This post is also available in: 日本語 (Japanese)
Executive Summary
During our research discovering threats in legitimate network traffic, activity generated by a certain type of Android Package Kit (APK) files kept hitting our radar. This activity led us to conduct an in-depth investigation on the associated APK files. Our research revealed a family of malicious APKs targeting Chinese users that steals victim information and conducts financial fraud.
To do this, the threat actor masquerades as a law enforcement official and says the target's phone number or bank account is suspected of being involved in financial fraud. They then guide the person to download an app that will allow the attacker to investigate their bank transactions. The threat actor then instructs the person to select their bank from the app and fill in their personal information, including payment card details. At this point, the attackers can drain the bank account of whatever funds are available.

Palo Alto Networks customers are better protected from this malicious APK through our Next-Generation Firewall with Cloud-Delivered Security Services, including Advanced WildFire, DNS Security and Advanced URL Filtering. If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
Table of Contents
Table of Contents
Campaign Overview
Malware Analysis
Malware Installation
Malware Behavior
How the Threat Actor Conducts Financial Fraud
Network Traffic Features
Advanced Malware Traffic Detection
Conclusion
Indicators of Compromise
Malicious APK Samples
Infrastructure
References
Campaign Overview
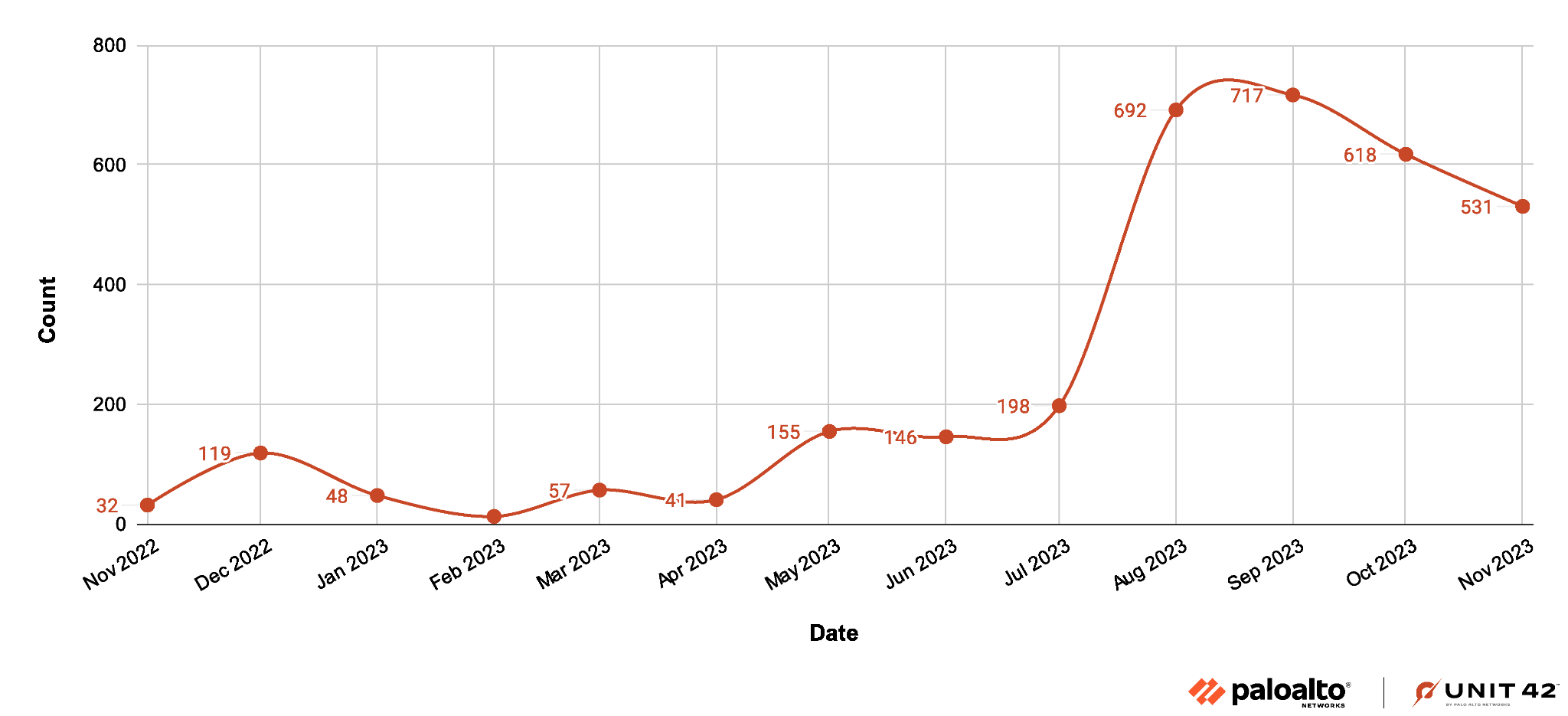
We found indicators of the malicious APK activity we’ll discuss in this post as early as November 2022. Following several months of dormancy, the malware delivery attempts surged with a peak value of 717 in September 2023.
Figure 1 presents the trend of delivery attempts from November 2022 through November 2023.
Malware Analysis
Malware Installation
Our analysis of the malicious APK samples reveals victims must have retrieved them from non-official third-party sources, due to the non-compliance of the APK with official Google Play Store submission policies.
We believe threat actors likely delivered these APK samples through social engineering, similar to the methods described by the following sources from China:
The threat actors used this Android application to impersonate law enforcement authorities. They claimed that the victim's bank account was suspected of being involved in money laundering or other financial-related crimes. They then sent the victim a download link to this application package, urging the victim to input their sensitive personal information into the malicious application.
Malware Behavior
The malicious Android application would be installed on the victim's device with the name "安全防护" (translated from Mandarin as "Security Protection"). Upon execution, the application requests the following permissions for the capability to make phone calls and receive SMS text messages:
- android.permission.CALL_PHONE
- android.permission_RECEIVE_SMS
The android.permission.CALL_PHONE permission allows the app to disconnect incoming phone calls, and the android.permission_RECEIVE_SMS permission allows the app to block SMS messages received by the Android device.
To control or block phone calls and SMS messages, the application would typically need to be set as the device's default phone/SMS application handler. A request to change this setting is depicted in the screenshot in Figure 2 below.
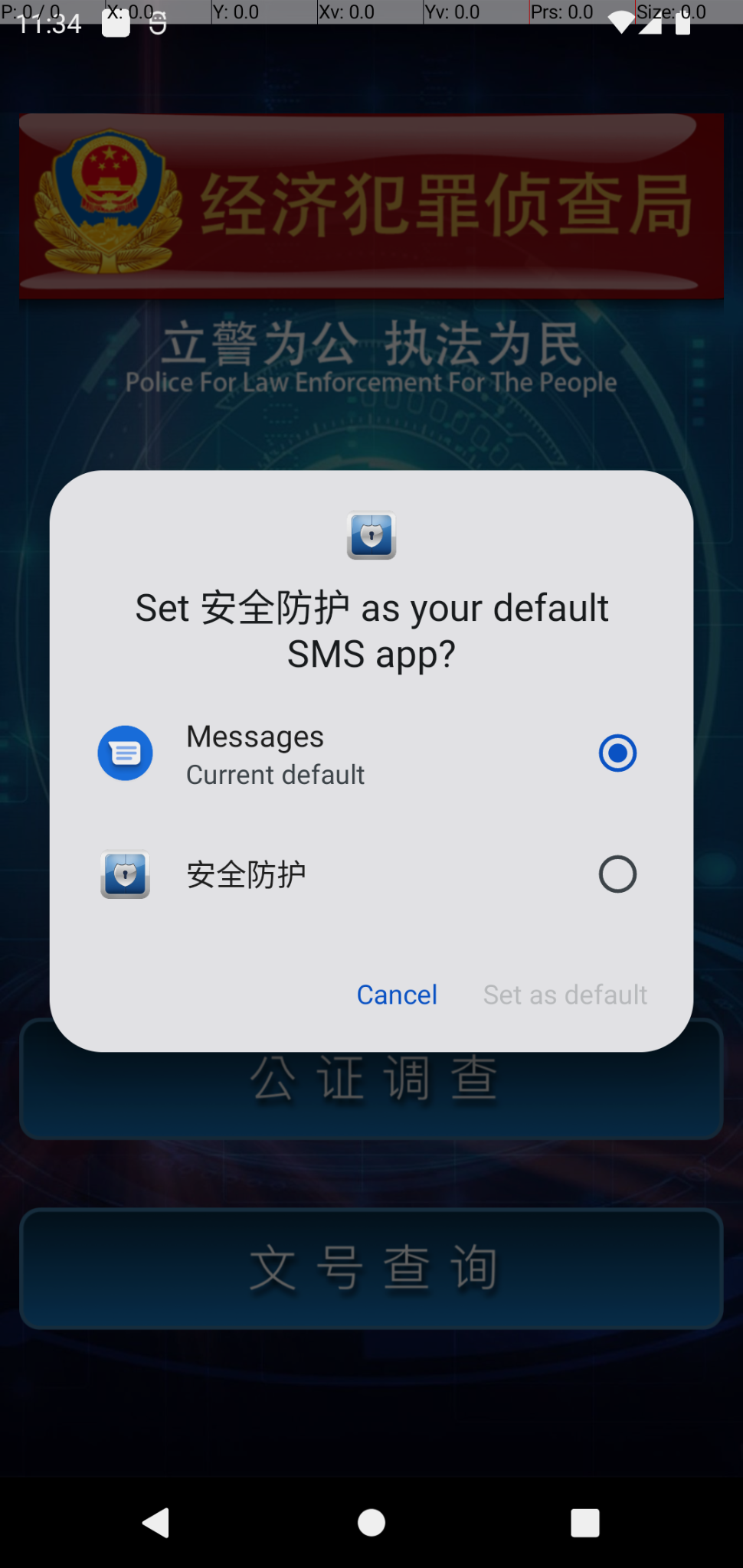
By blocking incoming phone calls and SMS messages, victims are not able to receive alerts about financial fraud from others or from legitimate law enforcement.
How the Threat Actor Conducts Financial Fraud
First, the threat actor masquerades as an official law enforcement authority and alleges the victim's phone number or bank account is suspected of being involved in financial fraud.
To convince people the app is legitimate, the threat actor provides a legal case number, and they ask the person to search for this case number in the malicious application. The threat actor will also generate a fake legal case document with the intended victim's name on it. As depicted in Figure 3, the malicious application requests the legal case number and the person’s sensitive personal information.
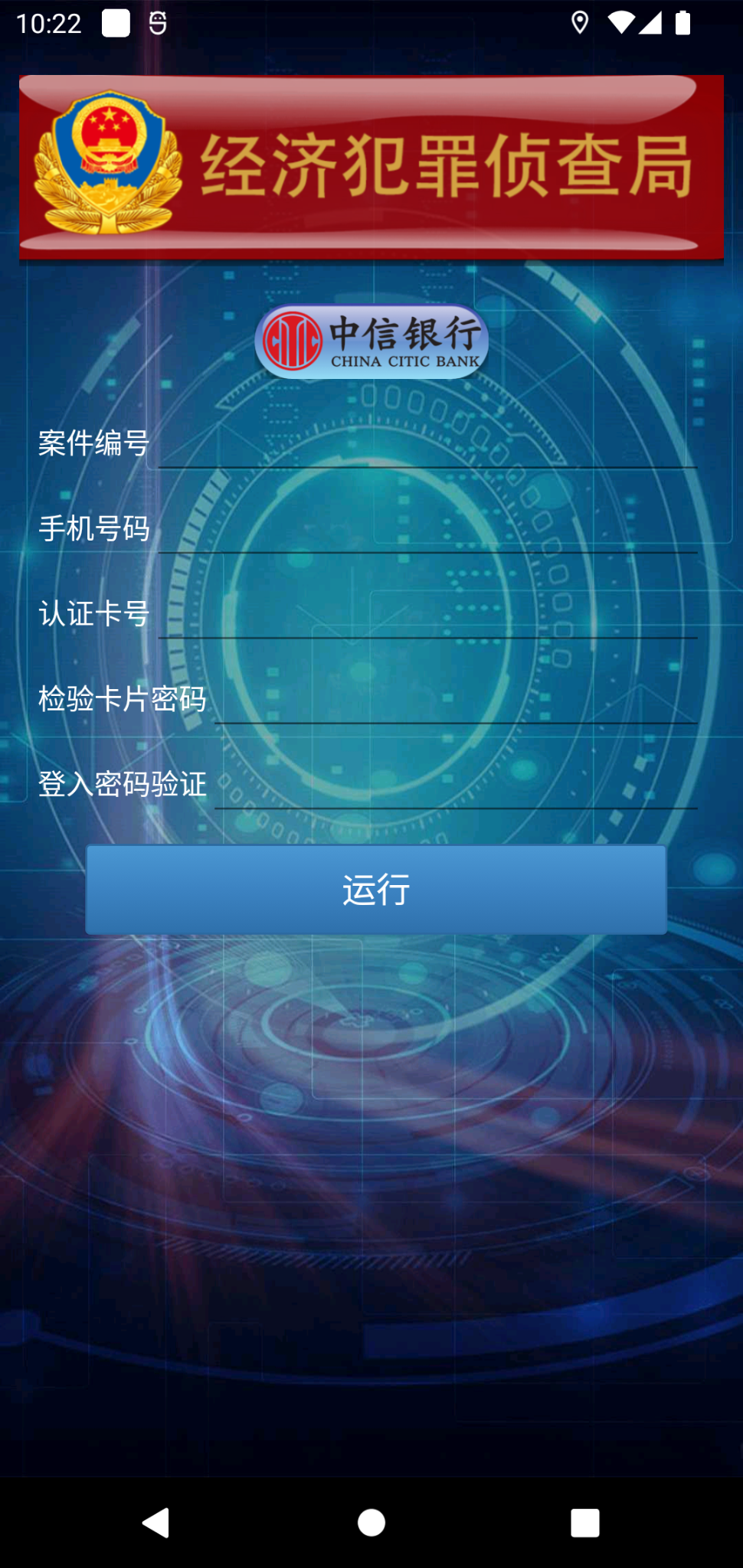
Once a target fully believes the app is from a genuine law enforcement authority, the threat actor guides the person to download the next-stage payload. The app accomplishes this by sending a download link, under the pretext of investigating bank transactions and the source of deposited funds.
The APK malware sample supports selection from a variety of banking institutions (Figure 4). Once selected, the threat actors instruct victims to fill in their sensitive personal information, including payment card details.
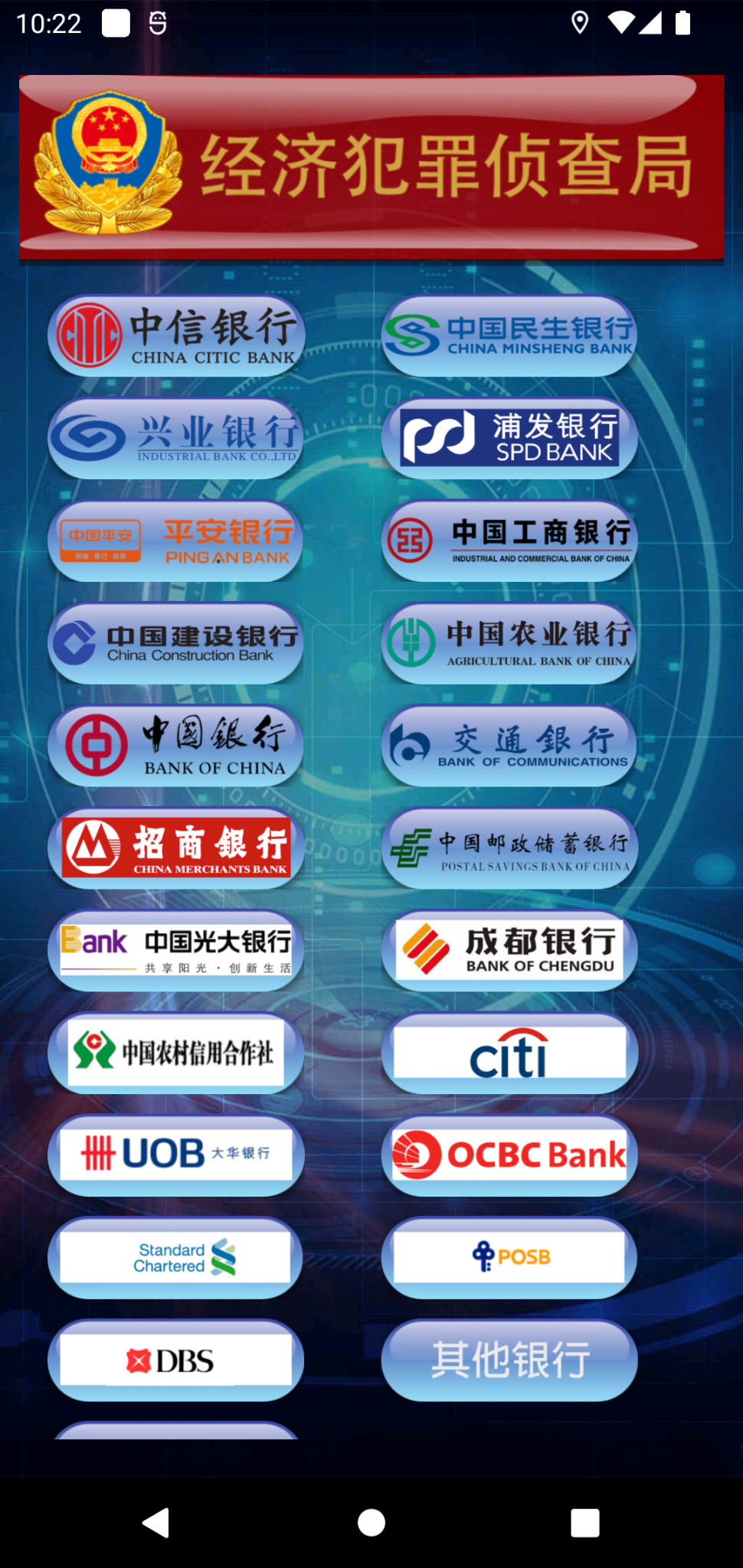
Since the application can block incoming phone calls and SMS messages, these financial institutions cannot contact the victims through their Android device, which makes it more likely that victims will be trapped in the scam.
Network Traffic Features
Our WildFire sandbox captures, detects and prevents this specific malware family, better protecting our customers from such a threat. In particular, the dynamic analysis logs contain traces of outgoing HTTP network connections to remote endpoints (namely, log[.]tbs[.]qq[.]com and 52[.]221[.]181[.]208, which were generated by one of the APK samples).
The following are the sample URLs we have logged:
- hxxp://log[.]tbs[.]qq[.]com/ajax?c=dl&k=27d9e98adf5322f7ed5d3ba399165d4f
- hxxp://52[.]221[.]181[.]208/api/GetCmd[.]aspx
- hxxp://52[.]221[.]181[.]208/api/getconfig[.]aspx
- hxxp://52[.]221[.]181[.]208/resource/260707[.]jpg
Advanced Malware Traffic Detection
Since the domain (log[.]tbs[.]qq[.]com) used by the malicious APK files during their execution is legitimate, definitively identifying isolated connections as malicious becomes challenging. Therefore we propose that multiple connections to such IP addresses and domains within a brief time frame can serve as a possible indicator of command and control (C2) traffic.
This behavior strongly suggests malicious network traffic activity rather than legitimate network traffic. To enhance our detection capabilities, we leverage these attacking network endpoints to generate advanced signatures for detecting malware activities. Our signatures incorporate multiple network entities, enabling us to effectively identify and mitigate malware communication sessions that might otherwise evade detection based solely on single-entity analysis.
Conclusion
Attackers take advantage of an information gap and the victim's fear of being embroiled in legal action, coupled with carefully designed social engineering attacks, to reap significant illegal profits.
To defend against the threat, we highly recommend that people do not download third-party applications from untrusted mobile application stores and do not share sensitive information with unknown sources.
Palo Alto Networks customers are better protected from malware discussed in this article through products like our Next-Generation Firewall with Cloud-Delivered Security Services that include Advanced WildFire, Advanced Threat Prevention and Advanced URL Filtering.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared our findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
Malicious APK Samples
- 2cf117abf5ced6d37e98068d1961b85f400ecede4c11ebd69cc5cc9629aaaacd
- 6e43d2d4f14b26a75b9094eb1bd509b0f63e069a3c97867bfb0ac6c2a154dcd6
- b0ad0de29f9c64e696212121e5e716b99668906d6531804fd6e5a55d95c9bd1f
- bf4a214782d6a3ce14fb37af919b4803d3013cc5774b2782290e33985bebd01b
- d342c40f126a150cd93da083c237cda7d9fc739a2050a819573b5fb4a3a67026
Infrastructure
- 13[.]250[.]172[.]152
- 18[.]143[.]192[.]34
- 18[.]166[.]72[.]58
- 52[.]221[.]181[.]208
References
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
from Unit 42 https://bit.ly/3Hm5joo
via IFTTT
No comments:
Post a Comment