Shodan is a powerful search engine that scans the web for devices connected to the internet. Shodan can help penetration testers greatly as it provides a good starting point when looking for online devices and assists in identifying potential weak points within a network.
This comprehensive guide will explore Shodan and its many features. We will explain how it works, show you how to search effectively, its use cases, and what legal implications, if any, there are.
We will also show you two examples of how to use Shodan, demonstrating its capabilities.
If you’re ready to explore Shodan, let’s begin.
What Is Shodan.io?
Shodan is a search engine that scans IP addresses for connected devices like routers, webcams, servers, and industrial control systems, identifying open ports, unsecured devices, and services running on systems. It helps identify potential entry points and vulnerabilities in these devices.
It was created by John Matherly in 2009, who described Shodan as "the world's first search engine for Internet-connected devices."
Some key features of Shodan include:
Search Filters: Shodan offers a variety of search filters that help users pinpoint specific devices, services, or vulnerabilities. This includes filtering by device type, operating system, country, port, etc.
Banner Information: Shodan collects "banner" information from devices, including details like the software version, operating system, open ports, and other metadata. This information can help identify potential vulnerabilities.
Exploit Finder: Shodan can help identify systems running software versions known to have vulnerabilities. This can be extremely valuable in preventing security breaches.
Network Mapping: With Shodan, you can identify all internet-facing assets associated with a specific IP or company. This can be crucial in understanding the full extent of an organization's potential attack surface.
Internet of Things (IoT) Device Discovery: Shodan is particularly useful for discovering Internet of Things (IoT) devices. Since many IoT devices are not securely configured by default, Shodan can help identify these potential security risks.
The intended usage of Shodan is to help penetration testers in mapping an organization's internet-facing assets and identify vulnerabilities such as open ports or outdated software.
Shodan aids in improving system security by highlighting and addressing these vulnerabilities.
How Does Shodan.io Work?
Shodan operates somewhat like Google in that it searches the web, but instead of indexing website content, it scans the entire internet for devices with open ports. When it finds these open ports, it captures information about the services running on them – a process known as "banner grabbing."
Shodan then organizes this data into a searchable database. Users can utilize various search queries or filters to locate specific services, devices, or vulnerabilities.
Getting Started With Shodan.io
Now that you understand what Shodan is and how it works, we will show you how to create an account and get started.
Your first step is to head to the Shodan register page and sign up for an account.
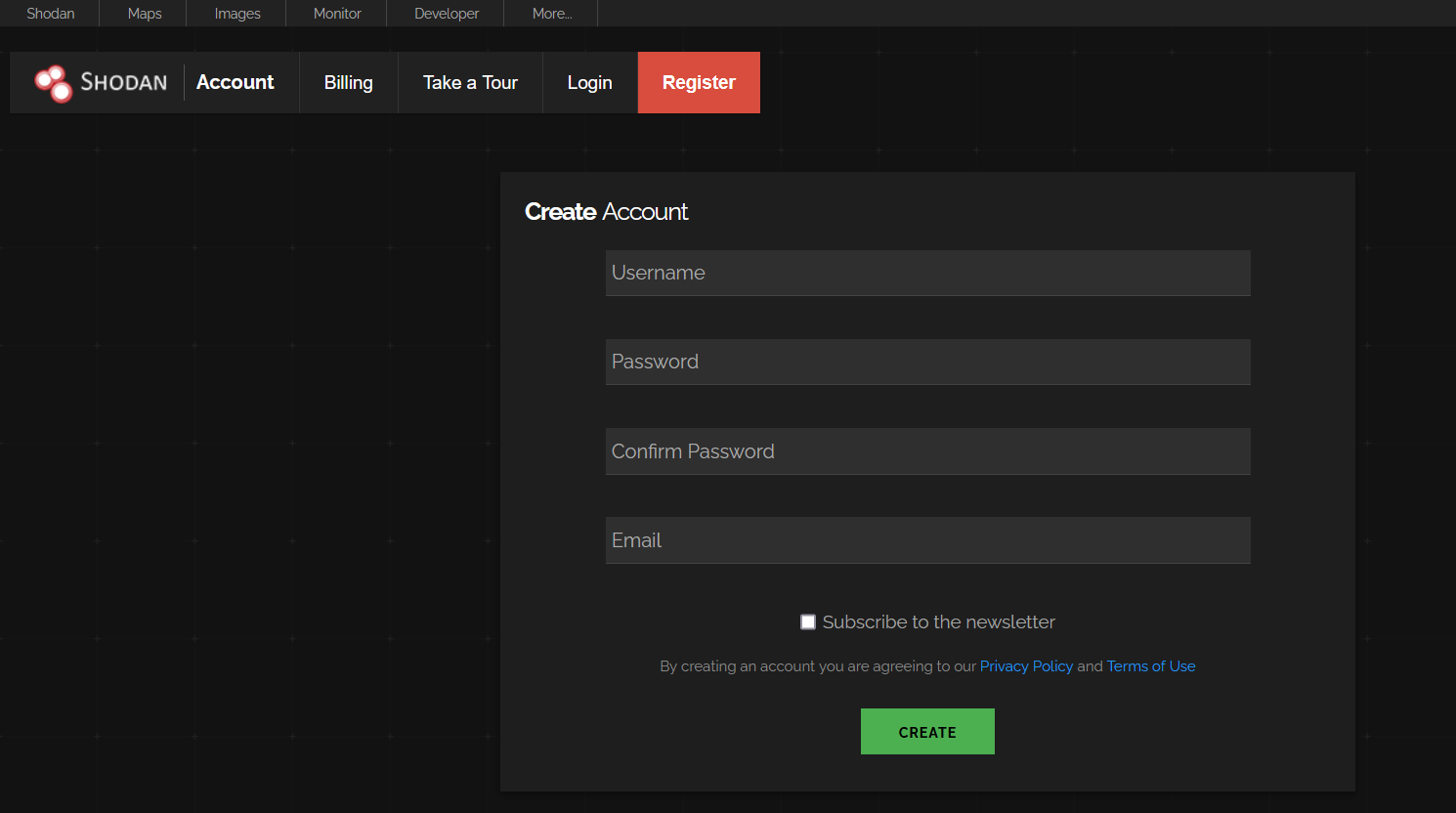
Once you’ve created an account, you should receive an email with an activation link to verify your account.
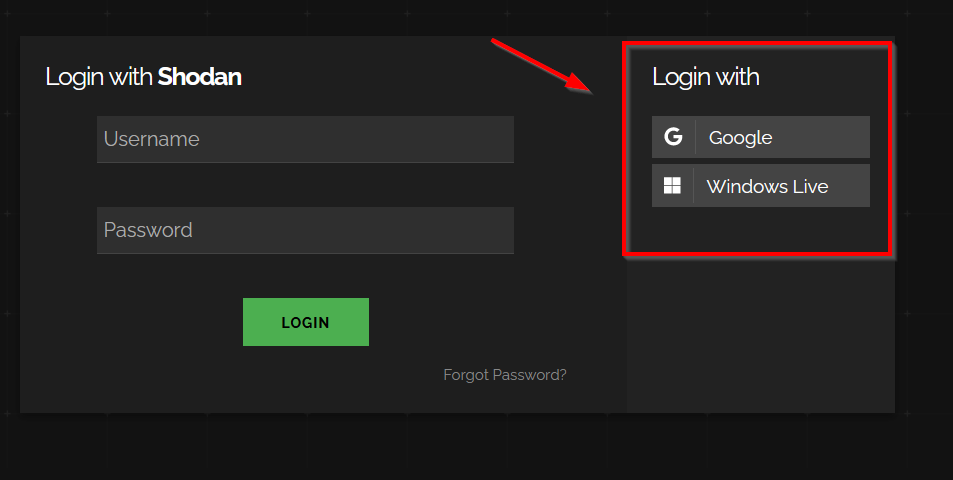
Once that’s done, you can proceed to log in. If you signed up for an account with an email from Google or Windows, you can use the SSO (single sign-on) method.
The Shodan dashboard is your central hub for navigating and utilizing the powerful features of Shodan. It's where you can enter search queries, apply filters, and read the documentation on the many features of Shodan.
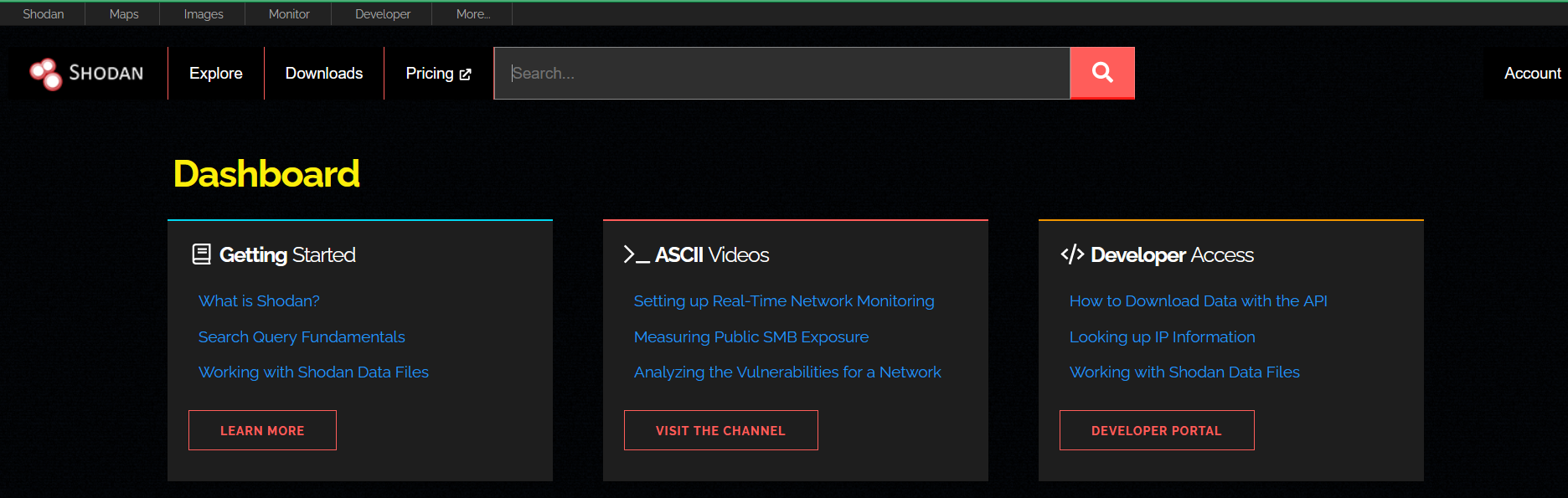
A few main features include:
Maps
You can view maps (paid feature), which allows you to explore search results visually. It displays up to 1,000 results at a time, and as you zoom in/out, Maps adjusts the search query only to show results for the area you're looking at. All search filters for the main Shodan website also work on Maps.
Images
Shodan Images is a user-friendly interface around the “has_screenshot filter” and is one of the services included with the Shodan Membership. It provides a quick way to browse all the screenshots that Shodan collects.
Explore
This section on Shodan provides you with a showcase of trending and popular searches. It includes categories such as “Industrial Control Systems,” “Databases,” “Network Infrastructure,” and “Video Games.”
Shodan gives every account, whether free or paid, an API key that can be found under the “Account” tab.
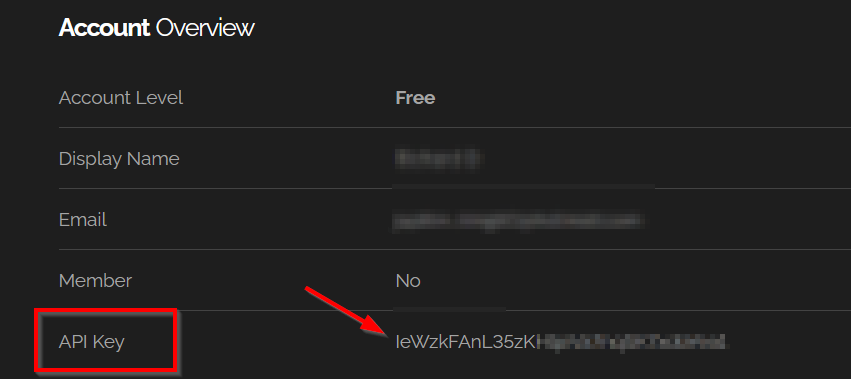
Shodan has two APIs. The REST API is the one you will be primarily using lets you search for specific data and get summaries. The Streaming API gives a live feed of data as Shodan collects it, but you can't search this data - it's for large-scale use.
Shodan.io Search Syntax and Operators
Now, we will show you some examples of Shodan search queries and filters and how to make the best use of these.
Basic Search Examples
| apache | This search will return servers running Apache software. |
| Microsoft-IIS/7.5 | This will return servers running version 7.5 of Microsoft's Internet Information Services web server software. |
| nginx | This will return servers running Nginx, a popular open-source web server. |
| cisco-ios | This will return devices running Cisco's IOS operating system, often used in networking hardware like routers and switches. |
| default password | This might show devices or services where default passwords are still used. |
Filters
| ip: | Filters results by a specific IP address.Ex: ip:192.168.2.1 |
| asn: | Filters results by a specific ASN (Autonomous System Number) ID.Ex: asn:AS8160 |
| hostname: | Filters results by a specific hostname or find values that match the hostname.Ex: hostname:google.com |
| port: | Filters results by a specific port number of a service or find particular ports that are open.Ex: port:21 |
| net: | Filters results from a specified CIDR (Classless Inter-Domain Routing) block.Ex: net:192.0.2.0/24 |
| isp: | Filters results by devices assigned a particular address (space) from a specified ISP (Internet Service Provider).Ex: isp:Bell |
| city: | Filters results by a specific city or find devices in a particular city.Ex: city:Vancouver |
| country: | Filters results by a specific two-digit country code or find devices in a particular country.Ex: country:CA |
| os: | Filters results by a particular operating system or search based on the operating system.Ex: os:Linux |
| product: | Filters results by a particular software or product identified in the banner.Ex: product:Apache |
| version: | Filters results by a specified software version.Ex: version:2.2.5 |
| geo: | Search for specific GPS coordinates.Ex: geo:42.3601,-71.0589 (command line only) |
| before/after: | Find results within a specific timeframe.Ex: after:2022-01-01 (command line only) |
Let’s combine some filters to effectively use search queries and show you how this can be leveraged as an important tool when testing.
product:"Apache" os:"Linux" port:"80" country:"US": This query identifies Apache servers running on Linux systems with an open port 80, specifically located in the US. It could help identify potentially exploitable systems.
product:"nginx" version:"1.14.0": This query is used to find nginx servers with version 1.14.0. This suggests these systems may have known vulnerabilities associated with that version of nginx.
os:"Windows XP" city:"New York" port:"445": This query targets systems running the outdated Windows XP OS in New York City with open port 445, often associated with potentially exploitable SMB vulnerabilities.
ip:192.168.1.1 product:"Apache" port:80: This query inspects a specific IP address, checking if it's running an Apache server on port 80, potentially revealing points of entry.
ip:192.168.1.1 os:"Linux": This query examines a particular IP address to see if it runs a Linux OS.
Shodan Through CLI
Shodan can also be used from the command line. We will show you a quick install of this on Kali and its basic usage.
To install Shodan, use the following command:
pip install shodan
Next, you need to activate your API key to use the REST API with the following:
shodan init <API Key>

Once everything is ready, you can run shodan in the command line to see a list of available commands.
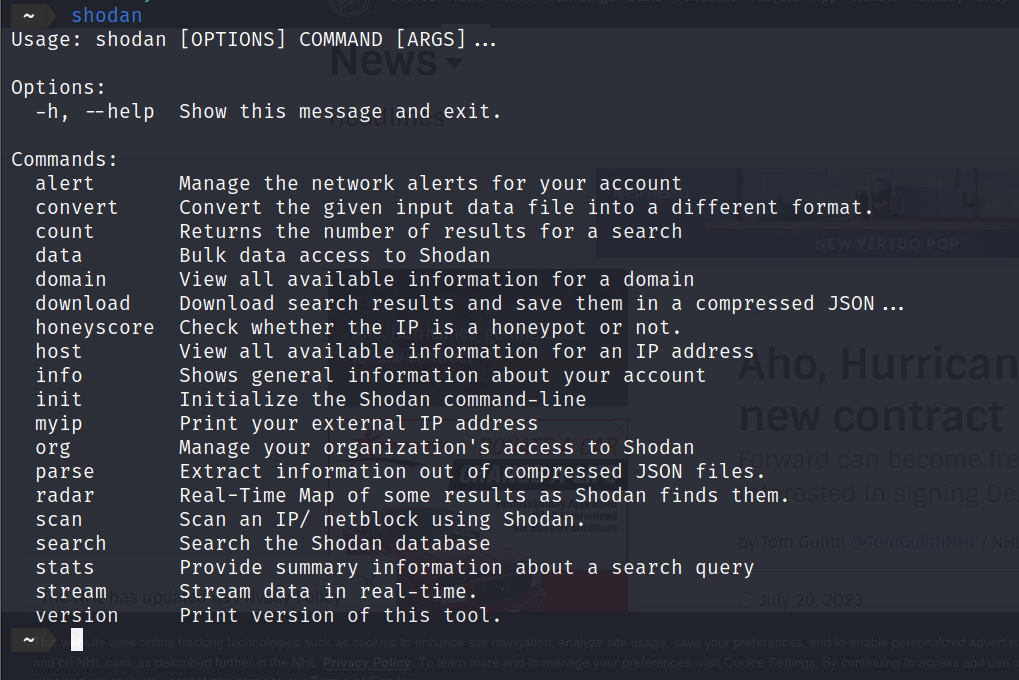
Here is a breakdown of what some of the commands do. Some of them require a paid account.
shodan search <query>: Searches Shodan for a specified query.
shodan host <ip address>: Shows all information about the host with the specified IP address.
shodan count <query>: Returns the total number of results the query would return.
shodan download <filename> <query>: Download search results and save them into a zipped json file for offline analysis.
shodan scan submit <ip>: Send a request to Shodan to crawl an IP or netblock.
Using Shodan
As a penetration tester, using Shodan can be incredibly helpful as it allows you to find more information about your client's internet-facing assets. It reveals open ports, operating systems, and services on each connected device and can help identify potential vulnerabilities.
Here are some of the devices and services that can be found using Shodan.
- Routers and Switches: Shodan can identify these devices, which form the backbone of most networks, and provide information on open ports and potential vulnerabilities.
- Servers: Web, email, database, FTP, DNS, and various other types of servers can be discovered and further examined for security issues.
- Webcams and Security Cameras: If improperly configured or secured, these devices can be a privacy risk and thus are important to discover during a penetration test.
- Firewalls and Intrusion Detection Systems: Gaining information about these security devices can be critical to a penetration tester's understanding of a network's defenses.
- Printers: Network printers can be an overlooked security risk and sometimes be used as a pivot point within a network.
- VoIP Phones: If not properly secured, voice-over IP phones can allow an attacker to listen in on calls or use the device to gain further access to a network.
- Smart Devices: This includes IoT devices like smart thermostats, lights, refrigerators, etc. These devices are increasingly common and often lack robust security, making them an important part of a penetration test.
- Industrial Control Systems: For penetration testers working with manufacturing or utility companies, discovering and testing the security of ICS devices like PLCs (Programmable Logic Controllers) can be critical.
- RDP Information: Remote Desktop Protocol (RDP) is commonly used in business environments. Shodan can detect RDP services and potentially insecure configurations.
- Default Credentials: Some internet devices still use their default usernames and passwords. Shodan can help identify these devices.
- Exposed Databases: Shodan can detect databases directly accessible online, such as MongoDB or Elasticsearch instances, which may reveal sensitive data if not properly secured.
- SMB Access: Shodan can reveal devices where the Server Message Block (SMB) protocol is being used, potentially without proper security configurations or authentication measures.
Next, we'll demonstrate a couple of examples of how to search for specific vulnerabilities using Shodan. We'll focus on two scenarios: searching for SMB vulnerabilities and identifying open RDP(Remote Desktop Protocol) ports.
SMB
We'll use a few search filters together to narrow our results for our Shodan query. The goal is to find devices that have port 445 open (which means they're likely using SMB), do not require authentication (meaning they're potentially vulnerable), are located in Canada, and contain the term "Documents." By combining these filters, we're narrowing the results to specific devices that meet our criteria.
Here is the query:
port:"445" Authentication: "disabled" country:"CA" "Documents"

From the results of our query, we've identified a potentially vulnerable SMB with numerous exposed folders. Not only does it reveal the SMB version, but it also tells us that it's likely vulnerable to remote code execution. As a penetration tester, this information can be extremely helpful. This information allows a penetration tester to plan the next steps of attack.
RDP
Next, we'll formulate a search query to identify open RDP ports running Windows RDP. Suppose we're conducting work for a client, and we want to leverage Shodan to determine if RDP is enabled and gather any other pertinent information it may provide. In this case, we could employ the following search query.
ip:"<IP>" "\x03\x00\x00\x0b\x06\xd0\x00\x00\x124\x00" has_screenshot:true
This Shodan query is searching for a specific IP address where the response includes the hexadecimal string "\x03\x00\x00\x0b\x06\xd0\x00\x00\x124\x00", which is typically associated with an open Windows Remote Desktop Protocol (RDP) connection. The 'has_screenshot: true' filter only shows results where Shodan has a screenshot.
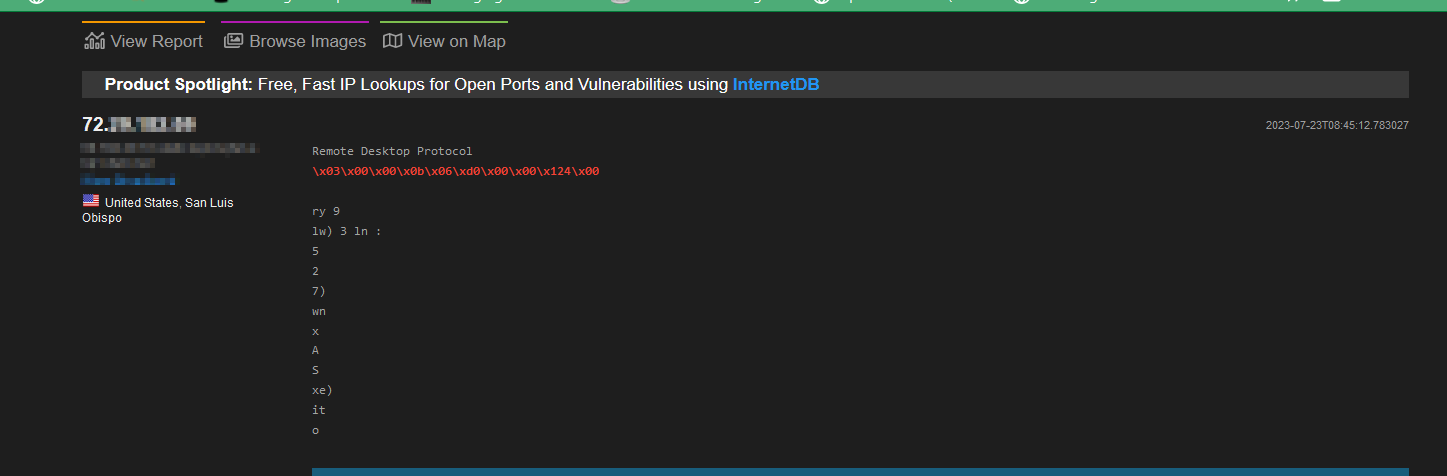
From our search, we have found that our target seems to have RDP open. Let’s look at the screenshot provided by Shodan for more information.
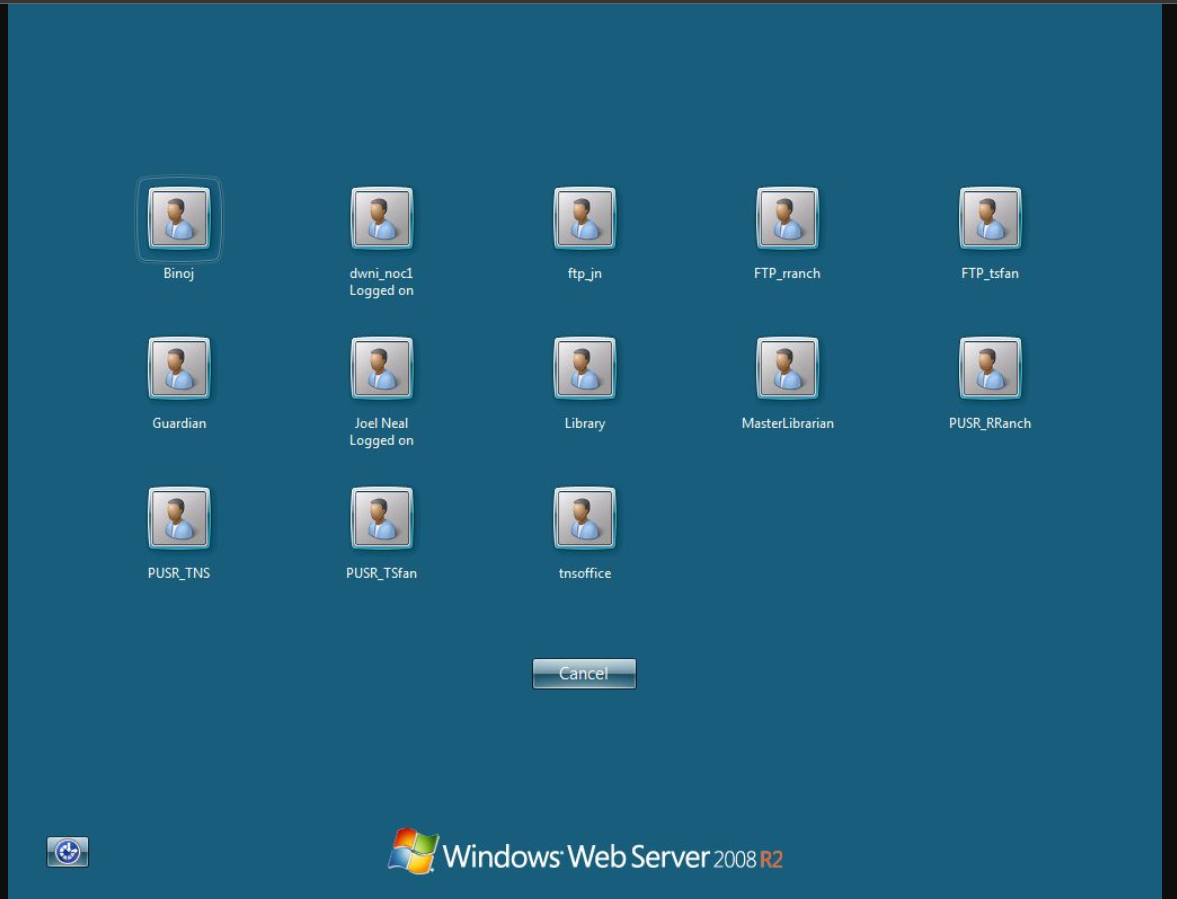
As you can see in the screenshot, we are presented with numerous usernames. These could be utilized in subsequent stages of our testing—for instance, in a password spraying attack.
See our article “Penetration Testing Steps: A Comprehensive Assessment Guide” for more information on the steps involved in a penetration test.
Shodan Use Cases
As you’ve seen, Shodan can be a great tool for locating potential SMB vulnerabilities and open RDP ports. But what other use cases does it have regarding cyber security?
Shodan can be used to:
- Gather Infomation for Reconnaissance: As a penetration tester, Shodan can be a great tool in the reconnaissance phase. It can provide a wealth of information about a target, from the devices and services they use to their locations, the network structure, exposed databases, and more. This information can be instrumental in planning and executing a penetration test.
- Monitor Emerging Threats and Trends: Shodan can provide real-time information about new devices or services on the internet. This can help penetration testers, and security analysts keep track of emerging threats and vulnerable systems.
- Evaluate Global Device and Service Exposure: Shodan's global reach allows penetration testers to evaluate the exposure of devices and services worldwide. This can help understand global trends, identify regions with high concentrations of vulnerable devices, and plan penetration testing strategies accordingly.
- Monitor Assets: For security analysts, or SOC teams, Shodan can continuously monitor their organization’s assets. This includes identifying new devices connected to their network, detecting unexpected changes, uncovering insecure configurations, and tracking their exposure to potential cyber threats.
Paid Featured
Shodan offers different paid plans, which offer other benefits. These benefits include a higher number of search and scan credits. An increase in monitored IP addresses, search pages, and search filters allowed.
Shodan offers a variety of pricing plans to suit different needs and budgets. These include a one-time payment option of $49 and monthly subscription plans priced at $69, $359, and $1099 monthly.
Legal Implications of Using Shodan
Shodan is generally considered legal and ethical for passive reconnaissance during a penetration test, it’s a search engine that gathers publicly available information about a target.
However, improper interaction with a target system without proper authorization can lead to illegal activities like exploiting vulnerabilities, attempting to access systems, or launching attacks.
These activities are illegal under the Computer Fraud and Abuse Act (CFAA) in the US, the Police and Justice Act in the UK, section 342.1(1) of the Criminal Code of Canada (Unauthorized Use of Computer), and similar laws in other countries.
As a penetration tester, it is crucial to obtain explicit permission before testing vulnerabilities or attempting to gain access. This typically involves a clear contract or written agreement outlining the scope and limits of the testing activities.
See our article “Is Hacking Illegal? The Law and Ethical Perspectives” for a more detailed explanation.
Conclusion
You should have a better understanding of how to use Shodan. As you’ve seen, Shodan can be an incredibly powerful tool. Enabling penetration testers to search the internet for various devices, services, and potential vulnerabilities.
From discovering exposed databases or systems running outdated software, to identifying open ports and insecure configurations, Shodan provides invaluable insights for a comprehensive penetration test.
Crafting precise search queries and understanding the results is key to effectively using Shodan. Always use this tool responsibly and within your role's legal boundaries.
Happy hunting!
Frequently Asked Questions
Hackers use Shodan to identify vulnerable systems, discover exposed databases or infrastructure, and gain insights about specific targets. They may search for servers running outdated software with known vulnerabilities or look for open ports that provide opportunities for unauthorized access.
Shodan is legal because it is a legitimate search engine that indexes publicly available information from various devices and networks. Shodan simply scans the internet to gather information that is already openly accessible.
If they're online, Shodan can find any device connected to the internet, such as servers, webcams, smart TVs, routers, traffic lights, IoT devices, and even refrigerators.
Shodan is a search engine, although instead of indexing websites like Google, it scans the web for devices and provides detailed information about them, such as their operating system, open ports, services running, software versions, and even default passwords in some cases.
Shodan will show vulnerabilities in search results. However, to search for specific vulnerabilities, you must be on a small business plan or higher.
Shodan is a passive tool as it does not actively interact with systems but collects and presents data from these publicly available assets.
from StationX https://bit.ly/45vdDw9
via IFTTT



No comments:
Post a Comment