The Good | TrickBot Developer Jailed for Five Years
Developer and distributor of the notorious TrickBot malware, Russian national Vladimir Dunaev, was handed down 5 years and 4 months of prison time this week. According to the DoJ, TrickBot caused tens of millions of dollars in losses and was used to attack hospitals, schools and businesses with ransomware in the U.S.
TrickBot started out in life as a dedicated banking trojan but over time evolved into a complex malware framework, shifting focus to enterprise environments and incorporating a suite of features including network profiling, mass data collection and lateral traversal exploits. At its height, TrickBot was believed to be in use by both APTs and crimeware actors.
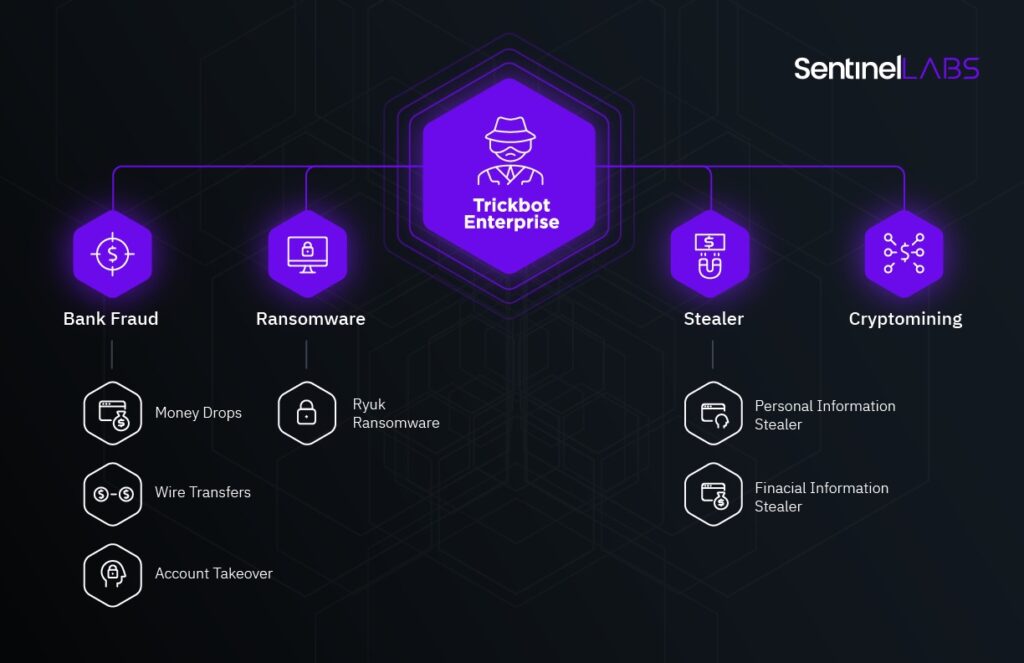
Dunaev was arrested in South Korea back in 2021 and subsequently extradited to the U.S. that October. He finally stood trial in November of 2023, when he pleaded guilty to conspiracy to commit computer fraud and identity theft, and conspiracy to commit wire fraud and bank fraud. According to the DoJ, Dunaev had created programs to bypass AV software and developed credential harvesting and data mining tools.
He is the second member of the gang behind TrickBot to be sentenced to jail time: A Latvian woman, Alla Witte, received 2 years and 8 months in June of last year. A number of other individuals have been indicted and sanctioned by U.S. authorities.
The Bad | Researchers Warn of Risks with Google Search
Security researchers are raising concerns about Google Search in the wake of increasing abuse of Google Ads – a service which promotes paid advertisements above organic search results – by various threat actors.
In one report this week, researchers noted how Chinese-speaking Googlers were being served Remote Administration Trojans (RATs) through malicious adverts shown at the top of search results for messaging apps like Telegram, which are restricted in China.
Closer to home, KrebsOnSecurity said U.S and other English-speaking users were being targeted when searching with Google for software. In one recent example, searches for the (legitimate) FreeCAD graphic design program were returning links to the malicious freecad-us[.]org domain above the real freecad.org site. Searches for other popular software that have been seen returning malicious paid advertisements include Corel Draw, GitHub Desktop, RoboForm and TeamViewer.
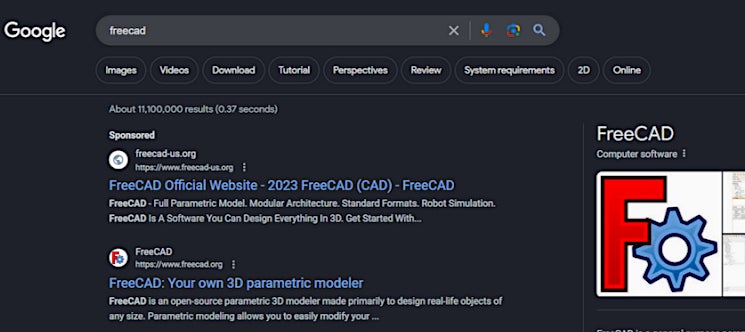
According to SentinelLabs’ Tom Hegel, threat actors behind the malvertising schemes rotate serving malware with serving legitimate software as a means to escape detection by Google. Krebs quoted Hegel as noting that “In the malicious ad campaigns we’ve seen…they would wait until the domains gain legitimacy on the search engines, and then flip the page [to serve malware] for a day or so and then flip back.”
In addition, the malicious sites use scripts to fingerprint visitors and determine whether they should serve malware based on criteria such as geolocation, browser or language. This allows the sites to target, say, users from the United States while ignoring users from other locations. An earlier report into this kind of malvertising suggested that many of these sites are used to deliver infostealers and trojans like IcedID, Formbook and others.
In response, Google said that it had removed the ads brought to its attention by the report, but researchers remain concerned that the problem is beyond Google’s ability to fully control. Users are advised to exercise caution when clicking sponsored links returned in Google searches.
The Ugly | Russian APT Strolls Into Microsoft and HP Networks
Both Microsoft and Hewlett Packard Enterprise revealed this week that they had separately become victims of Russian state-sponsored intrusions by APT 29, also known as Midnight Blizzard, The Dukes, Nobelium and NobleBaron. The same threat actor was held responsible for the SolarWinds supply chain attack in 2021.
January 12th, Microsoft discloses that they were compromised by APT29 a/k/a/ Midnight Blizzard and state the group got access to emails for corporate leadership, cyber security personnel, and legal.
January 24th, Hewlett-Packard discloses that they were compromised by APT29…
— vx-underground (@vxunderground) January 24, 2024
In a statement released Thursday, Microsoft said that it had detected a nation-state attack on January 12, 2024. The threat actor used password spray attacks to compromise a vulnerable account. They then used this initial access to create multiple OAuth applications and target Microsoft corporate email accounts.
The company has released few further details about the nature of the compromise, other than to note that the attackers used residential proxies to obfuscate the source of the attack. The technique involves routing traffic through a large number of IP addresses that are also used by legitimate users. The high change over rate of IP addresses makes it difficult for non-behavioral solutions to detect malicious traffic.
Meanwhile, in a filing to the SEC last Friday, HP said that a suspected nation-state actor it also believed to be Midnight Blizzard had gained unauthorized access to its cloud-based email environment.
The filing says that the company believes the activity is related to an intrusion from at least May 2023 in which a number of SharePoint files had been exfiltrated. It further stated that it had “determined that such activity did not materially impact the Company”, although again further details around the compromise remain undisclosed.
from SentinelOne https://ift.tt/aO9pUqg
via IFTTT
No comments:
Post a Comment