SentinelOne is thrilled to announce general availability (GA) of the integration between our real-time, AI-powered cloud workload protection platform (CWPP) with Snyk Container. The integration and partnership helps cloud security practitioners, AppSec, and developers more seamlessly collaborate to streamline triage, stop the spread of security incidents for containerized workloads, and solve root cause of issues impacting production back in application source code.

Overview
When Singularity Cloud Workload Security, the real-time CWPP from SentinelOne, detects a runtime threat to a containerized workload running on cloud infrastructure, the threat details are automatically enriched with relevant context from Snyk Container about known vulnerabilities in the application code.
These vulnerability details are ingested from Snyk Container into the SentinelOne’s Singularity Data Lake in one of 2 ways: (1) via an API call to Snyk upon the runtime threat detection, and (2) optionally at a pre-defined cadence set by the customer.
By consolidating cloud security data from build and runtime, customers are better equipped to accelerate investigation and response. No more data silos, no more context switching, no more copy and paste. Instead, powerful context resides in one convenient location. Through the integration, our mutual customers can now:
- Automatically correlate runtime threats to known container image vulnerabilities
- Easily notify the source code owner
- Better prioritize and fix source code vulnerabilities impacting production operations
- Facilitate remediation of runtime issues at the workload source code
Getting Started
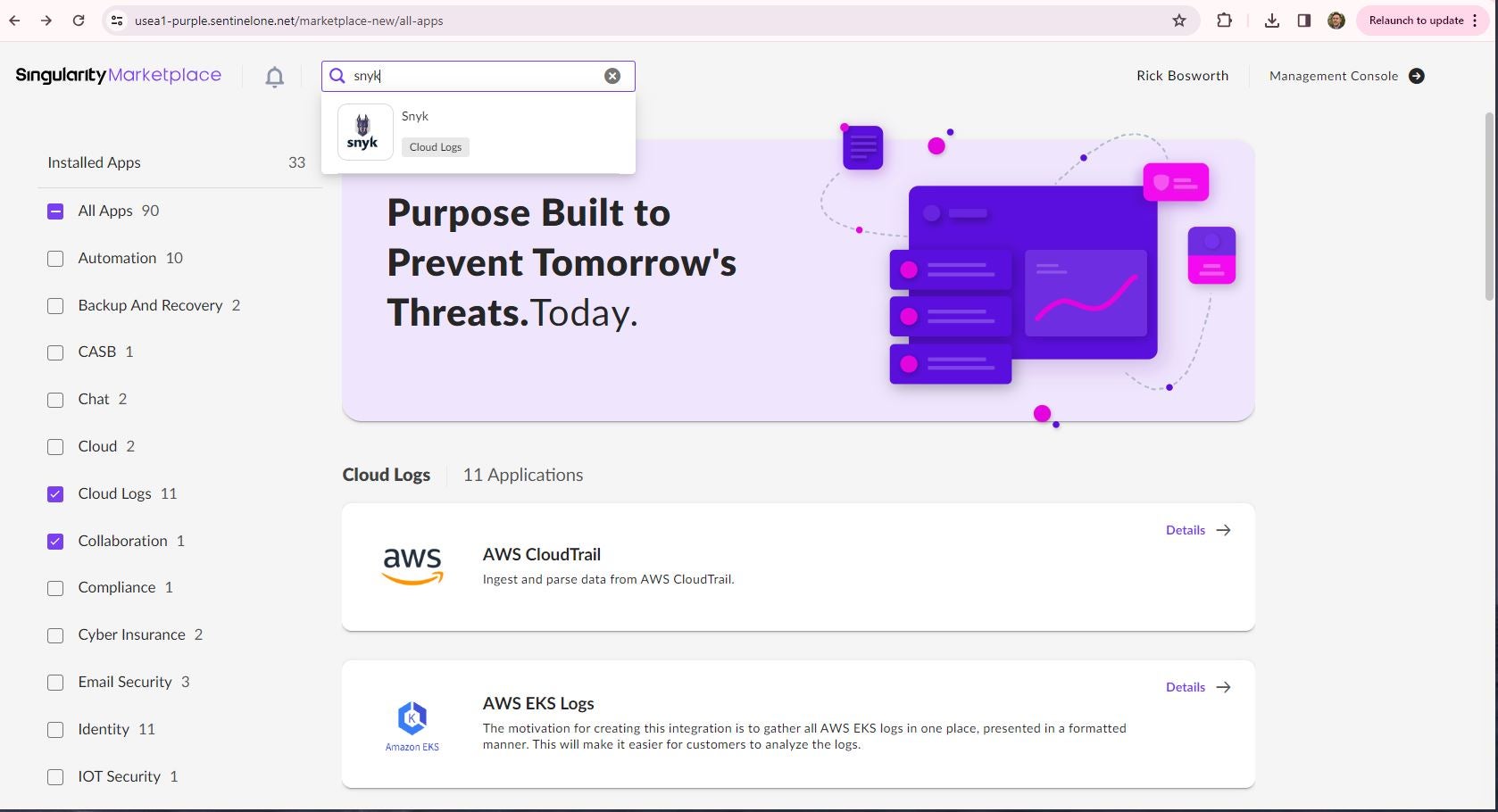
Phase 1 of the integration, in which runtime threat detections from SentinelOne are enriched with software vulnerabilities identified by Snyk, is available today to mutual customers. To get started, SentinelOne customers can navigate to the Singularity Marketplace from within the management console and search for Snyk.
As shown in Figure 1, select the Snyk app and install. This integration app will pull vulnerability details from the Snyk client into the Singularity Data Lake. Initial setup documentation can be found in the Knowledge Base document here.
The Value of Combining Runtime and Built Time Context
Knowing which workload vulnerabilities to fix first is a challenge. Keeping container images free of vulnerabilities can be difficult, as developers often lack visibility into the severity and associated risks of build-time vulnerabilities. Although users of Singularity Cloud Workload Security have visibility into container threats at runtime, they lack context about the vulnerabilities in container images, sometimes not even knowing who owns the workload’s source code. Without this build-time context, identifying the root cause of these threats can be difficult and time-consuming.
Solving the vulnerabilities at the source, in the source code, is ideal, as this prevents recurrence.
By enriching runtime threat detections from SentinelOne with vulnerabilities in the workload image identified by Snyk, cloud security, AppSec, and developers can collaborate better. They are better equipped to make informed decisions, put critical issues first, and better manage risk.
The enrichment of runtime threats with build-time context helps streamline triage, stop the spread, and solve issues impacting production right back at the source code.
Example: Runtime Threat, Build Time Context
In our example, we are running a container on a Kubernetes worker node. This node is part of a k8s cluster deployed on our managed k8s service, Amazon Elastic Kubernetes Service. Singularity Cloud Workload Security for Kubernetes has detected a runtime threat affecting our example containerized workload. More specifically, and as shown in Figure 2, both the Application Control and Behavioral AI Engines on the SentinelOne CWPP agent have triggered on a curl command.
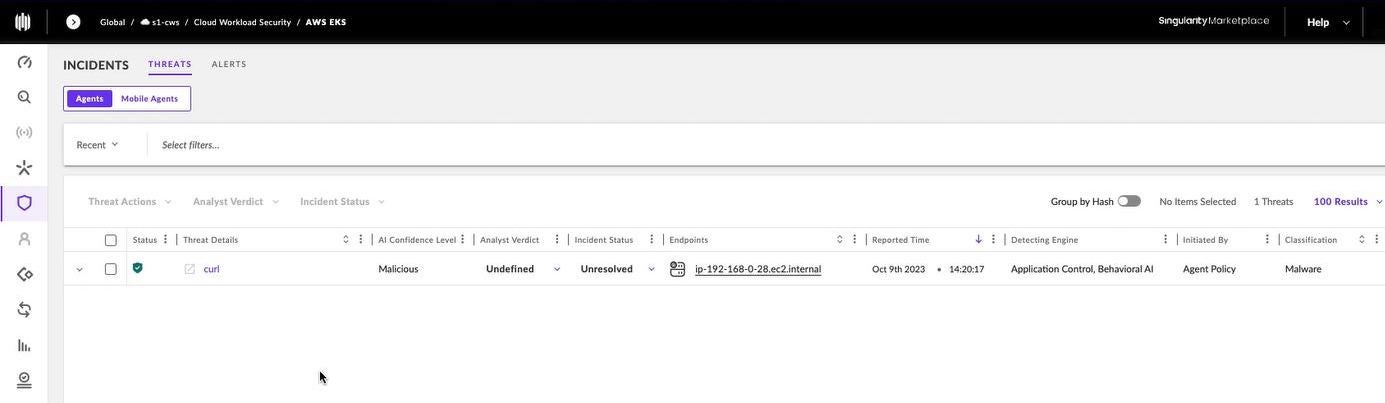
After clicking into the incident for more detail, the user is presented with the details shown in Figure 3. Here we see that the CWPP agent has automatically assembled details relating to the threat indicators mapped to the MITRE ATT&CK TTPs, information on the Amazon EC2 instance which is running the container, as well as k8s context including container image information such as registry, repo, labels, and container ID.
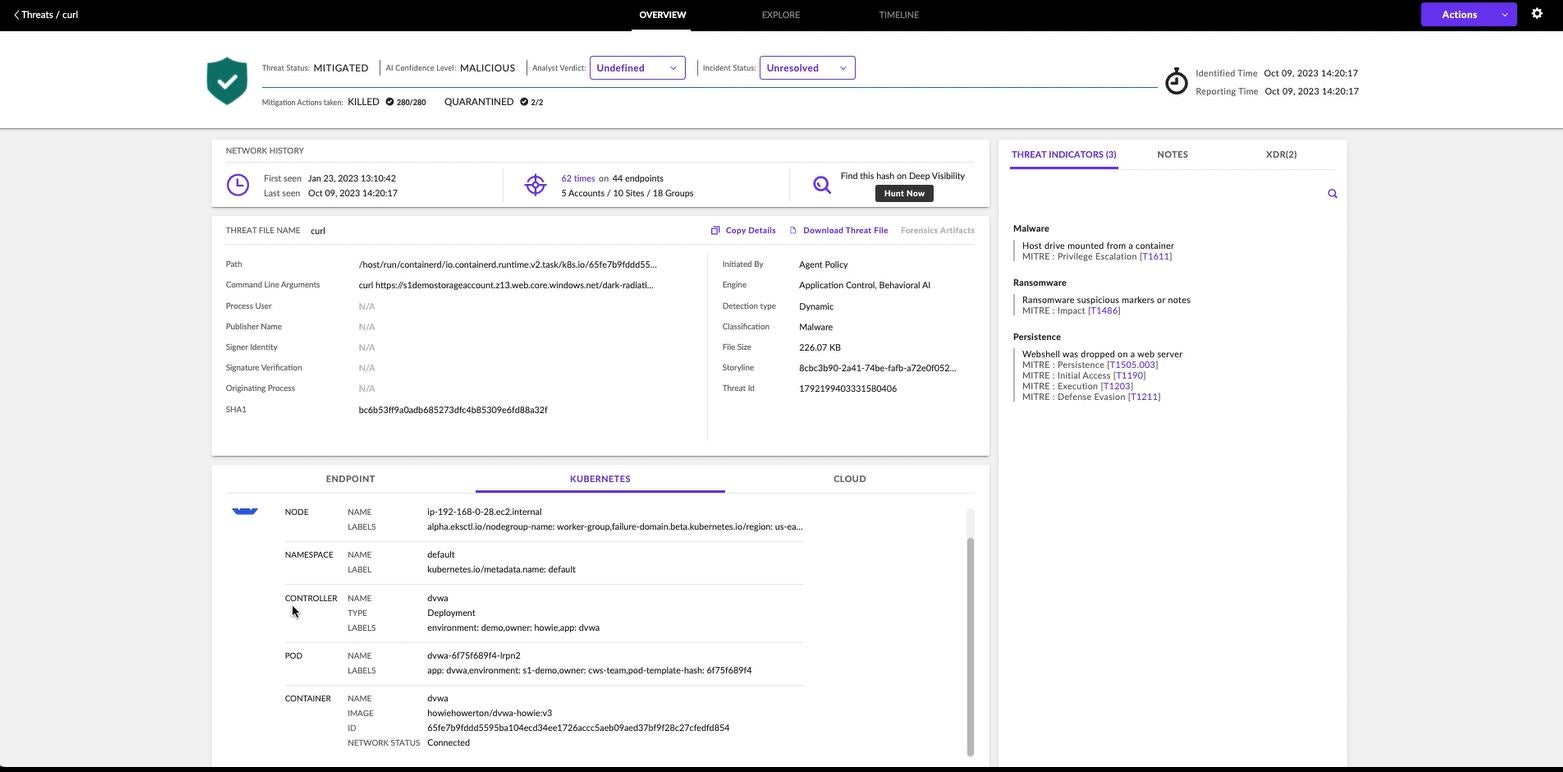
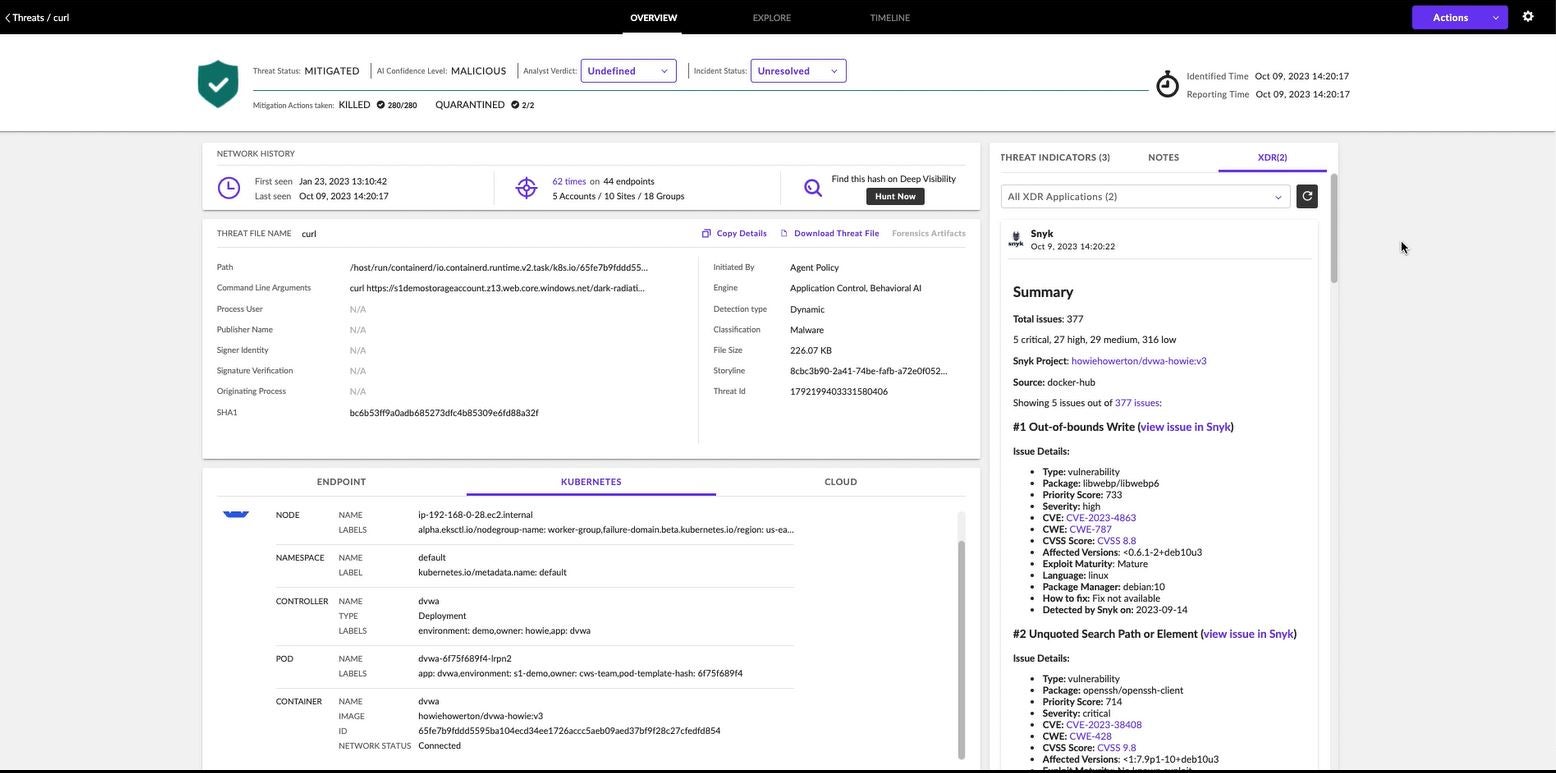
With our integration with Snyk Container, SentinelOne automatically enriches these threat details with information from Snyk about vulnerabilities found in the workload image from which our container was instantiated.
As shown in Figure 4, Snyk has identified 377 vulnerabilities in the workload source code of varying severity, including five which are critical. A cloud security practitioner can include this information in a security ticket which they then route to the DevOps owner. The cloud security analyst and developer can easily pivot from the SentinelOne console to the Snyk Platform via a convenient deep link, to view the project details and fix the vulnerabilities at the source code.
Once the developer updates the code, rebuilds, and redeploys the image to the registry, a new container image can be launched from the clean image.
Better Cloud Security Outcomes
By correlating runtime threat detections by SentinelOne with vulnerability details identified by Snyk, cloud security practitioners can slash mean time to repair and more easily collaborate with AppSec and development teams to solve root cause in workload source code. The combination of SentinelOne Singularity Cloud Workload Security and Snyk Container help customers close the runtime-to-build-time feedback loop, to improve triage, prioritization, and create better cloud security outcomes.
To see how our two solutions work seamlessly together, check out this 2-minute guided walk-through. To learn more about the value of real-time CWPP in your cloud security stack, head over to the Singularity Cloud Workload Security homepage. And of course, whenever you are ready, you may connect with one of our cloud security experts for a personalized demo.
Join Our Webinar | Nov 16
from SentinelOne https://bit.ly/3FSnL7C
via IFTTT
No comments:
Post a Comment