Leveraging known bugs and unpatched exploits continue to be an unyielding strategy for threat actors. Ranging from security bypasses and credential exposure to remote code execution, software vulnerabilities remain tools of the trade for cyber attackers looking for a way into lucrative systems.
While new flaws found in Active Directory and the MOVEit file transfer application along with those used in the AlienFox toolkit or recent IceFire ransomware campaigns have wreaked havoc this year, a number of existing vulnerabilities stand out from the rest in terms of how often they are abused to this day.
In this post, we delve into CISA’s latest round-up, which lists the top 12 most routinely exploited vulnerabilities of 2022 that continue to pose significant threats to enterprise businesses.

1. Fortinet FortiOS & FortiProxy (CVE-2018-13379)
Fortinet FortiOS SSL VPNs are primarily used in border firewalls and work by fencing off sensitive internal networks from the public internet. In the case of CVE-2018-13379, a particularly severe path traversal flaw, APT actors could use specially crafted HTTP resource requests to steal legitimate credentials and connect to unpatched VPNs and download system files. Though a patch was released back in 2019, CVE-2018-13379 has come back around several times in the past three years targeting government, commercial, and technology service networks.
In 2020, a hacker posted a list of one-line exploits to steal VPN credentials from nearly 50,000 Fortinet VPN devices using this flaw. Security researchers at the time pointed out that of the 50,000 domains, over four dozen belonged to well-known financial and government organizations. Later that year, the flaw appeared again; this time exploited by government-backed actors working to compromise US election support systems. For this campaign, CVE-2018-13379 was chained together with others to gain access to exploit Internet-exposed servers and gain access. This vulnerability was seen once more in 2021 when 87,000 sets of credentials for Fortigate SSL VPN devices were leaked online, obtained through the exploitation of CVE-2018-13379.
These critical flaws remain lucrative to threat actors who bank on Fortinet’s widespread popularity and adoption as a provider of VPN solutions. The larger the user base, the more potential targets there are, which increases the appeal for attackers. As a result of their frequent abuse, the FBI and CISA have since issued a joint advisory warning users and administrators of Fortinet against advanced persistent threat (APT) actors actively exploiting existing and future critical VPN vulnerabilities. It is highly likely that these flaws will continue to be used to gain an initial foothold in vulnerable environments as a precursor for future attacks.
For more details on this vulnerability, refer to the advisory. Fortinet has also provided steps for mitigation and prevention here.
2 – 4. Microsoft Exchange Server (CVE-2021-34473, CVE-2021-31207, CVE-2021-34523)
Microsoft Exchange Server is a popular email and support system for organizations worldwide, deployed both on-premises and in the cloud. First seen in 2021, a chain of vulnerabilities identified in unpatched on-premises editions of Microsoft Exchange Server is still actively being exploited on internet-facing servers.
This chain of vulnerabilities is known collectively as “ProxyShell” and comprises CVE-2021-34473, CVE-2021-31207, and CVE-2021-34523 to affect several versions of on-premises Microsoft Exchange Servers. ProxyShell targets unpatched Exchange servers to achieve pre-authenticated remote code execution (RCE). Out of the three, CVE-2021-34473 has the highest rated CVSS score of 9.1. While the remaining were initially classified as “exploitation less likely”, they bring significant value to attackers when used in combination with CVE-2021-34473. Together, ProxyShell allows attackers to execute arbitrary commands on vulnerable Exchange servers on port 443.
All three flaws were patched in 2021, but security researchers currently track several uncategorized threat (UNC) groups that are known to exploit ProxyShell vulnerabilities while predicting more clusters to appear as future generations of threat actors adopt working exploits. In a particular cluster of threat activity tracked as UNC2980, Mandiant researchers observed the ProxyShell vulnerabilities leveraged in a cyber espionage operation reportedly linked to Chinese-speaking actors. In this operation, UNC2980 dropped multiple tools into a US-based university’s environment after gaining access and deploying a web shell by exploiting ProxyShell. After exploitation via ProxyShell, the threat actors used publicly available tools such as Mimikatz, HTRAN, and EarthWorm to conduct post-exploitation activities.
Since its discovery, multiple intrusions leveraging ProxyShell have targeted the education, government, business services, and telecommunications industries. Microsoft’s security updates from May 2021 and June 2021 list the necessary updates that protect against ProxyShell. For more details on the vulnerability, see Microsoft’s blog post.
5. Microsoft Various Products (CVE-2022-30190)
Dubbed “Follina”, CVE-2022-30190 is a high-severity RCE vulnerability that affects multiple Microsoft Office products. Thought to be leveraged by a variety of Chinese-speaking threat actors, Follina allows the execution of arbitrary code after convincing users to open malicious Word documents or any other vector that processes URLs. Follina continues to be seen in various cyberattacks due to the large number of unpatched versions of Microsoft Office products available. It was first publicly disclosed in May of 2022:
Interesting maldoc was submitted from Belarus. It uses Word’s external link to load the HTML and then uses the “ms-msdt” scheme to execute PowerShell code.https://t.co/hTdAfHOUx3 pic.twitter.com/rVSb02ZTwt
— nao_sec (@nao_sec) May 27, 2022
Threat actors are known to exploit the Follina vulnerability through phishing scams, which use social engineering techniques to trick users into opening malicious Office documents. When users encounter embedded links within Office applications, these links are automatically fetched, triggering the execution of the Microsoft Support Diagnostic Tool (MSDT) protocol. MSDT (msdt.exe) is a Microsoft service primarily designed to collect system crash information for reporting to Microsoft support. However, threat actors can exploit this protocol by crafting links to force the execution of malicious PowerShell commands without requiring any further user interaction. This poses a serious security risk, as it allows attackers to remotely execute unauthorized commands on the targeted system through seemingly innocuous links.
The Follina flaw has more recently been exploited as a zero-day to support threat campaigns against organizations in critical industries. From March to May of 2022, an activity cluster tracked as UNC3658 exploited Follina to target the Philippine government. In April the same year, additional samples of Follina appeared in a campaign against South Asian telecommunication entities and business services by UNC3347. A third cluster dubbed UNC3819, CVE-2022-30190 was used to attack organizations in Russia and Belarus, suggesting a possible lure to content related to the illegal invasion of Ukraine.
CISA has urged Microsoft users and administrators to review Microsoft’s Guidance for CVE-2022-30190 to apply the necessary workarounds.
6. Zoho ManageEngine ADSelfService Plus (CVE-2021-40539)
In late 2021, at least nine entities across the defense, healthcare, energy, technology, and education sectors were compromised through a patched critical flaw in Zoho’s ManageEngine ADSelfService Plus. The product offers a comprehensive self-service password management and single sign-on (SSO) solution tailored for Active Directory and cloud applications. This tool is designed to allow administrators to enforce two-factor authentication (2FA) for secure application logins while granting users the ability to reset their passwords autonomously.
Tracked as CVE-2021-40539, the vulnerability enabled threat actors to gain initial access to victim organizations’ systems. CVE-2021-40539 (CVSS 9.8) is an authentication bypass vulnerability affecting REST API URLs that could be used for RCE. In response to this, CISA issued a warning against the zero-day flaw and how it could be used to deploy webshells, allowing an actor to conduct post-exploitation activities, such as stealing administrator credentials, conducting lateral movement, and exfiltrating registry hives and Active Directory (AD) files.
Vulnerabilities in SSO solutions for AD and cloud applications are particularly nefarious. Should they be successfully exploited, attackers can essentially gain access to critical applications, sensitive data, and other areas deep within the corporate network through AD.
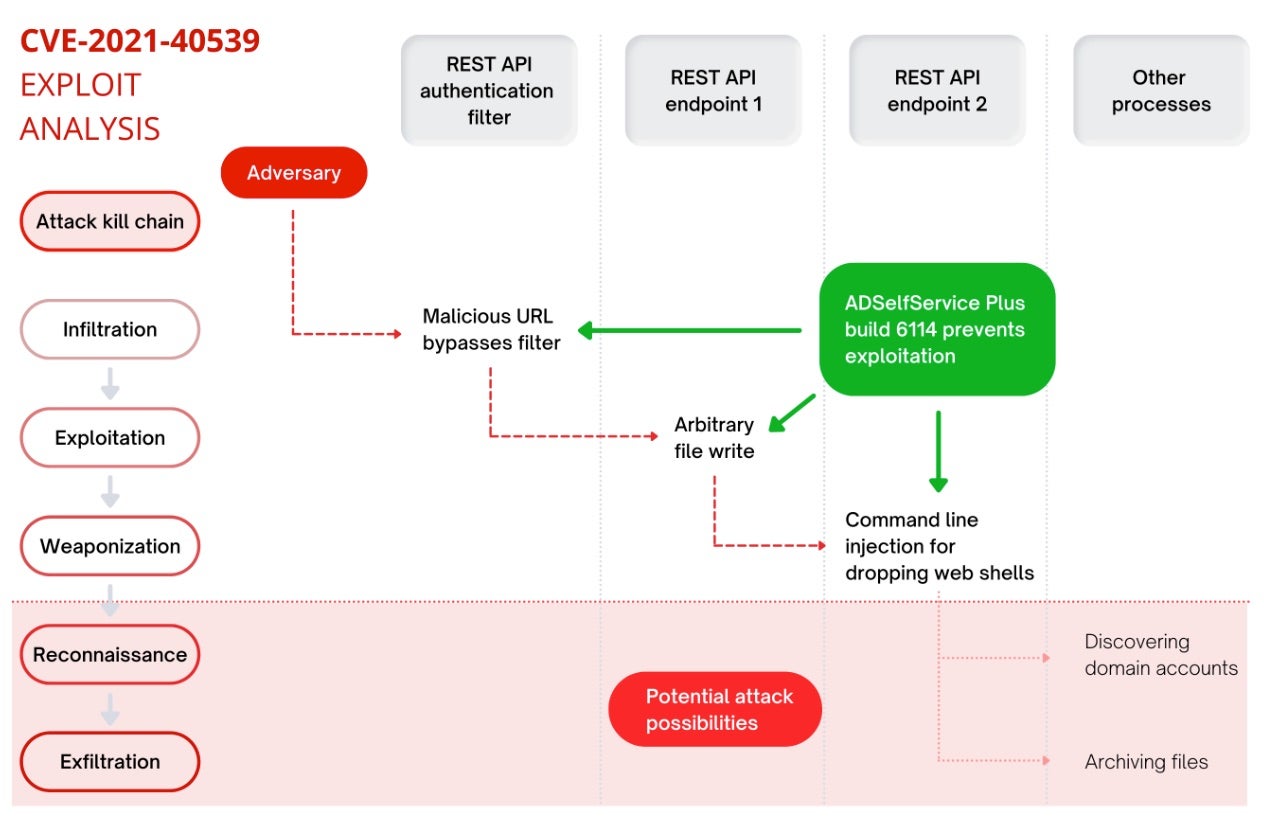
Most recently, exploitation of CVE-2021-40539 was observed in an attack against the International Committee of the Red Cross (ICRC). In their statement, Red Cross admitted to missing the critical patch that would have protected them from the exploit, highlighting the importance of maintaining a robust patch management process. As a result of the attack, the names, locations, and contact information of over 515,000 individuals part of the ICRC’s Restoring Family Links program were compromised.
Read Zoho’s advisory for more details about this vulnerability and how to update to ADSelfService Plus build 6114.
7 – 8. Atlassian Confluence Server & Data Center (CVE-2021-26084, CVE-2022-26134)
Atlassian Confluence, being a collaboration and documentation platform in use by many governments and private enterprises, continues to draw significant attention from threat actors. In CISA’s latest list of routinely exploited flaws, the Australian-based company holds two spots in the form of CVE-2021-26084 and CVE-2022-26134, which are both related to a case of Object-Graph Navigation Language (OGNL) injection.
Mass exploitation of CVE-2021-26084 first occurred in September 2021 and targeted the widely popular web-based documentation service. Confluence is designed to allow collaboration between multiple teams on shared projects. CVE-2021-26084 is a command injection vulnerability that could be exploited to execute arbitrary code on a Confluence Server or Data Center instance. Essentially having the same permissions as the user running the service, the attacker is able to execute any command, gain elevated admin privileges, and establish a foothold in the environment. CISA released an advisory guiding users and administrators to review Atlassian’s updates to prevent compromise.
Mass exploitation of Atlassian Confluence CVE-2021-26084 is ongoing and expected to accelerate. Please patch immediately if you haven’t already— this cannot wait until after the weekend.
— USCYBERCOM Cybersecurity Alert (@CNMF_CyberAlert) September 3, 2021
Just nine months later, Atlassian rolled out a warning for another OGNL injection vulnerability targeting their Confluence Server & Data Center. Tracked as CVE-2021-26134, it enables an unauthenticated attacker to execute arbitrary code in all supported versions of Confluence Data Center and Server. This critical-level flaw quickly became one of the top exploited bugs after a proof-of-concept (PoC) was released within a week of its initial disclosure. In this instance, CVE-2021-26134 was used to achieve unauthenticated RCE on the server and then drop a Behinder web shell. The Behinder web shell gave the actors very powerful capabilities such as interaction with Meterpreter and Cobalt Strike as well as memory-only web shells.
Since we posted about the Atlassian Confluence vulnerability yesterday (CVE-2022-26134), at @Volexity we have several new observations. The first is that that the targeted industries/verticals are quite widespread. This is a free-for-all where the exploitation seems coordinated.
— Steven Adair (@stevenadair) June 3, 2022
According to Atlassian’s website, the company supports 83% of Fortune 500 companies, 10 million monthly active users, and over 235,000 users in over 190 countries. The two Atlassian-based CVEs showcase how financially-motivated threat actors will continuously leverage exploits to reach many attractive targets at once.
9. Log4Shell (CVE-2021-44228)
Log4shell, assigned as CVE-2021-44228 and also known as “the Log4j vulnerability”, is a maximum severity RCE flaw found in Apache Log4j, a popular Java-based logging library used widely in various applications. This vulnerability allows remote attackers to execute arbitrary code on affected systems, potentially leading to unauthorized access, data breaches, and even full system compromise.
The vulnerability came to light in December 2021 when it was first publicly disclosed. The issue originated from the use of untrusted data in the “log4j2” component’s look-up mechanism, enabling attackers to inject malicious code through crafted log messages. This flaw exposed a wide variety of applications, including web servers, enterprise software, and cloud-based services, that all relied on Log4j for logging.
Though Apache quickly released a patch for the level 10.0-rated RCE vulnerability, security experts confirm that exploitation will be ongoing and could lead to widespread malware deployment given its broad use across major vendors. CISA has since issued a binding operational directive (BOD), ordering federal civilian executive branch (FCEB) agencies to patch their systems against this critical vulnerability.
The rapid exploitation of Log4shell is attributed to its widespread adoption across diverse industries and platforms. The Apache Log4j library has been a staple in the Java community for many years, making it present in countless applications and systems. What’s more is that patching the vulnerability has proved challenging, as many organizations struggle to identify and update all instances of Log4j within their infrastructures promptly.
See CISA’s GitHub repository for known affected products and patch information and their dedicated page containing technical details and patching guidelines for impacted organizations.
10 – 11. VMware Workspace ONE Access & Identity Manager (CVE-2022-22954, CVE-2022-22960)
VMware is a popular virtualization software, making it a frequent target for all levels of cyber attackers including advanced persistent threat (APT) groups. Exploiting vulnerabilities in VMware could grant unauthorized access to virtual machines and critical data hosted on the platform. Since VMware virtualizes multiple systems on a single physical server, a successful attack could potentially compromise multiple VMs simultaneously. Oftentimes, attackers choose to target VMware environments in order to gain a foothold in larger networks, exploiting the trust and accessibility of the virtualized infrastructure. VMware vulnerabilities take up two spots in CISA’s list of top exploited flaws this year.
First, CVE-2022-22954 (CVSS 9.8) is a server-side template injection vulnerability that could be triggered by a malicious actor with network access to achieve RCE in VMware’s Workspace ONE Access & Identity Manager. After PoCs for the vulnerability were published in spring of last year, security researchers saw it used in active attacks infecting servers with coin miners – a common first mode of attack when new flaws are exploited. VMware has published a security advisory with more details of this vulnerability here.
This is being exploited in the wild and crypto miners are being deployed#HUMINT
CVE-2022-22954#Vmware #Workspace VulnerabilitiesExpect #ransomware now/soon https://t.co/WlVy4EF9ZG
— mRr3b00t (@UK_Daniel_Card) April 13, 2022
Second, CVE-2022-22960 (CVSS ) is a privilege escalation vulnerability. According to CISA’s advisory on this vulnerability, it enables a malicious actor with local access to escalate privileges to root due to improper permissions in support scripts. If chained together with CVE-2022-22954, an actor could execute an arbitrary shell command as a VMware user and then wipe logs, escalate permissions, and move laterally to other systems with root access.
Since VMware products are used commonly across Federal Civilian Executive Branch (FCEB) agencies among other critical industries, CISA ordered an emergency directive for government agencies to complete a series of mitigation measures. These measures can be found here.
12. F5 Networks BIG-IP (CVE-2022-1388)
A few days after F5 published a patch for a critical RCE vulnerability tied to their BIG-IP suite of products last September, security researchers were able to create an exploit for the flaw. Classified as a missing authentication vulnerability, CVE-2022-1388 (CVSS 9.8) relates to an iControl REST authentication bypass that could lead to attackers gaining access and taking control of a compromised BIG-IP system. The attacker could perform a number of malicious actions such as dropping webshells for future attacks, deploying cryptocurrency miners, and exfiltrating sensitive data.
Remote code execution flaws are trivial to exploit, making them popular for targeting by opportunistic threat actors. Whenever vulnerabilities are found in internet-facing services, threat actors are sure to make quick work in leveraging them. Exploits like CVE-2022-1388 provide immediate, initial access to a targeted network and often enable attackers to follow through with lateral movement and privilege escalation; critical tactics in the cyberattack kill chain.
F5’s security advisory detailing CVE-2022-1388 indicators of compromise (IoCs) and steps for mitigation can be found here. CISA also released an advisory in response to the flaw in response to several PoCs that were published shortly after initial disclosure.
Conclusion
Enterprise security teams must acknowledge that old vulnerabilities persist and continue to pose a significant threat. While the latest CVEs often receive the spotlight, CISA’s annual list of routinely exploited vulnerabilities serves as a stark reminder that existing flaws are still capable of inflicting serious damage on vulnerable systems.
In addition to the comprehensive list, CISA offers guidance to vendors and tech organizations for identifying and mitigating potential risks. The recommendations include adopting secure-by-design practices and prioritizing patching known exploited vulnerabilities, thus minimizing the risk of compromise. Vendors are also encouraged to establish coordinated vulnerability disclosure programs, enabling root cause analysis for discovered flaws.
SentinelOne is ready to help security leaders defend their organizations against every level of cyberattack. To see how we can help you build a robust security posture, contact us today or book a demo.
from SentinelOne https://bit.ly/3DKQ3zZ
via IFTTT
No comments:
Post a Comment