The Good | Authorities Arrest Alleged Ringleader of Major Cybercrime Organization
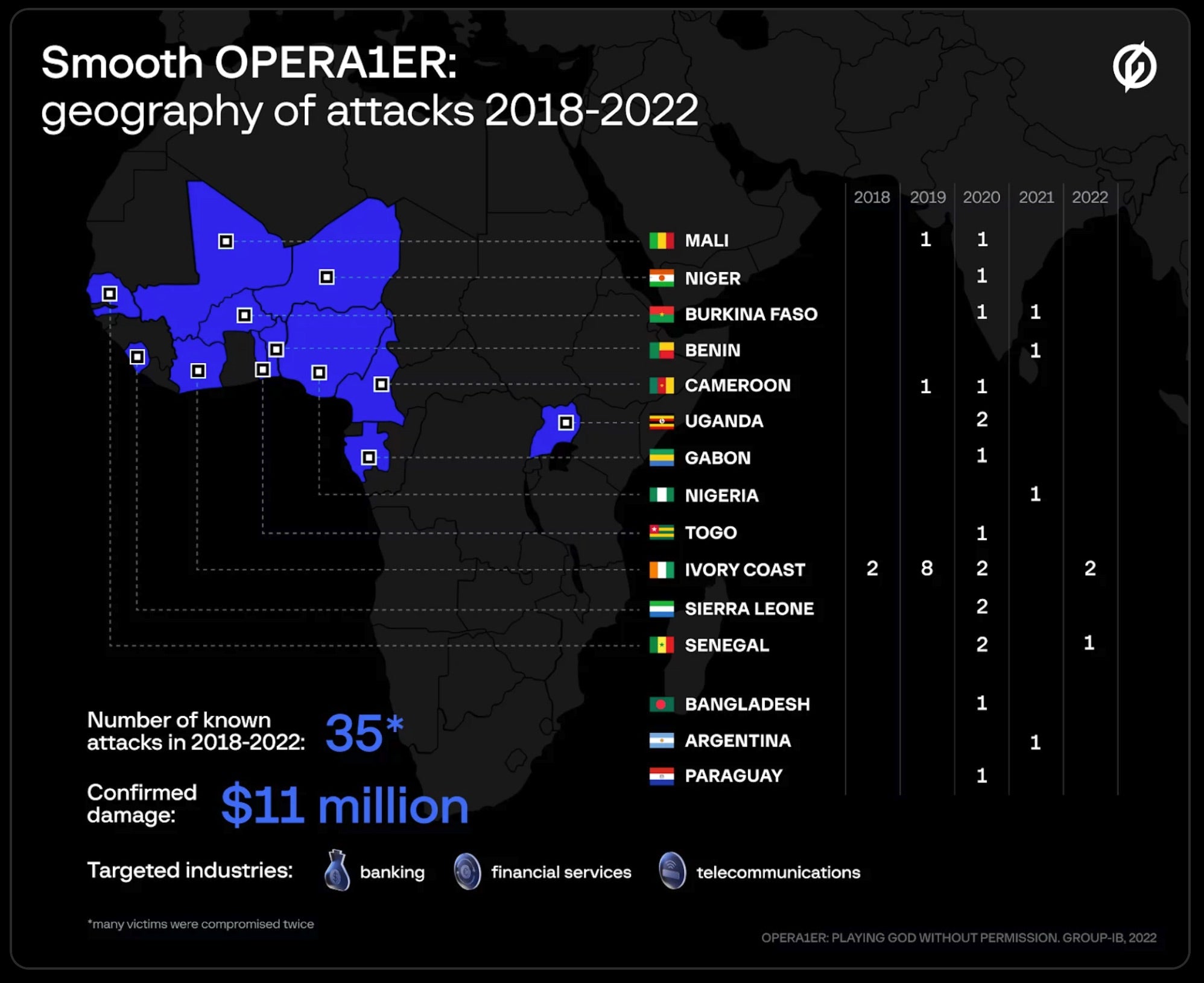
After pocketing as much as $30 million in stolen funds over the course of four years, a suspected senior member of the OPERA1ER cybercrime organization has been arrested in Cote d’Ivoire. The arrest was carried out as part of Interpol’s Operation Nervone with cooperation across local and international law enforcement agencies as well as cybersecurity researchers.
OPERA1ER, aka BlueBottle, NX$M$, DESKTOP Group, or Common Raven, is infamous for over 30 attacks spanning 15 countries in Africa, Asia, and Latin America. According to Interpol, they are a highly mature criminal organization focused on targeting financial institutions and mobile banking services with mass business email compromise (BEC) and malware campaigns.
Based on recent security findings, BEC scams continue to soar. These scams are a sophisticated form of cyber fraud where attackers impersonate legitimate business email accounts to deceive recipients and either initiate fraudulent transactions or gain unauthorized access to sensitive information. Last year alone, IC3 received over 20,000 BEC-related complaints with adjusted losses amounting to over $2.7 billion.
OPERA1ER gains an initial level of compromise through well-crafted spear phishing emails embedded with remote access trojans (RATs), keyloggers, and password stealers. Noted in previous attacks, OPERA1ER emails are in French and often reuse tax office and job hiring language. After breaking in, the group is known to use tools like Cobalt Strike and Metasploit to establish persistence.
The success of Operation Nervone is the result of extensive collaboration between various law enforcement and cybersecurity researchers Orange-CERT-CC and Group-IB, who first published a report on OPERA1ER late last year. The operation represents the importance of exchanging threat intelligence and working collectively to bring down high-profile, organized cybercrime syndicates.
The Bad | High-Severity Vulnerability In Cisco Switches Allows Attackers to Modify Encrypted Traffic
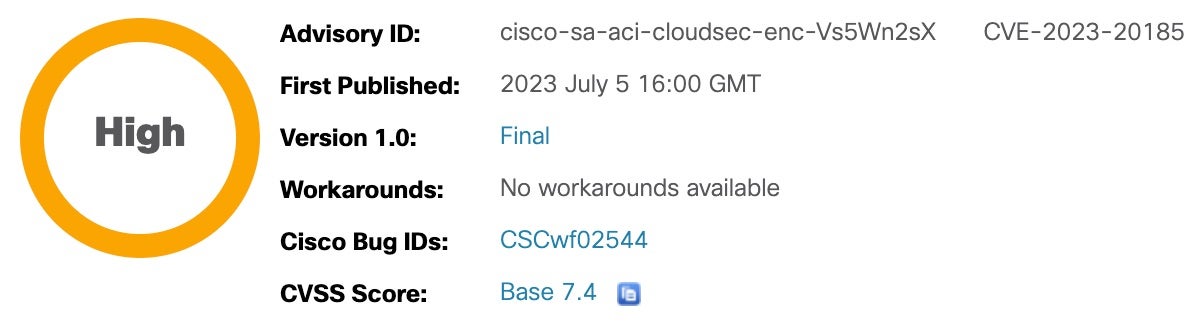
Cisco has issued a security advisory this week warning customers about a new, high severity vulnerability allowing attackers to tamper with encrypted traffic in some data center switches.
Identified as CVE-2023-20185, the vulnerability was found during internal security testing and impacts Cisco Nexus 9332C, 9354C, and 9500 spine switches equipped with a Cisco Nexus N9K-X9736C-FX Line Card, operating in application centric infrastructure (ACI) mode, running firmware 14.0 or later, and that have the CloudSec encryption feature enabled. ACI mode is most typically used in data centers for controlling both physical and virtual networks.
The vulnerability stems from an issue in the implementation of ciphers leveraged by the CloudSec encryption feature on affected switches. Exploitation of CVE-2023-20185 occurs when an attacker intercepts the traffic and uses cryptanalytic techniques to bypass encryption between two ACI sites.
If exploited, attackers can gain unauthenticated access and either read or tamper with intersite encrypted traffic between the remote sites. Further, successful exploitation enables adversaries to access data that allows them to move laterally across the compromised network.
So far, Cisco’s Product Security Incident Response Team (PSIRT) says it has no indications of active exploitation or public proof of concepts (PoCs) targeting the vulnerability. However, there are no software upgrades to address the vulnerability. This is a developing situation and customers can minimize the risks of unauthorized access and data manipulation by disabling the ACI multi-site CloudSec encryption feature immediately and contacting Cisco support to discuss alternative options.
The Ugly | BlackCat Ransomware Runs Malvertising Campaigns By Cloning Popular File Transfer App
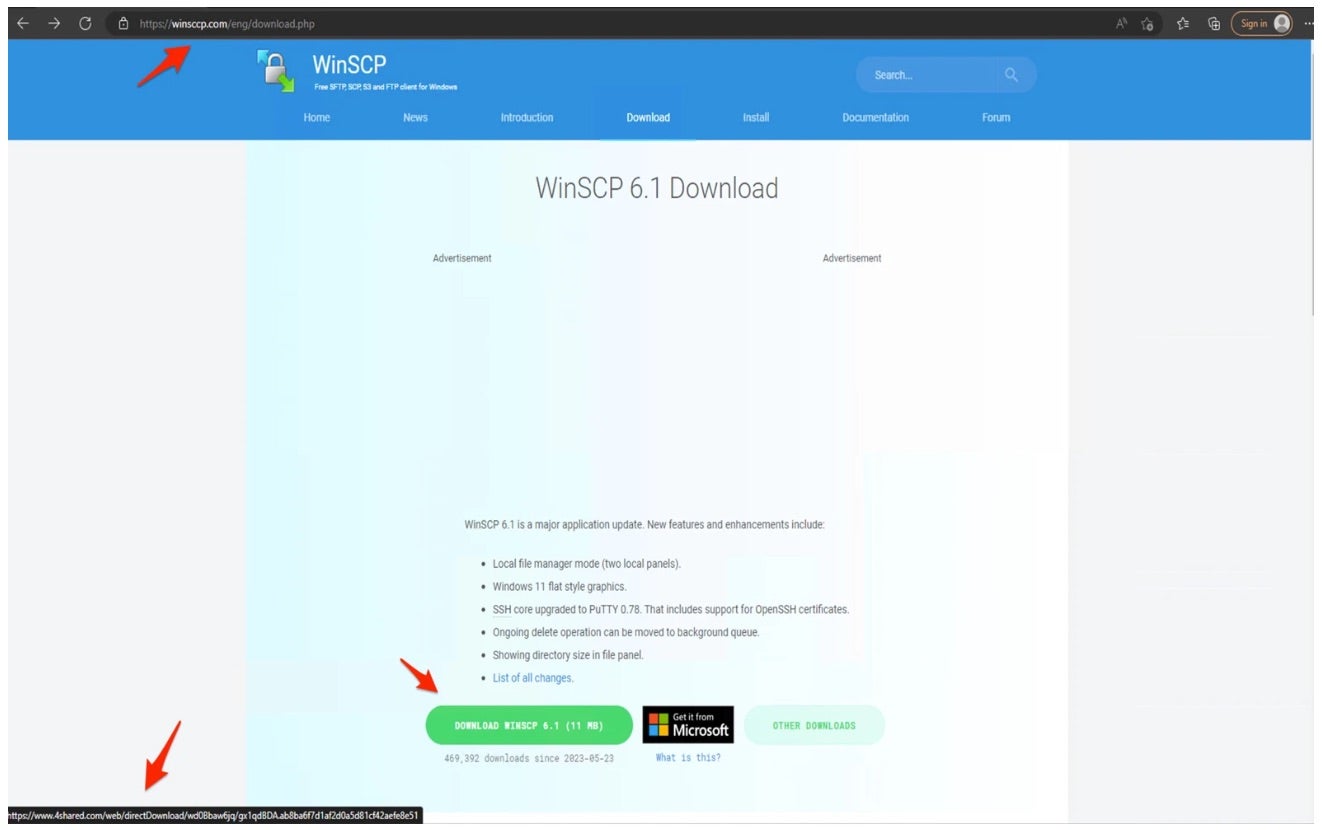
This week, cybersecurity researchers uncovered several malvertising campaigns designed to spread malware-laden installers to unsuspecting WinSCP users. WinSCP is an open-source and free SFTP, FTP, WebDAV, S3 and SCP client, and file manager for Windows that boasts over 201 million downloads and counting. The campaign has since been attributed to the notorious BlackCat ransomware group (aka ALPHV).
Malvertising (malicious advertising) is delivered through legitimate online advertising networks and platforms. These advertisements appear as regular ads on websites, but contain malicious links and code that infects users’ devices with malware. Upon interaction, users are redirected to attacker-controlled websites or prompted to download the malware. Malvertising takes advantage of the trust placed in reputable brands and advertising networks, making it difficult for users to identify the threat.
In the recent BlackCat campaigns, the group used WinSCP specifically to lure IT professionals, web and systems administrators to obtain initial access to valuable target networks. Researchers had discovered ads promoting fake WinSCP sites on both Google and Bing search pages. The spoofed WinSCP sites prompted visitors to download the app, masking behind domain names that are very similar to the real WinSCP website. Further interaction then installed a trojanized DLL file containing a Cobalt Strike beacon that connected to a C2 server.
Attacks due to malvertising continue to increase, and have recently been seen spreading a new macOS variant of Atomic Stealer, stealing AWS logins, and distributint virtualized .NET malware loaders. Businesses can prevent attacks from malvertising by using firewall control and web filters to block access to known malicious websites, implementing ad blocking software to prevent ads from being displayed, and deploying endpoint protection software to prevent and detect the execution of malicious code delivered through malicious adverts.
from SentinelOne https://bit.ly/46HikEz
via IFTTT
No comments:
Post a Comment