d5267a13c1bc6e01ce5f9a350b8ac57470c0b4065b7d70a86caa757ef6e7741b90751063b3472cbd7a734835ef459b083345d198986b57f1bc05272cea844a26bf80260154107b63ee7d7663db28899c9a083acfc7efc1942188b40296275fa322290622636533cf8f8608957106da74076ea69aaacc0995a7a2f166cc29d6fcc671c6e3c9ac98215f98093405e0bfcfb47c5e7a153d84089d522aa83da6820c5f8b402fd8459821c19e9acc5caea8367880ceacfaaa9160b7d63d71064ea8e5eface950e371244047afd67b81235161cdd4f8e06a81a7d8f5453cdbb11af7b1abcab5f58465d76b34e2c66a3f9d630d1f9ee37cf0c56688133b2b13c73a03a3677d82ea37a70180be
Coverage
Product
Protection
Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection
Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK
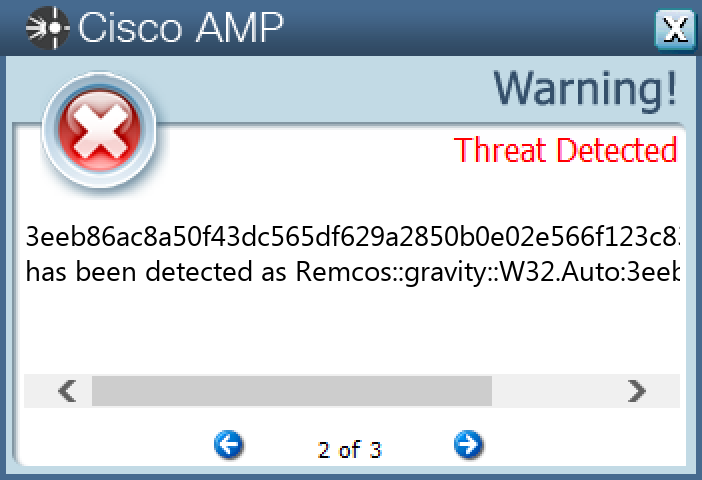
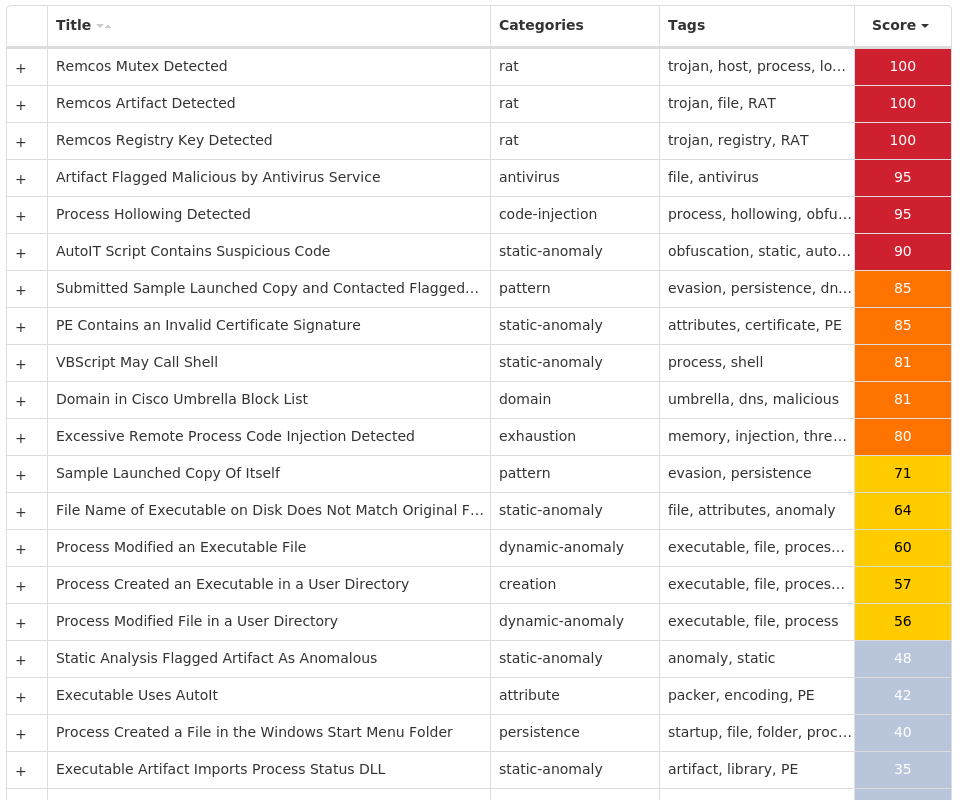
Win.Dropper.Remcos-9994988-0
Indicators of Compromise
IOCs collected from dynamic analysis of 10 samples
Registry Keys
Occurrences
<HKCU>\SOFTWARE\R-8943LY Value Name: licence 10
<HKCU>\SOFTWARE\R-8943LY10
<HKCU>\SOFTWARE\R-8943LY Value Name: exepath 10
Mutexes
Occurrences
Remcos_Mutex_Inj10
dccw10
r-8943LY10
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
185[.]29[.]11[.]3110
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
remcoss[.]onmypc[.]org10
Files and or directories created
Occurrences
%APPDATA%\remcos10
%APPDATA%\remcos\logs.dat10
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\whoami.url10
%HOMEPATH%\WerFault10
%HOMEPATH%\WerFault\ipconfig.exe10
%HOMEPATH%\WerFault\whoami.vbs10
File Hashes
1d33b7a9d533212bab85b75643a357defce3e3ccc4a8e8e60d67bc20223b55b13eeb86ac8a50f43dc565df629a2850b0e02e566f123c83a92a36b549766df30174f9a164ddf0693a977c6ec95a5ad3589bd4c671d932d22412f59f39fa05cade7871c62f90043573a44acba9c896730f15227c23b4670022d95ac9fd6f33d9227b0c7c29e518f6ffbe4dd7b3f8a7d8fba09a41eda2db2318ccc6b4990475e7e593e0d0ac6156d2b37f6f9275d0424c58602a5fb33ee5ff8de778be90fb0cc0c9b54ae33e1ef5e7f555a63411c2e057cd36b22b0cacf1c7b0d6aa15326d513d68b64e68eae5411c64fbab787fa265a1ec5d275f272ee4474814c06c474226da1ec0876549fb4dfb5356cb49f6e5f1ee2f42886748d2b50d7455456f52ea661176dce9831c76589d0d421b7d11d0e8864ac6482cc4d33dfdb1a771ab8c67f2105d
Coverage
Product
Protection
Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
WSA
Screenshots of Detection
Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK
Win.Dropper.Kuluoz-9994888-0
Indicators of Compromise
IOCs collected from dynamic analysis of 26 samples
Registry Keys
Occurrences
<HKCU>\SOFTWARE\<random, matching '[a-zA-Z0-9]{5,9}'>26
<HKCU>\SOFTWARE\HAFQELRH Value Name: kxlorvxn 3
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: xkacxqqr 3
<HKCU>\SOFTWARE\OWMXSCVT Value Name: clpghwqf 2
<HKCU>\SOFTWARE\GFEKSCVG Value Name: vmbrerlw 2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bdpudrav 2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: nxujmuak 2
<HKCU>\SOFTWARE\JUQHUMGW Value Name: sqvsspvn 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: clxucfsq 1
<HKCU>\SOFTWARE\NHHMDEUC Value Name: bkebjrtj 1
<HKCU>\SOFTWARE\OELVBAJU Value Name: xwbcmfrn 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: rvebcdos 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: rdnapsgm 1
<HKCU>\SOFTWARE\MPBVOFKE Value Name: xwiivafw 1
<HKCU>\SOFTWARE\VUXUWDIM Value Name: dvtsxnuf 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: gxwdapdt 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: wkhpgjfw 1
<HKCU>\SOFTWARE\IDIWBVCK Value Name: nxsksrvb 1
<HKCU>\SOFTWARE\MGGJRFEA Value Name: hliipngk 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: pahgaxfk 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: wkstlpbm 1
<HKCU>\SOFTWARE\IPWQSJEP Value Name: khtlimfj 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: fiursbbg 1
<HKCU>\SOFTWARE\GITNNMRX Value Name: hceuxock 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: cedaixee 1
Mutexes
Occurrences
2GVWNQJz126
CCXPO_13_wKSU26
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
76[.]74[.]184[.]12718
203[.]157[.]142[.]215
193[.]247[.]238[.]2612
81[.]177[.]180[.]8312
151[.]3[.]8[.]10611
87[.]106[.]200[.]14011
113[.]53[.]247[.]14710
178[.]132[.]218[.]1809
91[.]121[.]70[.]149
142[.]4[.]60[.]2428
88[.]255[.]149[.]118
207[.]210[.]106[.]587
Files and or directories created
Occurrences
%LOCALAPPDATA%\<random, matching '[a-z]{8}'>.exe26
File Hashes
00502f3a5e474959f8ce93b5feeb79dd7f6eff4ecd7dbefe0c2e3678de0eedf601426a2a369847c154bbf2ee9fe8d2fa4c35fbac43dc9a67beeda28f31329ee4016f8bb1679a9874d406645ec5fbf9fe01f1349c718c2a19507dcd01ff2bbbbf0220e3fc2b2066f271a89c632da64595d838544de4b5ebc5f04aac66940971f7028fdd74004cff65fe2f4977a71c402008874a2ad55f38b29f8edb093ae8c2d902ba868962d78226f227bd28fbcb968e4b4fca390ed617c2f3ccc30f60159a210c493764094a0f20f2066b1c6dd5620cecf298d0474c0e27c8502efdd84ad1cb0d875382e169d8d0cee865be13592c356f3e0bda4c53709e7cb6cf1c058e1a4c0e295123a220ffab3b256d7dfb4c9d628d8cfbd60c3860df3690b45b12ce8da50f84d1068efc6101d418994a6c0141d1bb5163e1853dc4c846bc297b748218711041183e190b64467f531ab81cc85fc600f19b04d869d741a7540f7e887d19c111a5c730b3f4114d72e6d756bf7a56b8f5a3ddc4acfb4ea26f8e7f789fce4db013858a319ec0f498c3bcadd3fe22c4a6f98c8aef8046039afa07cfcb2ac9c0a315f934e01433fbf5045a4b02ad70f220113c65966300081bbee7c825992763b5192c9c3b0a954bbbc6c28580031cc70dc30cb759cd3b04c374a7aa000dcdedac20ff0ac60be2dcd35809c92b0cfd47e966c821df2627713f1acdb5d68c8ce92b22a4ff01ae30c88ca2237c306eb74cf7b237d7f19992cd04498802531fbbbc3722fe5826d997627a3b8de9bf294c64982ead2ce0e0e8a714701e2c0031724cd727290dadc36cce8e75a1940f42c0006275bebe27e4f6e8bf145b0559e001ee0c29788f51207813c3403377e1674f468d20d3ed7e45f15dbe1ca1ad044bdf27922ad296ade0c55703b53b8270aa494fdbe8a577e134e3cfeb7c766981602d96d92afecd890b126bc1fbbe694b40a8d64f9c6feacf3e92589a2aaa85cacf1b9f6b35d506f99a4e9022a56c5b1c344b6e29d045359563198b3aaf906acaf9e737e636e28c49a0cbd460214b4b4f8525ad08a2a34637d2662161b3ec352a742179453aad7855aecc9e3d66c8bf8e3882a43f20e92f84c33997c46ec247303f5fca2b
Coverage
Product
Protection
Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection
Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK
Indicators of Compromise
IOCs collected from dynamic analysis of 21 samples
Registry Keys
Occurrences
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: plQRn 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: PNGtqM 1
Mutexes
Occurrences
EjfrUHmSaeLyAw1
lCBadJKalzHVx1
tYgeoYfktDpsVQQSNxKR1
fnawPTxiuhcCnV1
PdJlJpQBGeZl1
pYOWDiaVcdPoRQxHsIjYubQOHDH1
gPVBNpPJwOaSGwOgGUyNr1
sVTndEbRmocUxXOJmJ1
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
158[.]101[.]44[.]2422
173[.]231[.]16[.]762
149[.]154[.]167[.]2201
193[.]122[.]6[.]1681
193[.]122[.]130[.]01
104[.]237[.]62[.]2111
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
checkip[.]dyndns[.]org4
api[.]ipify[.]org3
api[.]telegram[.]org1
Files and or directories created
Occurrences
%System32%\Tasks\Updates6
%TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp6
%APPDATA%\plQRn1
%APPDATA%\plQRn\plQRn.exe1
%APPDATA%\CGUzozPmYLV.exe1
%System32%\Tasks\Updates\CGUzozPmYLV1
%APPDATA%\PNGtqM1
%APPDATA%\PNGtqM\PNGtqM.exe1
%APPDATA%\tohNGyREiJ.exe1
%APPDATA%\bqzFpcTimliUk.exe1
%System32%\Tasks\Updates\bqzFpcTimliUk1
%System32%\Tasks\Updates\tohNGyREiJ1
%APPDATA%\NQUFZzfwxJKEr.exe1
%System32%\Tasks\Updates\NQUFZzfwxJKEr1
%APPDATA%\i2yitwbu.evy1
%APPDATA%\i2yitwbu.evy\Firefox1
%APPDATA%\i2yitwbu.evy\Firefox\Profiles1
%APPDATA%\i2yitwbu.evy\Firefox\Profiles\1lcuq8ab.default1
%APPDATA%\i2yitwbu.evy\Firefox\Profiles\1lcuq8ab.default\cookies.sqlite1
%APPDATA%\pGnxfTwNhIldl.exe1
%System32%\Tasks\Updates\pGnxfTwNhIldl1
%APPDATA%\CgusLjCsguWt.exe1
%System32%\Tasks\Updates\CgusLjCsguWt1
File Hashes
05f0a9fc7417c605c638b3ffda615fd6b20795a82b0408fe3f42f055de85103d198059af372b0917f0956f52c31117a5c7e1f0fd50a18bde92aa37a791930f032385c755372ca2515b6292191f16a197e5c82aaa7e40652b33690185c2d932de23a229335d91eae22c93b6bc7e57f7220bbc490af20e1580d5fdd4f3fc5327d134444f68609f8bb2253146f628bf1d4aee1209e03daf5403af99aca970ef55ba475ece56e57f220405bef9961b8e6013f839ef07eadea3f23790263f841d50dc5d2841d221d5f4b73591f9972ece12a9382fb40146caa6e8691eba12ae1380495dc52da7b97835654bab2a3a39e93d412a50608bfd7dfccb87ff716c9aba6a376181b4c5486a0d60e6254433d64e2cdd71f5d10c76411b85a2ebfc369a1573bd880a6f3c4afc5c947d48dc37270a5802b967cbd0af49d291fddbb8a38a18d1bf8e576e578efa64de8ed384743375e6bc3f3a074d508e510893cfe734cbfacef3a811fab0870234aa3d7af40ce5a42e009eb341600c7968555853c2f2473bbeaaadcb18871ff1d333a1f9170996a33c430610d03288d8def0cb010380f3d3791db43c354874e511906b2a3abef9db96af2a2d0aec46c8d04fe7357bcebdf03a4fb9e9daf6bb717f1fcf48903988ff22e8d08a2d7df065f08d4f7051afced9d66cbc6f62b0067cfa2b40571e869f9757fcfcc91ce95e057140757eb1d54513836acdf11f641788c28835c7205b496817c904a9c1ef6f7f390e5dce13d4ad93129ad6ddfb183079fd5ea960c75022874f71bd25f9586c748ab9cec41e39e437e725db14e99ef27cd34b8683f55fe26224400b4d9a2ef5498a8c8968782702e0dbecf1b1e544557474eda8724e661a04df7560da10d5879e457675dc7a2e4c354ff9f90832c3ae71cb6a7b3cbfd91583bc682d8a78c45739201d59b6c5b56e580536
Coverage
Product
Protection
Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection
Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK
Win.Dropper.Nanocore-9995112-1
Indicators of Compromise
IOCs collected from dynamic analysis of 10 samples
Mutexes
Occurrences
Global\{75b74e6b-77a5-42a6-b447-2fa106e8ff08}10
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
obelltd[.]ddns[.]net10
Files and or directories created
Occurrences
%APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C510
%APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs10
%APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs\Administrator10
%APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\run.dat10
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\filenet.vbe10
%APPDATA%\filenet.exe10
File Hashes
0d36017cc6ac2ccd7b332ef4efc2c3a7c039c594caab75eff13999fbb27b59801b7ccd74712bddd6ae3cea21cabe65d7dad02d39a798034b04fded11b6f4107c4d55b18caa7ee41188782449112c0719a1ca4947369d085c574d9f0a6cbc0cb779c3bc8be1465c3a72ff719eef3c4435e71fc05b7dfbd62c312199c3245321eb811691edb836d119ba756746fb52c00bf86116cc03279659e29bbd2226ed6d4781862d48d9e761d5fef1cc33a64a9bd3f87b9ba7df5caa40c82facef881b61799fd490f05a7cab1c35bc5d911d1dd7eab653ec040f4b5e0fecfa903acd02fa30a41a0da8626e4a2a6cf1f8e281b35ee5a8d098a80b3579018444768f51af7a91c72cfbc5eceeab714b402f122959646387520e280fe45366eea5c18b19af0cbbff56012a53c1f9ff4b861e694dcb05605a4c4f23aff1a4a2efe5c0fbb83d9f10
Coverage
Product
Protection
Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection
Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK
Win.Dropper.HawkEye-9995256-0
Indicators of Compromise
IOCs collected from dynamic analysis of 25 samples
Registry Keys
Occurrences
<HKCU>\SOFTWARE\DC3_FEXEC7
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: AGP Manager 6
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED Value Name: Hidden 5
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: Axrozue 3
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: Zaxuner 2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: Acuxern 2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: ptm 1
<HKCU>\ACRONIS1
<HKCU>\ACRONIS Value Name: Conv 1
<HKCU>\ACRONIS Value Name: ConvAsAdm 1
<HKCU>\ACRONIS Value Name: IsAdmin 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: Coreuv 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: Short Term 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: outlook_sys 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: Long Term Loan 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: firefox 1
Mutexes
Occurrences
GLOBAL\{<random GUID>}7
DC_MUTEX-VW9E0BJ3
DC_MUTEX-SNQ9FC52
DC_MUTEX-XU9P7EK2
2f120e27-e0dd-40c0-926d-cacc170a801b1
CB228061E88BC2B69FA01FC09F3CAE001
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
217[.]160[.]0[.]1438
77[.]88[.]21[.]1585
104[.]16[.]155[.]363
185[.]209[.]85[.]1833
104[.]16[.]154[.]362
103[.]70[.]136[.]1001
185[.]84[.]181[.]721
193[.]122[.]6[.]1681
185[.]82[.]220[.]1371
191[.]101[.]22[.]341
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
salako[.]net8
whatismyipaddress[.]com5
smtp[.]yandex[.]com5
checkip[.]dyndns[.]org1
minergate[.]sytes[.]net1
logover[.]su1
delta[.]http80[.]info1
monarch1[.]myddns[.]me1
wilfred123[.]ddns[.]net1
chevalblanc[.]1e517001[.]to1
chevalblanc[.]93319601[.]to1
chevalblanc[.]81252b01[.]to1
chevalblanc[.]bb8c4e01[.]to1
chevalblanc[.]6a0fe901[.]to1
chevalblanc[.]wm01[.]to1
chevalblanc[.]49b56c01[.]to1
chevalblanc[.]69385701[.]to1
chevalblanc[.]53fb0701[.]to1
chevalblanc[.]efe87401[.]to1
chevalblanc[.]cf488101[.]to1
Files and or directories created
Occurrences
%APPDATA%\dclogs7
%APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C57
%APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs7
%APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs\Administrator7
%APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\run.dat7
%ProgramFiles(x86)%\AGP Manager6
%ProgramFiles(x86)%\AGP Manager\agpmgr.exe6
\Sys.exe5
\autorun.inf5
E:\autorun.inf5
%APPDATA%\pid.txt5
%APPDATA%\pidloc.txt5
%TEMP%\holdermail.txt5
%TEMP%\holderwb.txt5
%TEMP%\SysInfo.txt5
%APPDATA%\Windows Update.exe5
E:\Sys.exe5
%APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\task.dat3
%System32%\Tasks\AGP Manager3
%System32%\Tasks\AGP Manager Task3
%TEMP%\win86.exe3
%TEMP%\Axrozun3
%TEMP%\Axrozun\azrezon.exe3
%TEMP%\Axrozun\azrezon.vbs3
%TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp3
*See JSON for more IOCs
File Hashes
287a6c0f58a354b6fbbce18d6d2bdf9082a0fb15c293b215c428977cd2ba584432801325c6a7e2512338c52618569bfe42e0ccc414ad8403478e832c621872c932e33f3283cbb118ab9cb4bac65e9207fb19472ac0526c1ccde3c09dfbe0700734234ccbab39e5876a404340e61f3772c0459c03a8bcb49ce81df08b5155300c36fb3d0e48ee960deeb4d88fe7c1f8c1ad3315eec57c95113ac1fee0afcf2d6e3e4e4cd4d9b33b20816288baa2715c5b44b1e750e27b49cbd6d3f9f806ca80016886bb95013a9f916fbbde507c721a2df5863b077f37bd20097e0fe43772dc127039f7b53d740f9d27da784b3dbbff127c8e4926af4517c77a884d8d3e22455e75168296430a81c1b6a07ec4ae998b2b9e8ce8dc6de4f7c6eb35af4d50458813898cc0800c85027161e26481160bd83544fa7ade222233e2b2552e00ed899e718d2241b4be30e2fefa1c97f6017aab6880ef77fad41698e45a3674f207dd3c4e96a7a364a472cedfa586ed85f268ac9e066212c063634af76f8385a50f1fd55f971d009ff009864f116e9d169aa28b4f74cacc6af1aa6fd66076657b74ddbc859a6a56ae7799714a9ff7d2582881ce2d576a5554b003480c43a6832a1af02f91a394d5606596a74e223108ad2f534d8cb211299a0d6d90c73c462c3afc5d3a45a584ee3d48e013bee43f2428dde6d75943f4623f46aa7301f1b1287d778ae0dea71e76ced9e8a5e3a4fff02ac395f1966f21b5d3381a96ac8ff337f12f489306acbcbd598b758bd6de681b96dfd81ef2028a82e66064f21856a6587b50765783b0f148376f721ed74f252e36ac7045b6f7beb571ed131d39f1ba06c3fa8c15f4c0ea1cf0aee4fb81d4964f80e6bb717a9129df23a00f0925e72280bf49025338c55dfa3f8e4df552dc3234902b76ba3b2b1e9ebb1702f01f86e88ac1271f7793c6d48bba55f820d2845e6895edee07daeaef65f5863774d8c29c317671eb8cdac72e21494340dea02f5d4ad2ea0d02f008b27034ad368ac884c38ff4fe52ba9cc8d941639c1a5ae652058a3a2eb0717f3f3a5a1950496c4371f196c27ca6dafecb06dbb74a77f5ca77b82b184c707a3666a6c813a6cac2b8c699a5c86e3ca0e7
Coverage
Product
Protection
Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
WSA
Screenshots of Detection
Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK





No comments:
Post a Comment