Getting data into your security information and event (SIEM) instance is crucial, and LogRhythm is highly focused on making it easy to do that.
As part of our latest quarterly product release, LogRhythm SIEM version 7.15 builds on the innovation we delivered in October 2023 and now supports managing additional Beats from the Web Console. The latest release features platform enhancements including simplifying Windows Event log onboarding and improving the analyst workflows when reviewing alarm notifications. It also includes new in-app LogRhythm SIEM tutorials, and new and updated supported log sources. Read on for a deeper dive into the latest LogRhythm SIEM release.
Save Time Onboarding New Log Sources in the Web Console
At LogRhythm, we want to make the work for administrators and analysts as easy as possible.
That’s why we’ve expanded the number of Beats administrators can manage from the Web Console. By onboarding log sources in the Web Console, you can cut your Beat Administration workload in half. In the latest release, LogRhythm now supports management for six additional Beats including:
- Gmail Message Tracking
- Okta
- Darktrace
- Sophos
- Qualys FIM
- GSuite
Last quarter, LogRhythm introduced a new workflow to onboard data in the Web Console, bringing the process into a simple wizard-driven experience. This experience makes it easier to get data into the system and expedites the onboarding process. It expedites the onboarding of LogRhythm Beats and reduces the need to switch between the Web and Client Consoles, cutting your Beat Administration workload in half.
Figure 1: LogRhythm now supports Beat management for GSuite in the Web Console.
Watch how easy it is to onboard log sources in the Web Console in this comparison video.

LogRhythm SIEM Platform Enhancements
Managing a SIEM platform isn’t always easy so our team has made your experience even better. LogRhythm 7.15 features platform improvements that enhance your workflows, save you time, and reduce the number of steps to complete a task.
Migration Path to Rocky Linux
As CentOS 7 reaches end of life from the Red Hat organization, we understand the importance of providing an alternative operating system to migrate DX and OC machines. That’s why LogRhythm created a detailed guide to migrate to Rocky Linux. This migration path offers customers continued support from the OS vendor to address security and bug fixes.
Web Console Log Export in Users’ Local Time
LogRhythm has made it easier to convert time zones when exporting logs from the Web Console to a CSV file. Customers can now export CSV files in their local time zone versus having to convert from the Coordinated Universal Time (UTC) time zone. Now users don’t have to do through the cumbersome conversion process to identify the correct time, improving their experience with the SIEM platform.
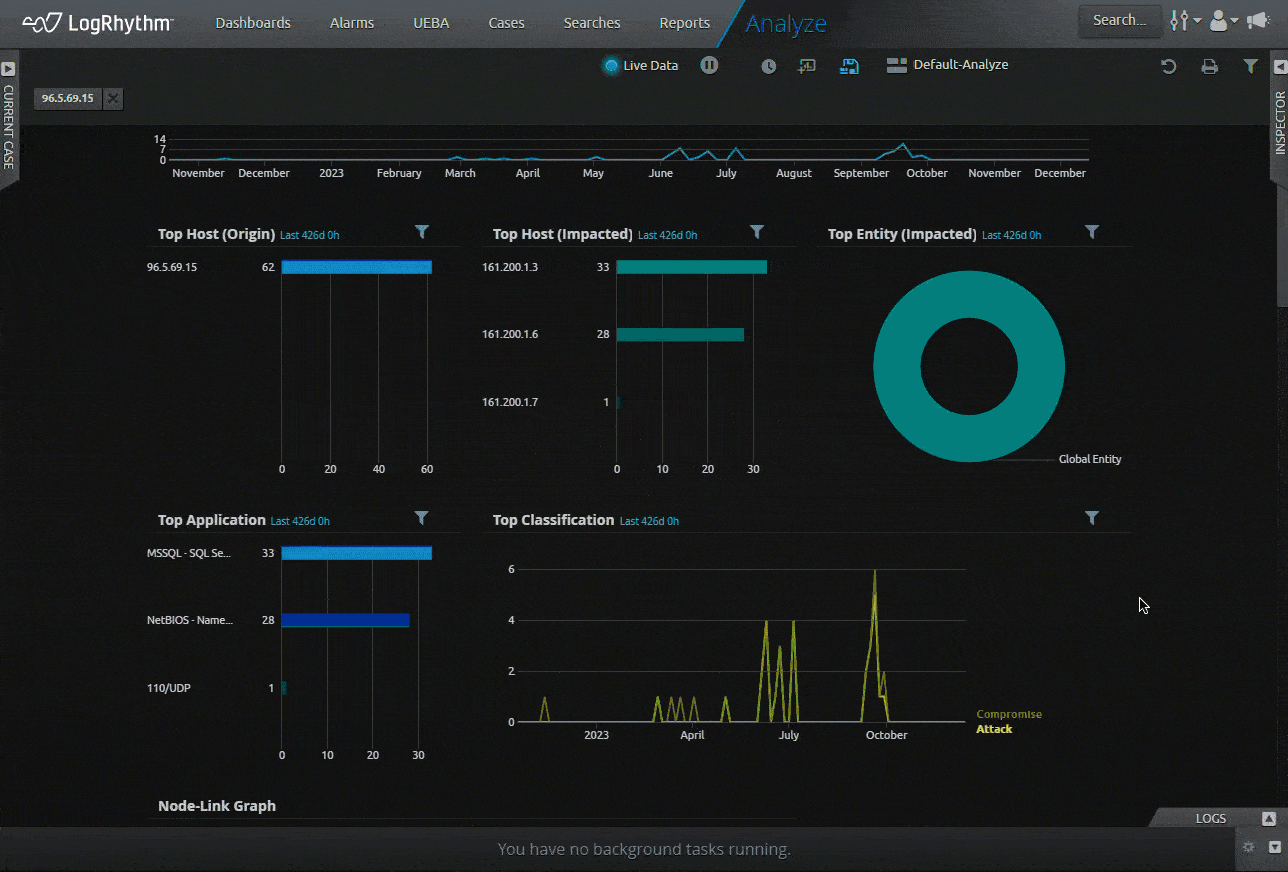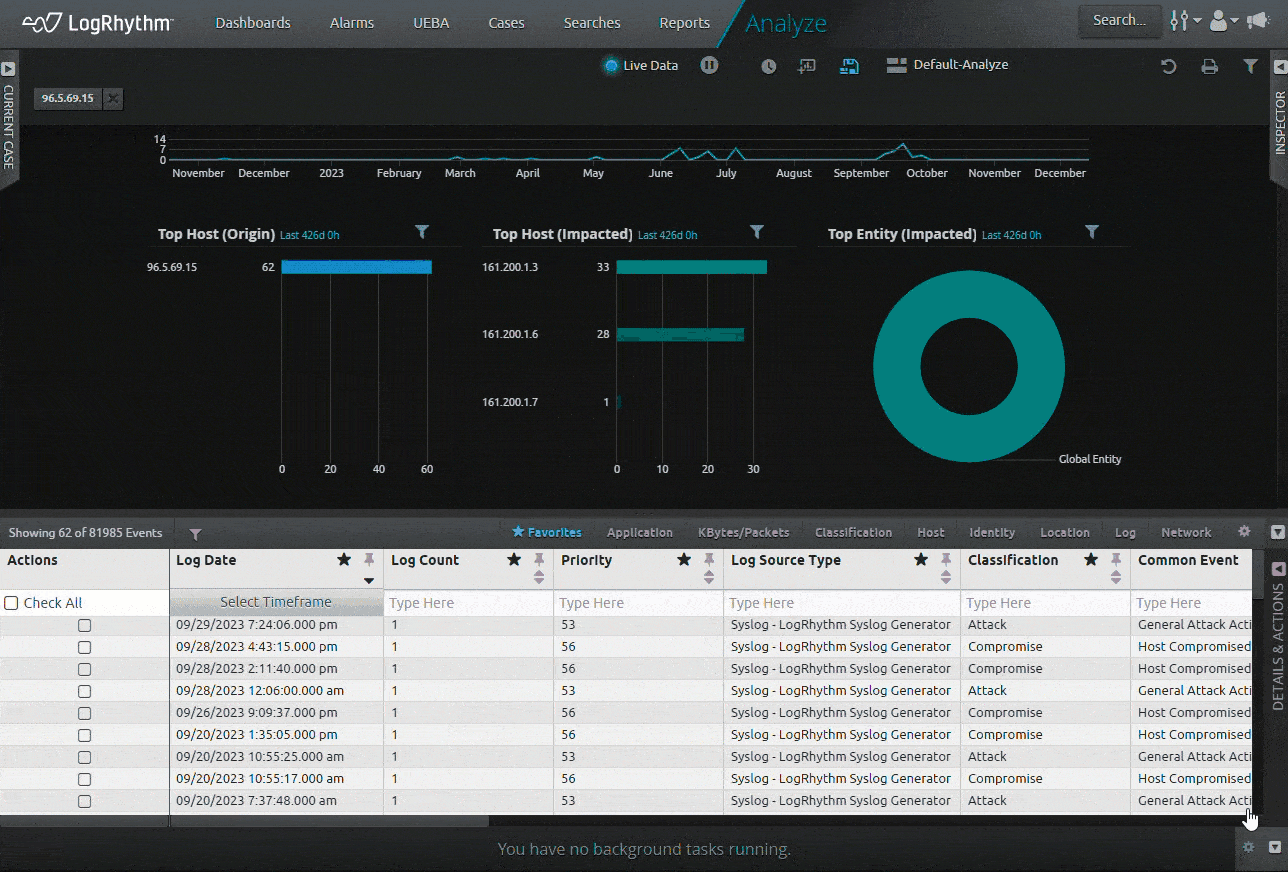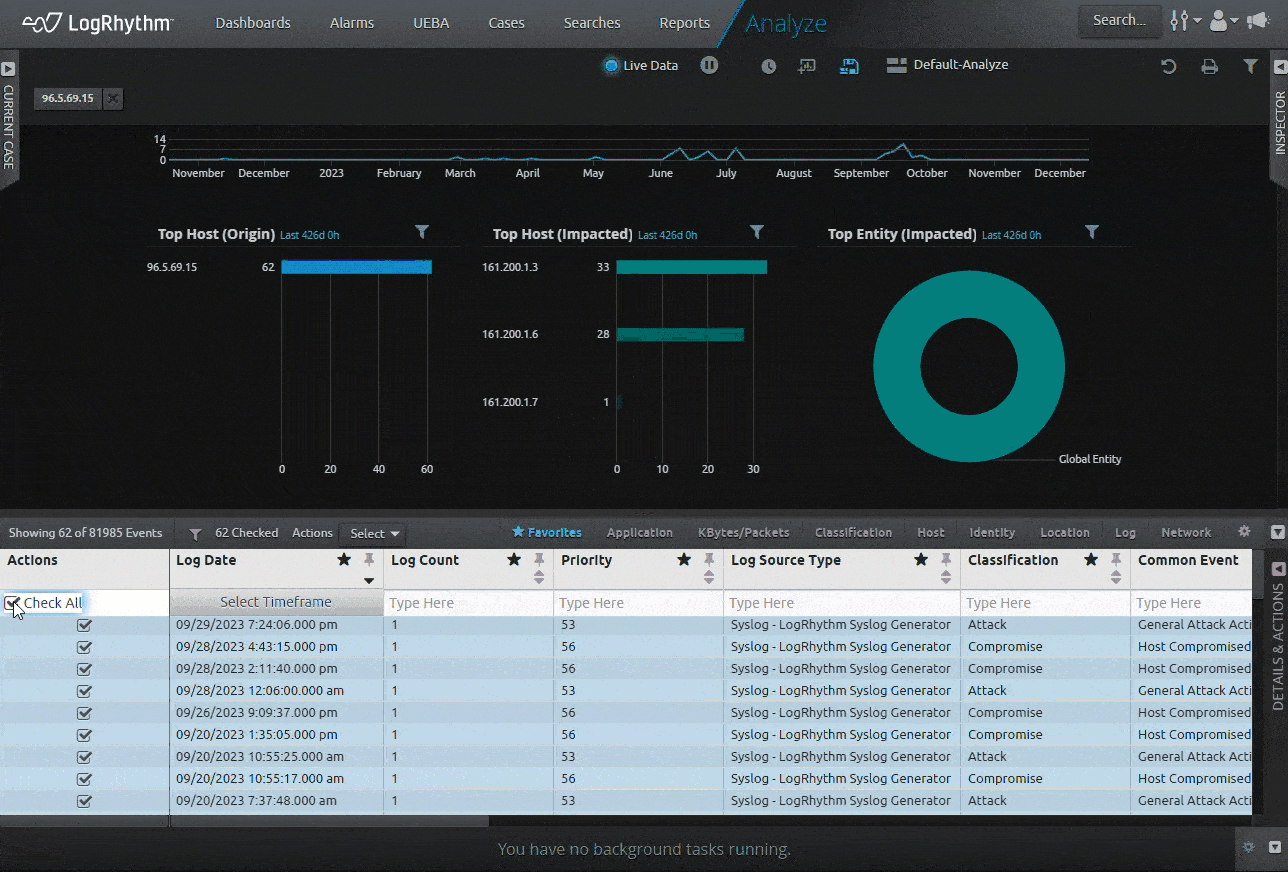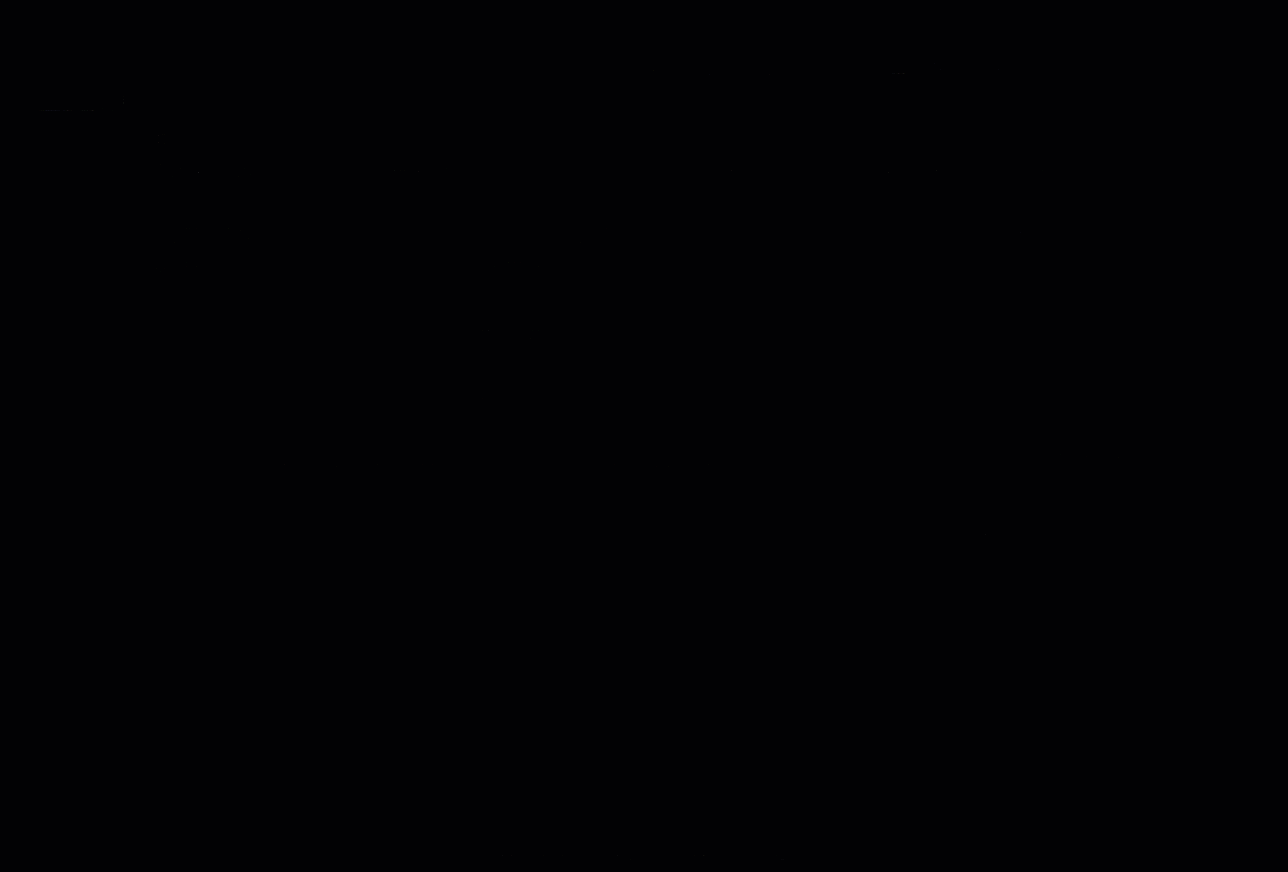
Figure 2: LogRhythm now exports logs to CSV with the user’s local time zone.
Automatic Flat File Path Population for Windows Event Logs
To make the workflow and tasks easier for LogRhythm SIEM users, we’ve changed a setting to automatically fill the flat file path population for Windows Event Log-based log sources. Now when users add Windows PowerShell Event logs or Windows SysMon Event logs, for example, LogRhythm SIEM 7.15 auto updates that field. This update saves users time and provides a more streamlined experience.
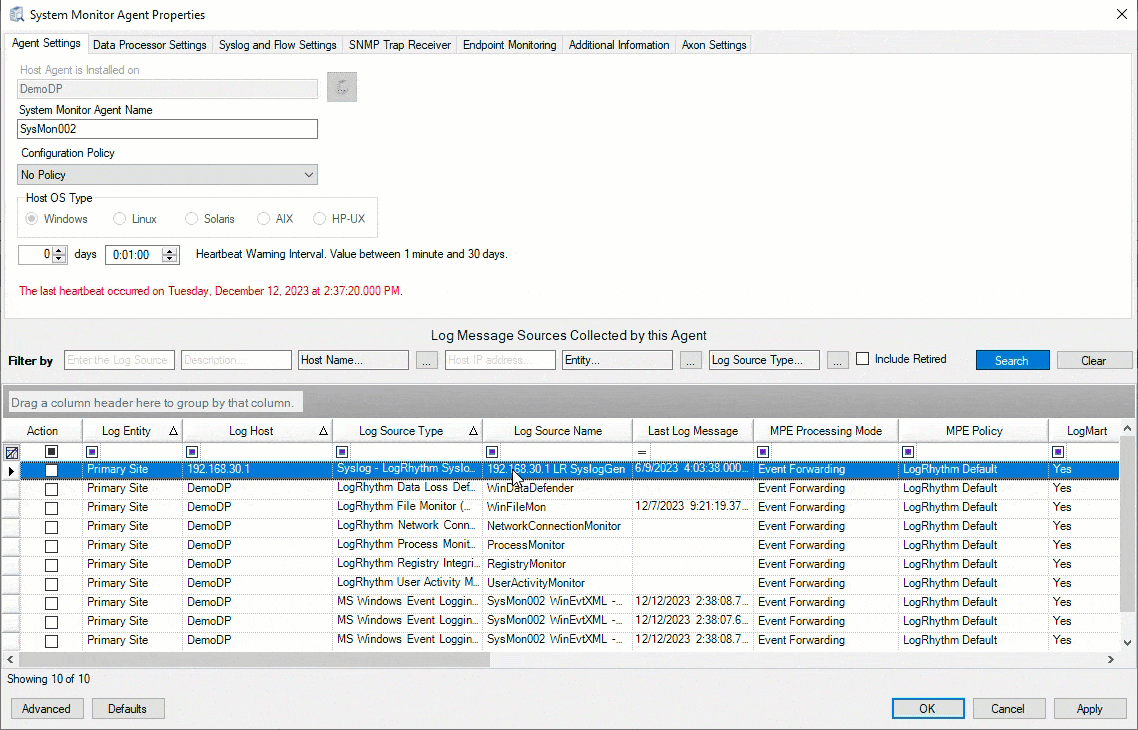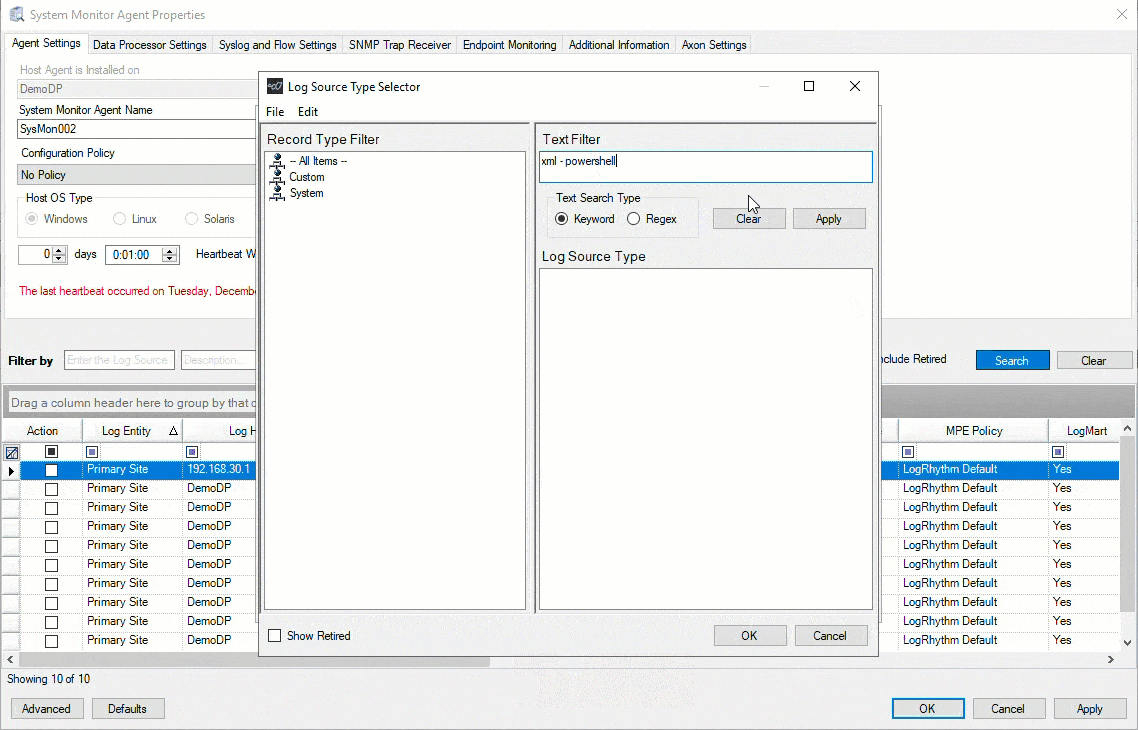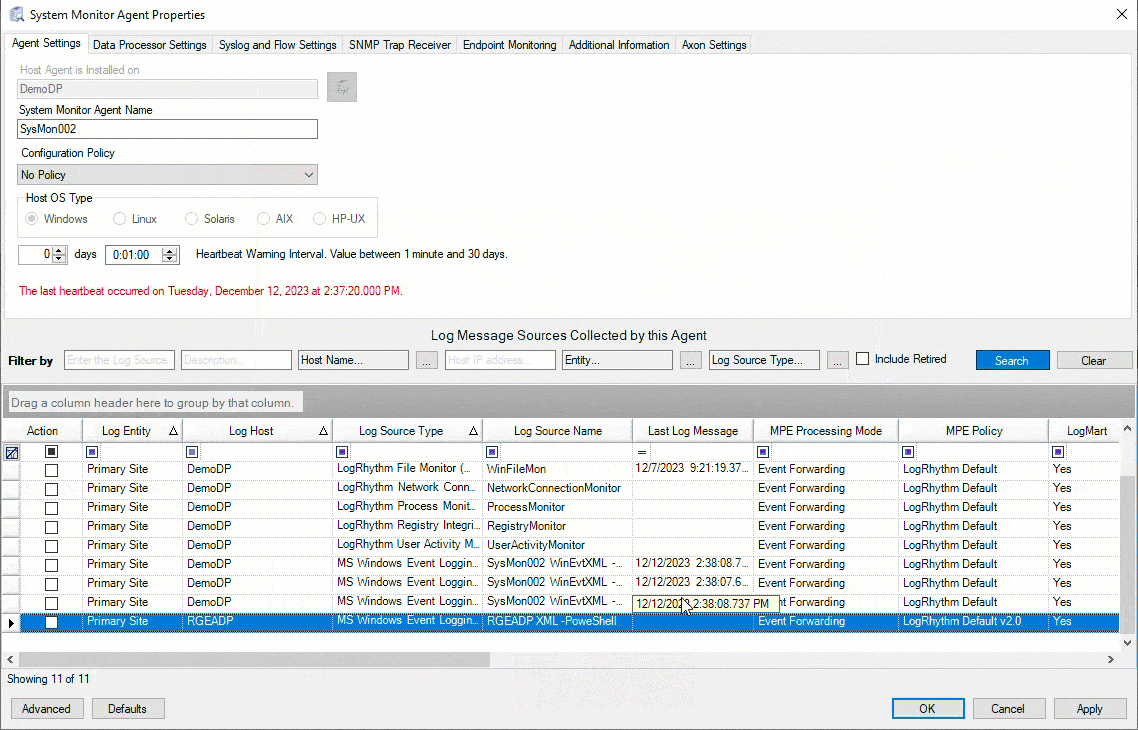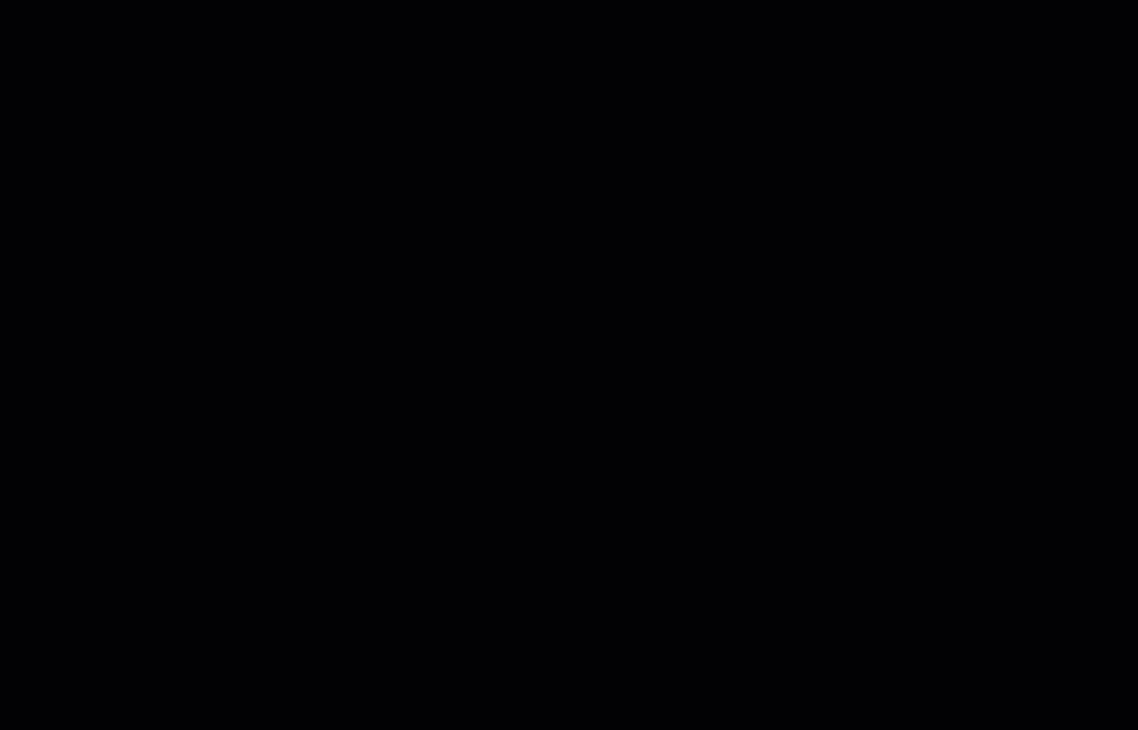
Figure 3: LogRhythm SIEM automatically fills the flat file path population for Windows Event Log-based log sources.
URL Links in Alarm Notifications
Navigating to an alarm from a notification is easier than ever. Our team improved the experience to direct you to alarm details even if you previously weren’t logged into the Web Console. After clicking a URL in a notification and logging into the Web Console, LogRhythm now automatically routes you to the correct alarm. This update saves you time and removes the hassle of searching for important notifications.
In-Platform Resource Center Tutorials
We know it’s important to stay up to date about the latest SIEM updates and training resources. To give you an easy way to stay fresh on platform training, LogRhythm launched five new tutorials in the Resource Center in the Web Console. They include:
- Beats Onboarding: Adding a new Beat and Log Source involves three key steps, which must be completed in order. This tutorial shows you the steps to following, including:
- Verify your Open Collector’s health
- Add a Beat
- Add a Log Source
- Case Management Overview: Cases provide a centralized repository for tracking and investigating events of interest. Watch the tutorial for a quick tour, including:
- Creating cases
- Adding evidence
- Updating case details
- Customizing the Cases Page
- Search: Follow along for a quick tour on how to use the Search capabilities in LogRhythm’s SIEM, including:
-
- Building a query
- Running a tail
- Advanced options
- Alarm Management & Best Practices: An alarm is a record of an event, or series of events, that triggered an alarm rule. In this tutorial, watch a quick tour on the following:
- Alarm card features
- Inspector panel details
- LogRhythm SmartResponse™ automated actions
- Dashboard Overview: Dashboards provide an easy and powerful overview of the logs your SIEM processes. This dashboard tour will cover:
- Key features on the dashboard
- How to switch between dashboards
- Adding and customizing widgets
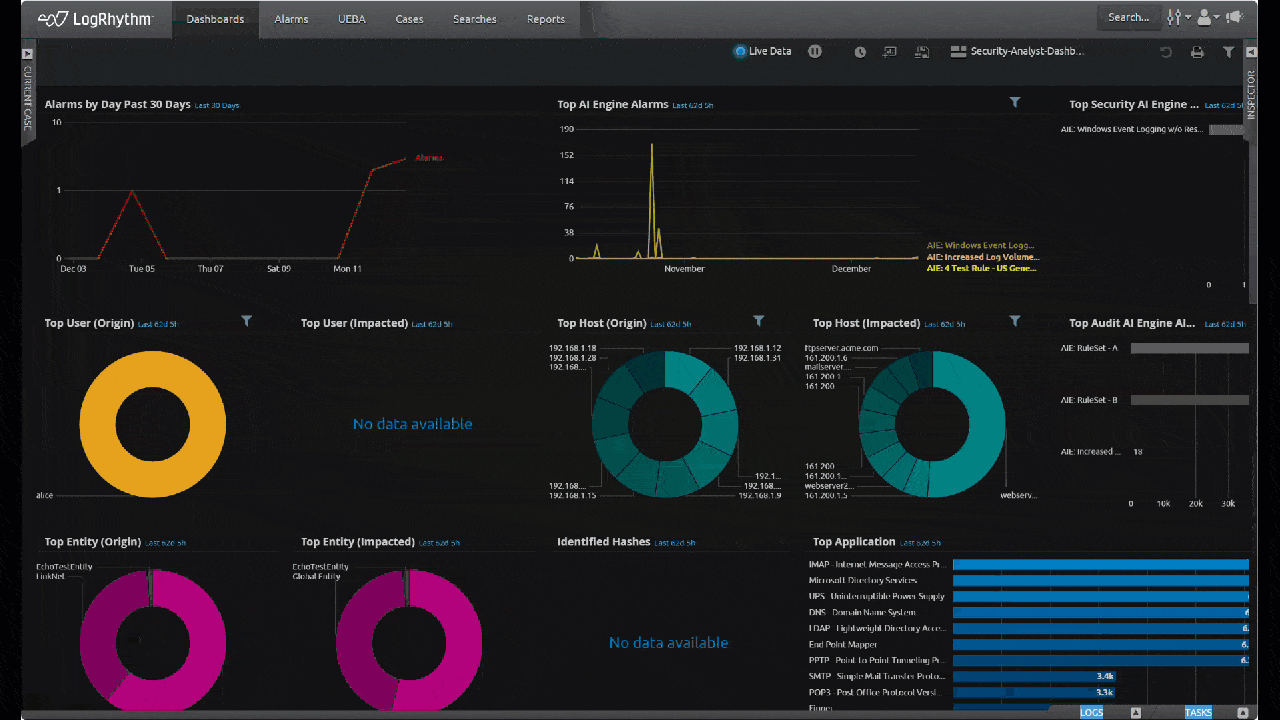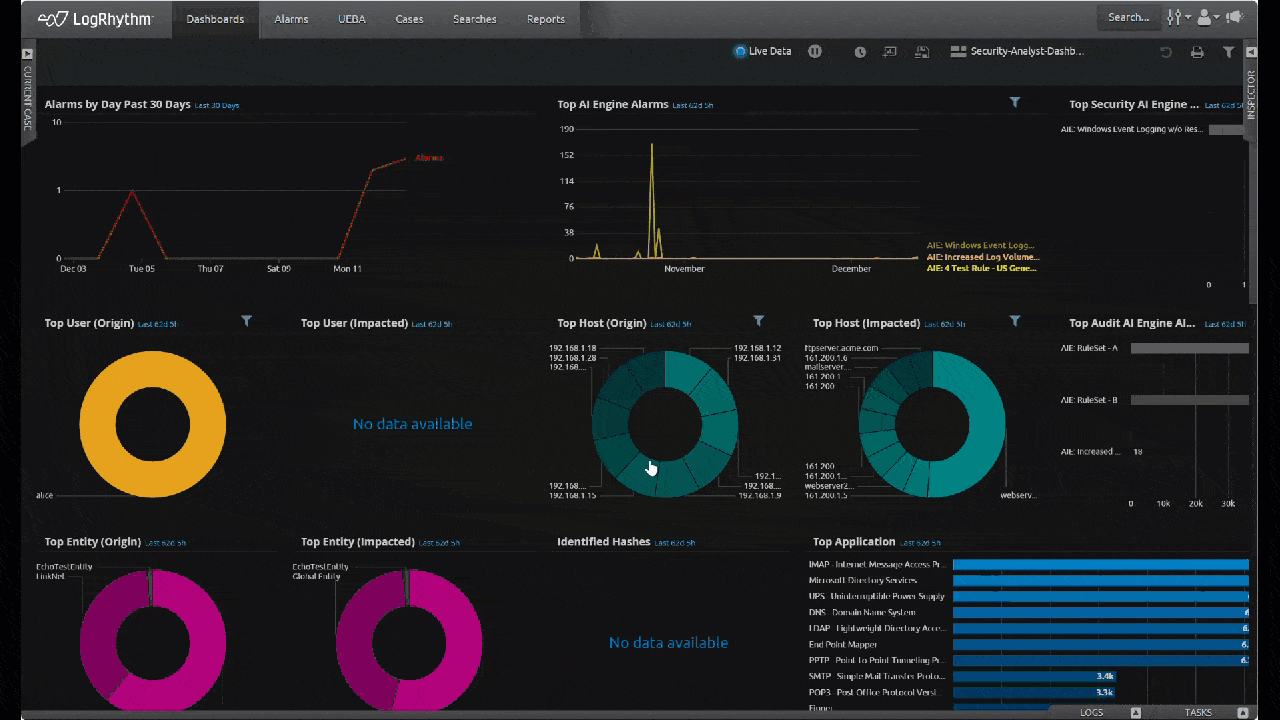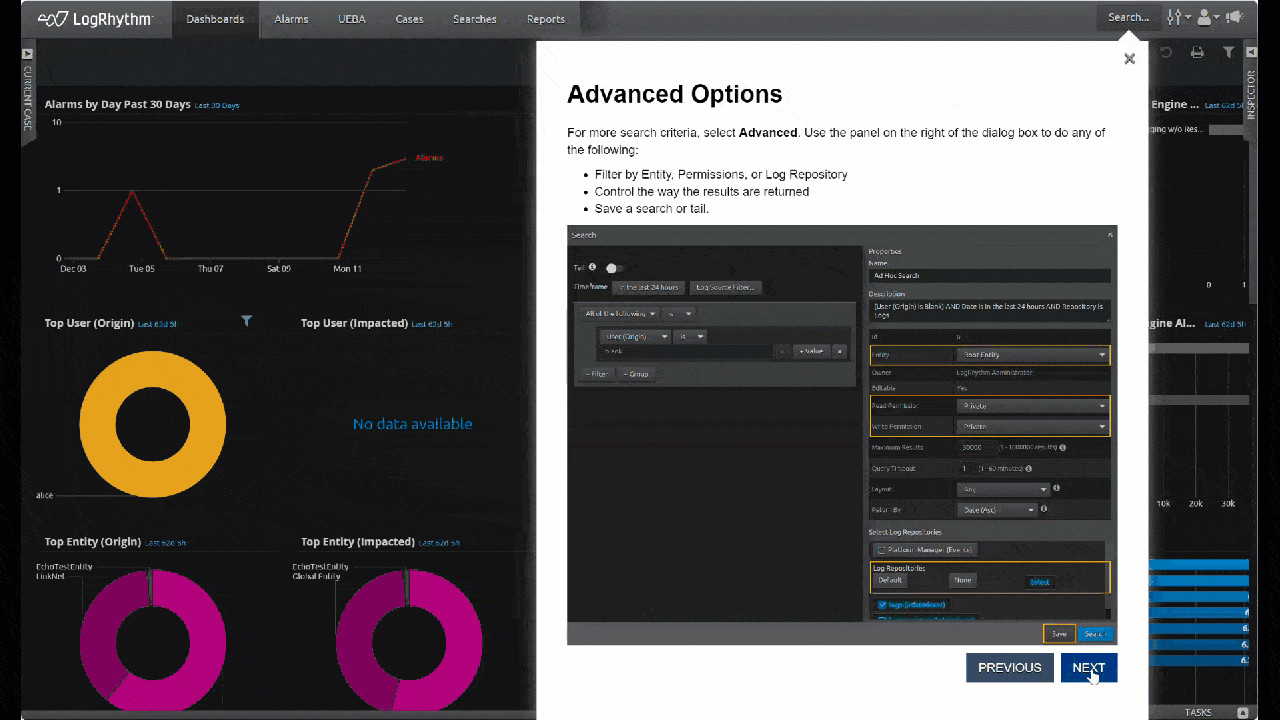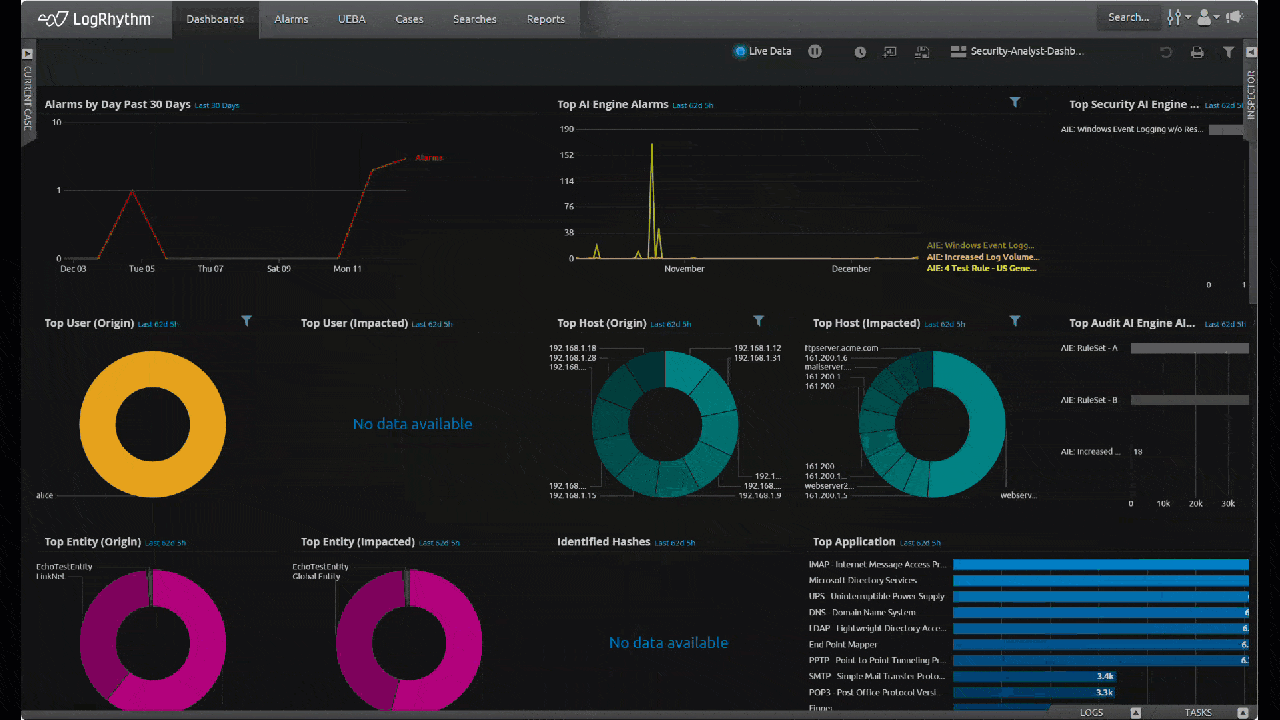
Figure 4: LogRhythm released new guided trainings in the Resource Center in the Web Console.
Ongoing Log Source Support
LogRhythm continues to grow the log sources it supports to boost correlation and analysis. We now offer support for the following:
- FortiNAC: Provides protection against IoT threats, extends control to third-party devices, and orchestrates automatic responses to a wide range of networking events
- Tenable.OT: Protects industrial networks from cyber threats, malicious insiders, and human error. New polices help prevent classification errors and provide more consistent parsing of log source data for Tenable Operational Technology (OT) while new MPE rules parse log metadata to the correct schema fields and classify highly complex log source data.
- strongSwan: This complete IPsec solution provides encryption and authentication to servers and clients.
- F5 Big IP System: A set of application delivery products that work together to ensure high availability, improved performance, application security, and access control
- QRadar: New policies for collecting and parsing network security logs from QRadar
LogRhythm also enhanced more than 35 log sources as part of LogRhythm SIEM 7.15, including:
- Mimecast: Updated Polices and workflow for collecting logs from Mimecast
- Imperva Database Activity Monitor (DAM): Updated Polices help prevent classification errors and provide more consistent parsing of log source data for Imperva Database Activity Monitor (DAM) while new Message Processing Engine (MPE) rules parse log metadata to the correct schema fields and classify highly complex log source data.
- Palo Alto Cortex Data Lake: Updated Polices for schema changes help prevent classification errors and provide more consistent parsing of log source data for Palo Alto Networks® Cortex Data Lake.
Download LogRhythm SIEM 7.15 Today!
Don’t miss the latest features from LogRhythm SIEM! Existing customers can request a license here and download LogRhythm 7.15 from Community. Information and documentation on all the latest enhancements are available in the Release Notes.
To help you stay up to date on LogRhythm SIEM releases, LogRhythm offers an Unlimited Upgrades Service that lets you upgrade to every SIEM product release available under your subscription. Schedule an upgrade on your schedule. Learn more about our Unlimited Upgrades Service.
To learn more details about LogRhythm SIEM 7.15 and see a demo, register for the January 2024 Quarterly Launch webinar or visit our What’s New webpage.
The post LogRhythm SIEM 7.15: Leverage New Beats and Platform Improvements appeared first on LogRhythm.
from LogRhythm https://bit.ly/3vq00lq
via IFTTT
No comments:
Post a Comment