As part of the Subscription Services team, our Analytic Co-Pilot Service consultants worked on a variety of security use cases in Q2 2023 within our own internal environments, as well as our customers. These collaborative efforts continue to grow the library of use cases that strengthen our arsenal to help secure organizations across the globe.
This quarter, vulnerabilities were identified in well-known software where we had to quickly investigate how to monitor against such attacks. Our team looked for indicators of compromise (IOCs) for that CVE. We also researched the resulting activity to see how the threat could be monitored in a more general sense, proving better coverage for any similar vulnerabilities in the future.
In this blog we are going to look at some custom use cases around different phases of attack, from initial access and persistence, as well as lateral movement. Here’s what to expect for each use case explained below:
- Where the use case originated from, either a custom rule from our team or based upon a Knowledge Base Threat module.
- The log sources required to successfully implement a use case.
- Difficulty score to set up the use case and how complex it may be.
- Impact rating to assess how a use case can positively impact threat monitoring.
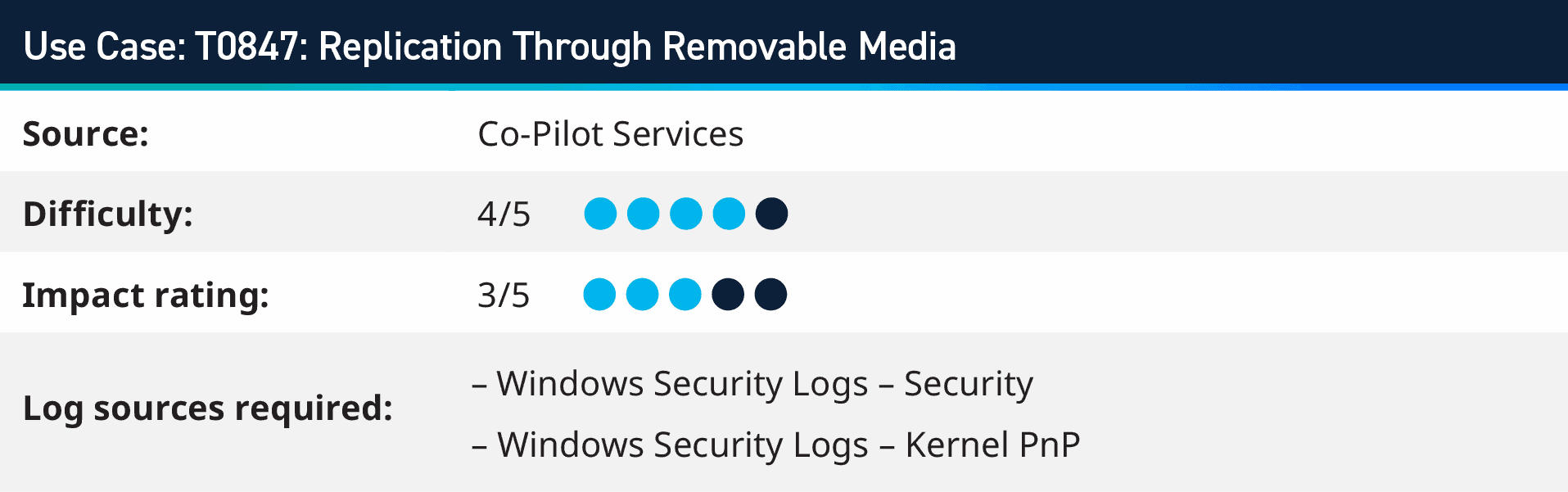
1. T0847: Replication Through Removable Media
Operational Technology (OT) and Industrial Control Systems (ICS) form the backbone of modern industrial environments, from energy grids to manufacturing plants. However, these critical systems face significant cybersecurity threats, including the risk associated with USB usage. USB drives, while convenient, can be a potent vector for malware and can result in data leakage if not appropriately managed.
A prime example of an OT/ICS compromise due to a USB is the infamous Stuxnet worm. Believed to have been developed by nation-states, Stuxnet was designed to attack specific industrial systems. It was reportedly spread via a USB drive and was responsible for causing significant damage to Iran’s nuclear program.
In the context of Windows 10 and Server 2016 operating systems, activating the “Audit PNP Activity” setting initiates a process of systematic logging. This includes recording events associated with the usage of Universal Serial Bus (USB) devices, among other related activities. By enabling this audit feature, you gain a comprehensive view of peripheral device interactions with your system, aiding in both system management and security oversight.
Once the logs are onboarded to the LogRhythm SIEM, monitoring for Event ID 400, 410 (Kernel PnP) and 6416 (Security) allows for monitoring of connected devices and information around the connected device.
2. CVE-2023-34362: Investigating the Exploitation of MOVEit Transfer Software
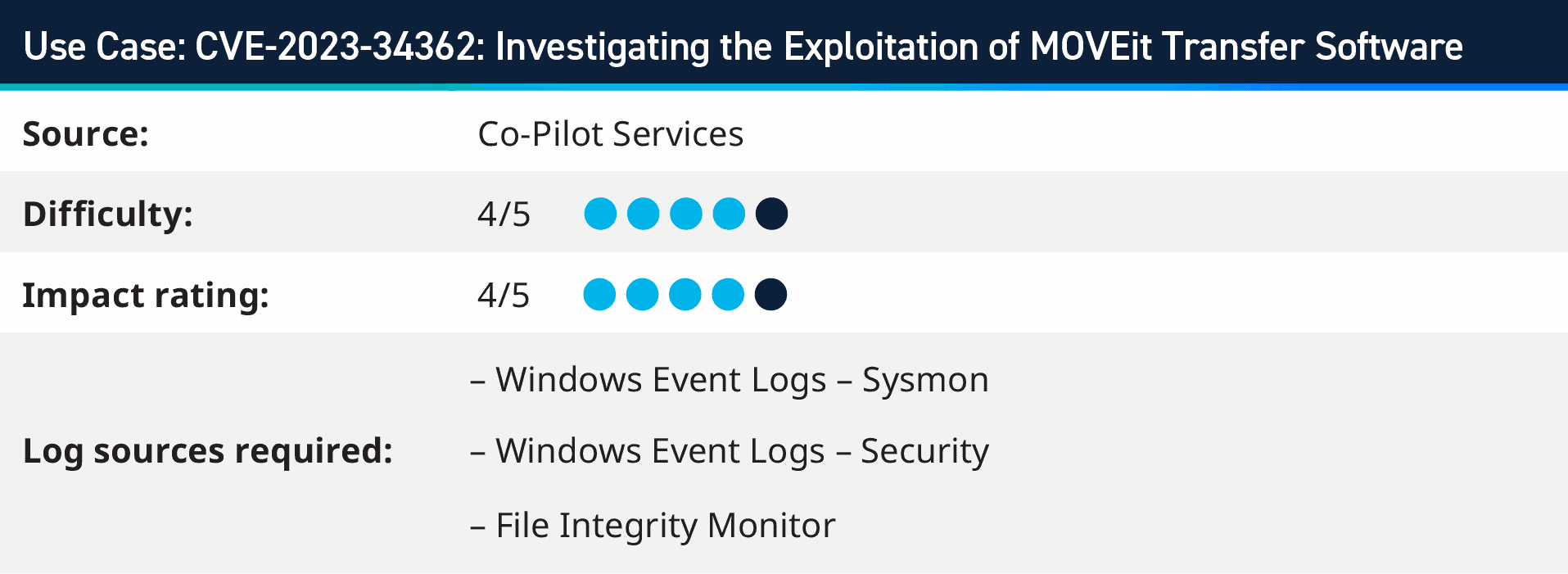
On June 1, 2023, cybersecurity firm Huntress detected an ongoing exploitation of a critical security loophole in the MOVEit Transfer software application, flagged by the software’s vendor, which progressed a day earlier. This vulnerability, later identified as CVE-2023-34362, prompted the immediate disabling of MOVEit Cloud during the investigation.
The fault appears to lie in the web application’s interface, providing potential unauthorized access to attackers.
Using AI Engine to monitor for process spawn from the w3wp.exe and MOVEit applications, we created use cases to monitor for the execution of the attack, as well as monitoring Web Server logs and File Integrity Monitoring to provide comprehensive cover of the IOCs pertaining to this vulnerability within MOVEit transfer software.

3. T1021.001: Remote Desktop Protocol: RDP Query/Enable Locally
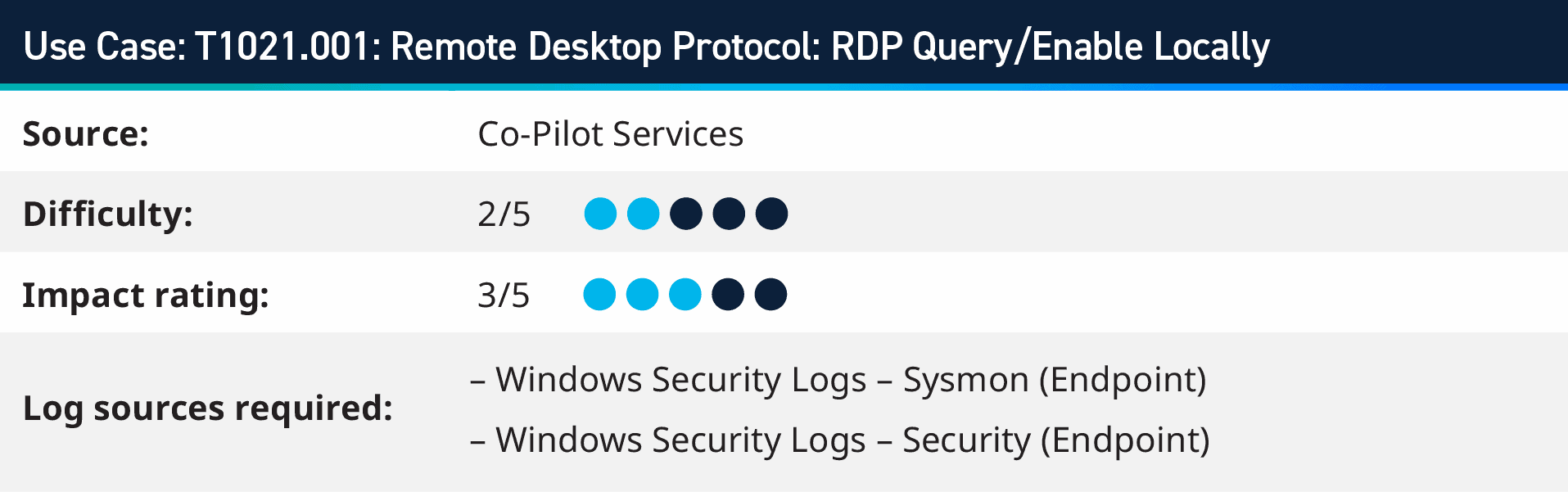
In the dynamic world of cybersecurity, adversaries are constantly seeking innovative ways to infiltrate computer systems. One such method involves using valid user accounts to exploit the Remote Desktop Protocol (RDP), a feature that enables remote access to a system’s graphical user interface.
While enabling RDP via the command line is a common task for system administrators, it’s crucial to consider the context. If an unknown or unauthorized user attempts to enable RDP, particularly in an environment where its use is uncommon or on a system where it’s typically disabled, it could signal suspicious activity.
Adversaries employ RDP with Accessibility Features or Terminal Services DLL, enabling them to maintain continued access to the system. This persistence makes it challenging for security measures to detect and eliminate the threat, underscoring the need for continuous monitoring and timely system updates.
In summary, while RDP provides valuable remote access capabilities, it can also serve as a potential entry point for adversaries. Therefore, it is crucial to ensure robust security measures, including secure credential management, continuous system monitoring, and regular updates, to mitigate the risk of unauthorized access. Always remember context is critical. Any activity that is not expected or authorized warrants further investigation.
4. T1003.001: LSASS Memory: WDigest Downgrade
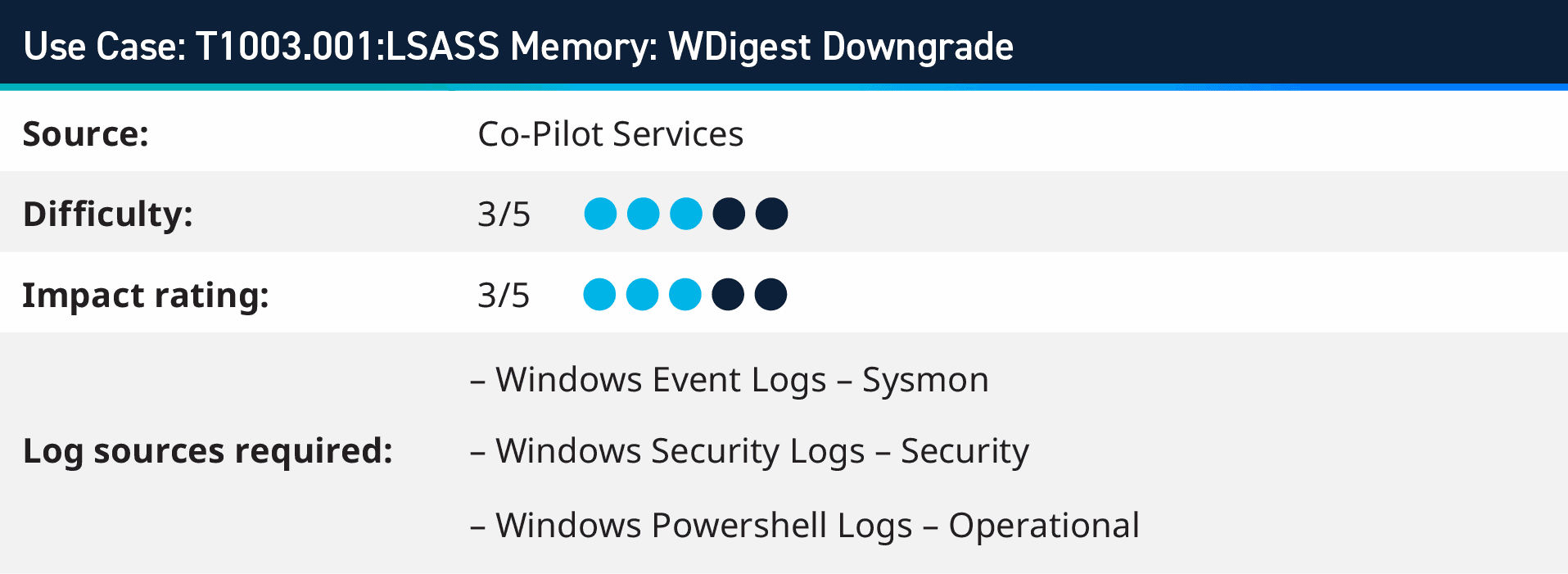
Adversaries might try to gain access to credentials held in the Local Security Authority Subsystem Service (LSASS) process memory. Once a user logs in, the system creates and stores various credential information in this location. An administrator or SYSTEM user can extract these credentials to facilitate lateral movement within the network using alternate authentication materials. Additionally, the LSASS process memory can be dumped and transferred from the target host for local analysis, adding another layer to potential attack strategies.
When a user logs on, WDigest creates a Digest Access Authentication. This process avoids sending a password in plaintext over the network by using a hash function that produces a unique “digest.” This digest is then used to authenticate the user without revealing the password. However, for WDigest to construct the digest, it must keep a copy of the plaintext password in memory. This is where the potential for misuse arises.
Red Teams/Attackers always seek ways to gain unauthorized access to systems and networks. One method is credential dumping, extracting user credentials from a system’s memory. WDigest, due to its design, can inadvertently aid in this by storing plaintext passwords in memory.
Using tools like Mimikatz, an attacker can dump these credentials and use them to escalate their privileges or move laterally within a network. They can also maintain persistence, reusing valid credentials to access resources even after initial malware or backdoors are removed.

5. T1110.003: Password Spraying
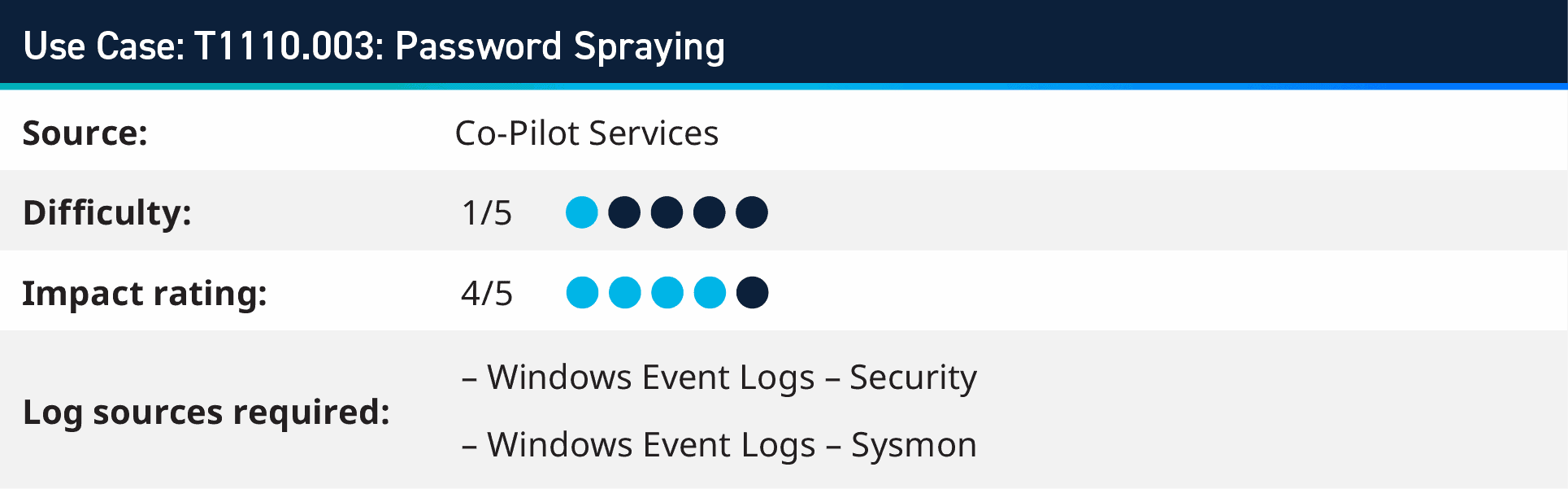
Password spraying is a technique used by cyberattackers to gain unauthorized access to systems or accounts by systematically trying a small number of commonly used passwords against a large number of user accounts. Unlike traditional brute-force attacks that target a single account with multiple password attempts, password spraying involves trying a few commonly used passwords against multiple accounts, making it less likely to trigger account lockouts or trigger security alarms.
It’s important to implement anomaly detection mechanisms that identify abnormal login behavior. By establishing baselines of typical user behaviour, any deviation from these patterns, such as a sudden surge in failed login attempts from different accounts, can indicate a password spraying attack. Among the logical rule blocks of the AI engine components is the trend rule block which could be leveraged to compare current login activity with a determined baseline to alarm on any inconsistencies with account logins.
Another technique that can be implemented to detect for password spraying is the unique rule block, by setting the unique criteria to user origin and grouping by host origin
6. T1047: Windows Management Instrumentation
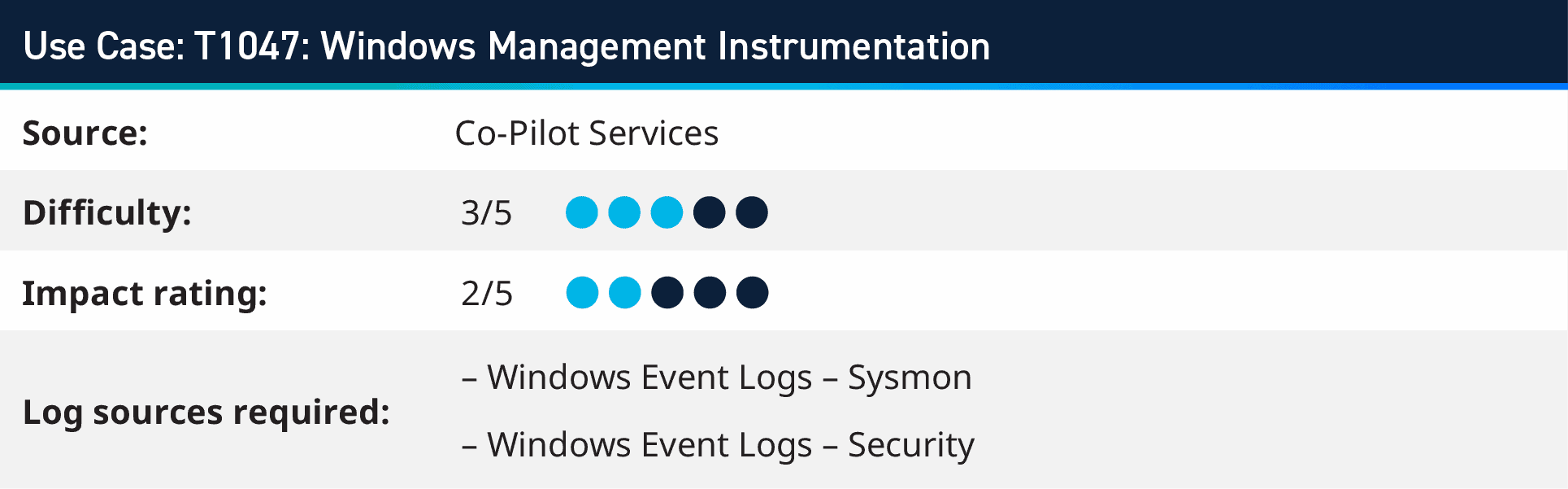
The rule is derived from Red Canary’s Global Threat Report, which ranks Windows Management Instrumentation (WMI) as the third most significant threat. WMI, an essential feature of the Windows operating system, is extensively utilized by administrators for various tasks, including system configuration, process execution, and task automation. Its capability to function on local and remote systems makes it a formidable tool for adversaries. These adversaries often exploit WMI to carry out malicious activities, which can easily be camouflaged amidst legitimate operations. The exploitation of WMI by adversaries encompasses a range of purposes, such as lateral movement across systems, gathering sensitive information, modifying system configurations, and establishing persistent access to compromised systems.
The detection rule looks for Microsoft Office applications spawning WMI processed, WMI reconnaissance activity, shadow copy deletion activity, WMI provider host spawning suspicious processed, as well as WMI related suspicious PowerShell commandlets. With this coverage of visibility, however WMI is being used nefariously, it can be picked up via the comprehensive detection techniques.
Where to Find Out More?
For customers with the Analytic Co-Pilot, Support Account Manager, or Technical Account Manager services, these use cases and others are available to download immediately within our Subscription Services Group Hub on the LogRhythm Community. Understanding that these use cases can be valuable, we do then share these to the wider Community after some time.
To glimpse over other use cases our Co-Pilot team has worked on in previous quarters, visit the following blogs below:
- Q1 2023 Analytic Co-Pilot Security Use Cases
- Q4 2022 Analytic Co-Pilot Security Use Cases
- Q3 2022 Analytic Co-Pilot Security Use Cases
- Q2 2022 Analytic Co-Pilot security Use Cases
To learn more about our Analytic Co-Pilot Services and how we can improve your threat detection and response, learn more here. If you are a customer and you have questions, reach out to your customer success manager or account team to get more information about how we can help with your use cases and analytics!
The post Q2 2023 Analytic Co-Pilot Use Cases appeared first on LogRhythm.
from LogRhythm https://bit.ly/3NSlXQK
via IFTTT
No comments:
Post a Comment