In this the fifth installment of our Detection Engine blog series, we examine the STAR Rules Engine and its role as one of five detection engines which work together as part of our cloud workload protection platform (CWPP) to detect, block, and respond to runtime threats impacting cloud workloads. (The first, second, third, and fourth posts in the series discuss the Static AI, Behavioral AI, Application Control, and Cloud Threat Intelligence Engines, respectively.)
- Static AI Engine
- Behavioral AI Engine
- Application Control Engine
- Cloud Threat Intelligence Engine
- STAR Rules Engine

STAR Rules Engine 101
Cloud workloads can create millions of security telemetry events daily. Security teams need an automated means of finding indicators of compromise (IOCs) lurking deep within that security data lake.
The STAR Rules Engine is a rules-based engine which enables users to transform queries of cloud workload telemetry into automated threat hunting rules. Whenever a match is made, these custom rules trigger alerts and, optionally, automated response actions. In this way, STAR rules become a force multiplier for security teams, equipping them to take swift action at scale in response to an ever-evolving threat landscape.
How Does It Work?
STAR rules apply custom detection logic which is immediately pushed either to every agent in the customer’s fleet or to a subset: it’s the customer’s choice. Each rule can be customized to suit the organization’s specific requirements. Users have the flexibility to choose between receiving alerts only or taking a mitigating response action such as matching process kill, network quarantine, and more. SentinelOne offers automatic mitigation options based on policy settings for suspicious or malicious threat confidence levels.
When a STAR rule matches inbound telemetry from the CWPP agent to the Singularity Data Lake, an alert is issued in near-real time. If there is a response action tied to the rule, the agent carries out that response on the Storyline tied to the telemetry event that made the match. STAR alerts can be found in the management console under Alerts and in the Activity log, ensuring that security practitioners remain informed. Threats are prominently displayed in the Threats section, providing a comprehensive overview of detected risks.
tied to the telemetry event that made the match. STAR alerts can be found in the management console under Alerts and in the Activity log, ensuring that security practitioners remain informed. Threats are prominently displayed in the Threats section, providing a comprehensive overview of detected risks.
Creating a STAR Rule
STAR rules can be created based upon any number of 200+ telemetry attributes. While that may sound daunting, creating a rule is done in 4 easy steps and with profound impact on SOC productivity.
STEP 1: Write a Query
The first step is to write a Singularity Data Lake query. This part represents the art of your threat hunting expertise. Early customers of Purple AI will find this step especially straightforward, as the GenAI allows natural language queries that are automatically translated to the appropriate SDL syntax.
Copy this query syntax to your paste buffer:
event.type == "File Modification" AND endpoint.os == "linux" AND tgt.file.path == "/etc/passwd"
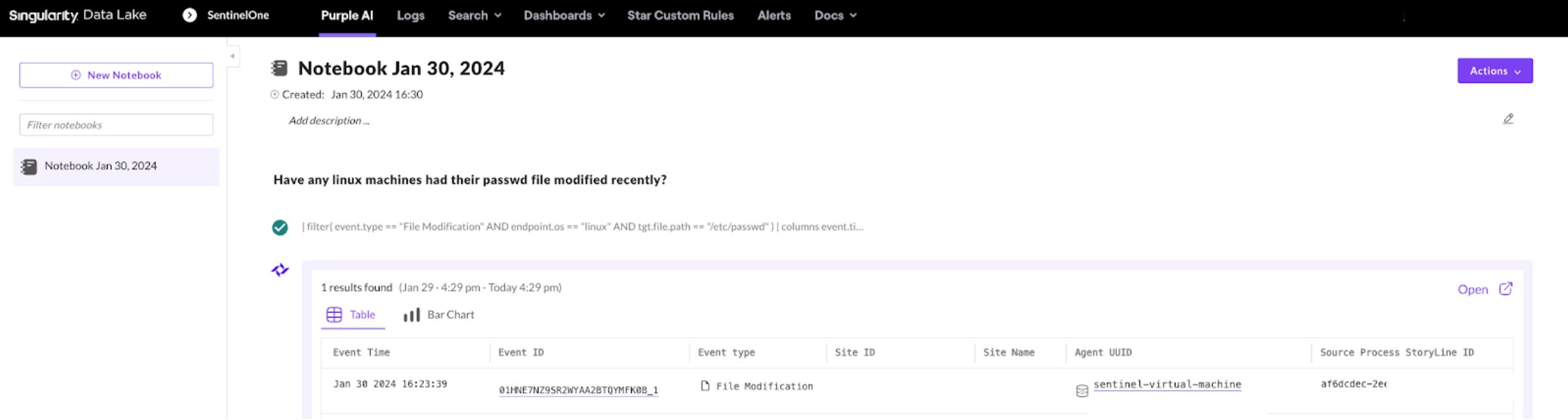
STEP 2: Create a New STAR Rule
Click ‘Star Custom Rules’ and then ‘New Rule’. Give the rule a unique name, description, and severity. Click ‘Next’ to go to the rule condition.
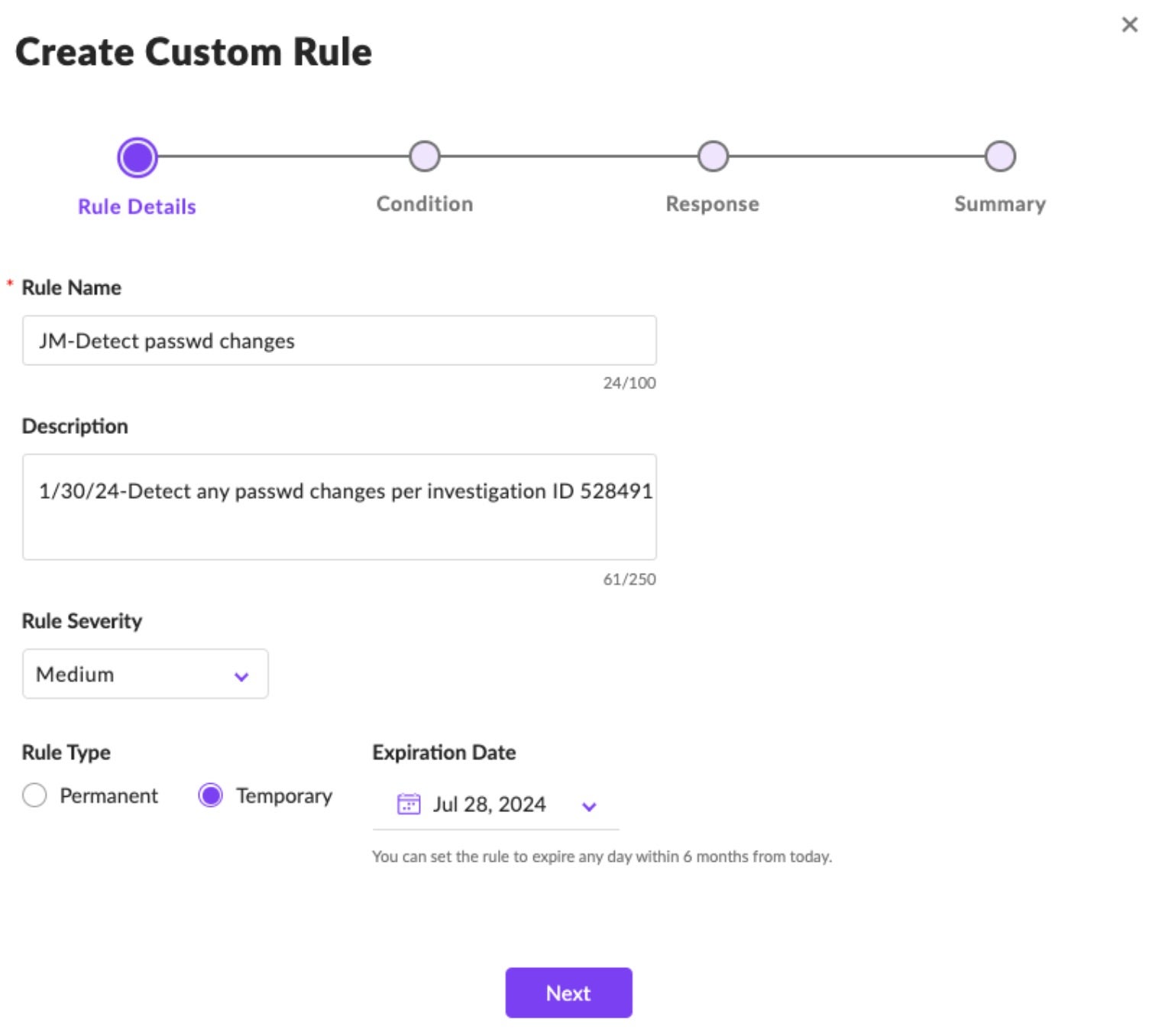
Set an appropriate scope, and then paste the query syntax from Step 1 into the rule. Click ‘Next’.
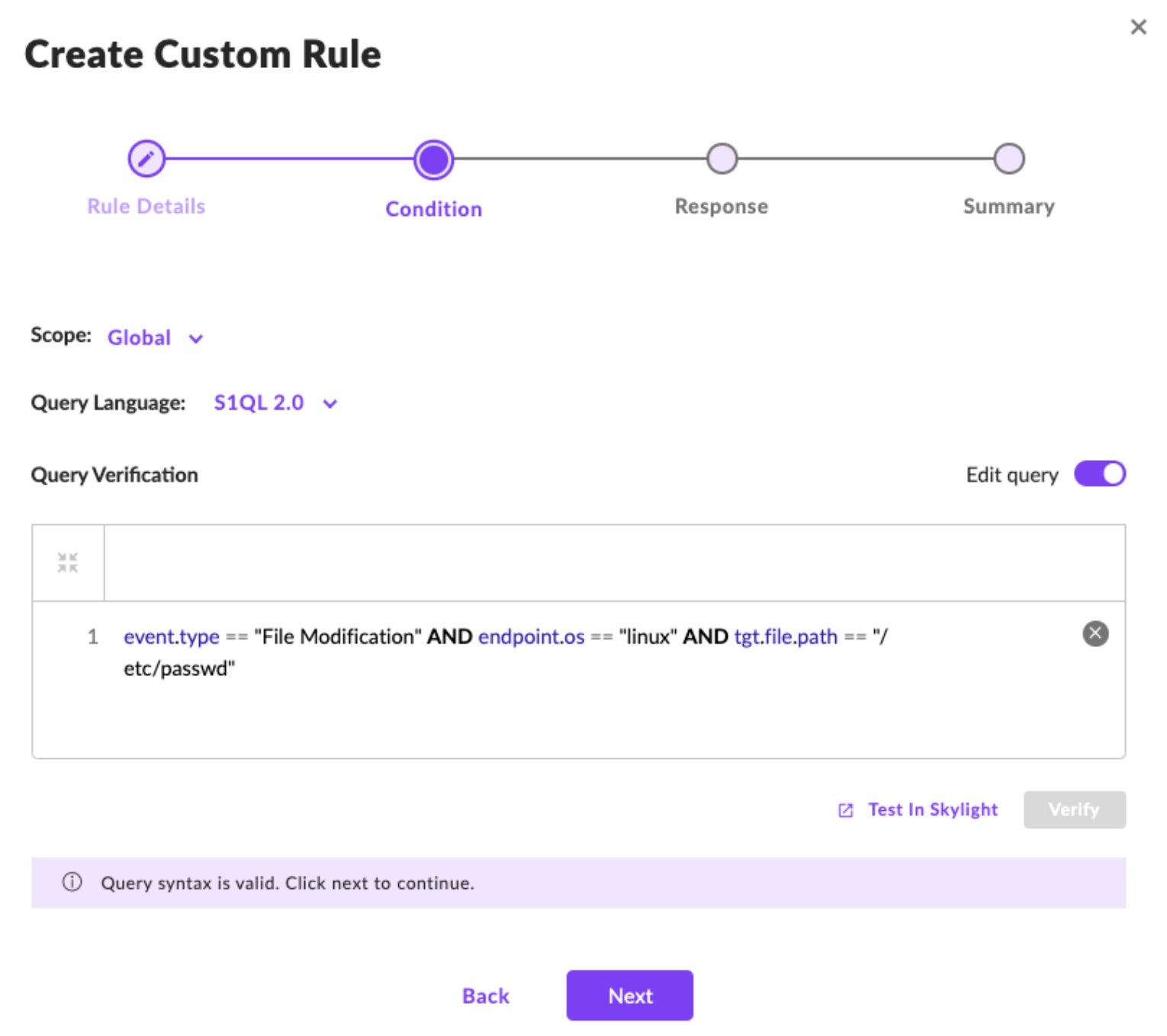
STEP 3: Add Response Actions
In short, what do you want to do when your rule matches a threat query? Do you wish to treat the detection as a suspicious or a malicious threat? If so, tick the box ‘Treat as a threat’ and select the appropriate choices, ‘Suspicious Threat Policy’ or ‘Malicious Threat Policy’. The automated response action is governed by the policy defined for the agent’s scope. Click ‘Next’.
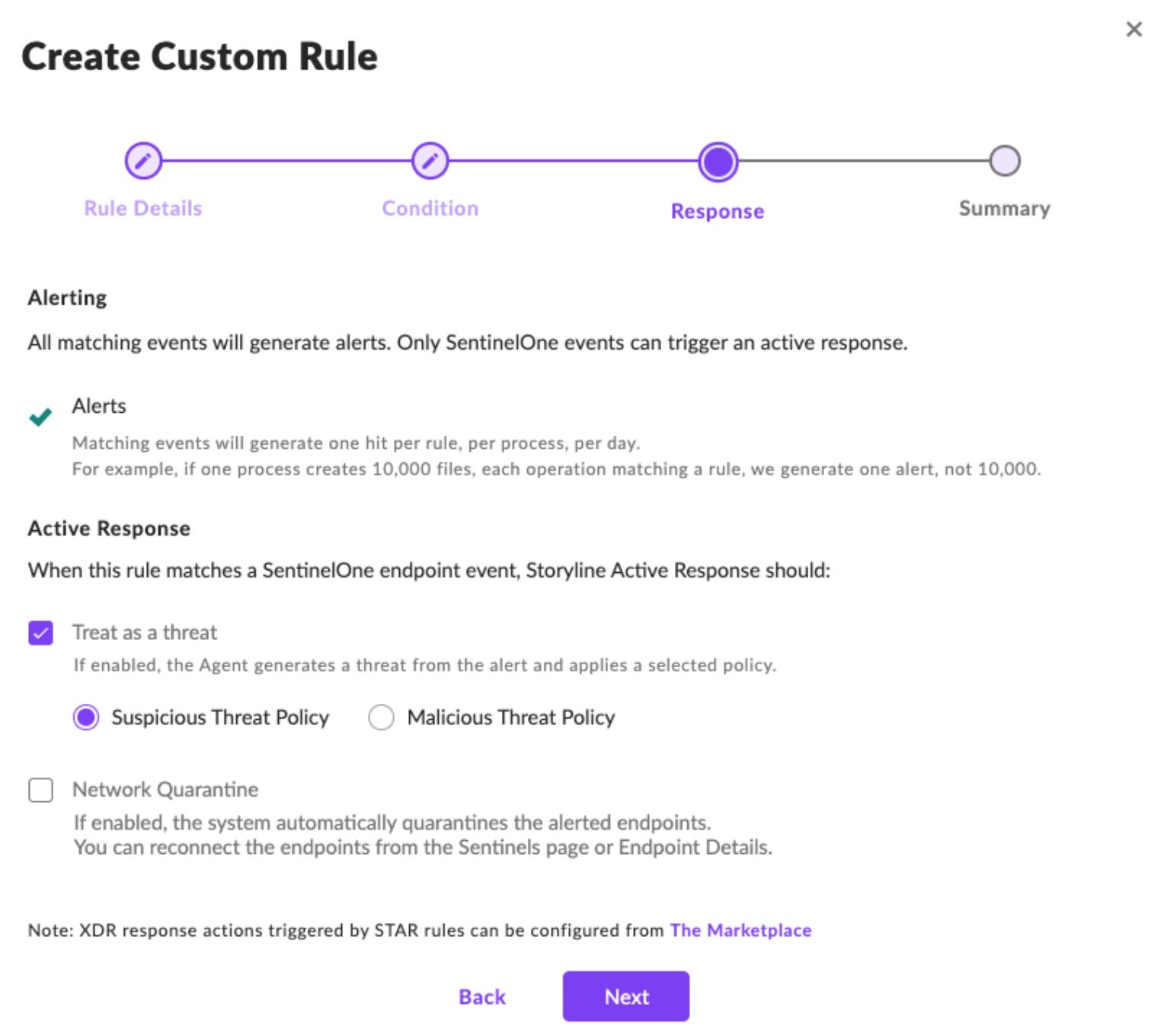
STEP 4: Save the Rule
In the Summary window, review the rule details. If you want the rule to be immediately active, tick the ‘Active rule immediately after saving’ box. If everything looks right, click ‘Submit’.
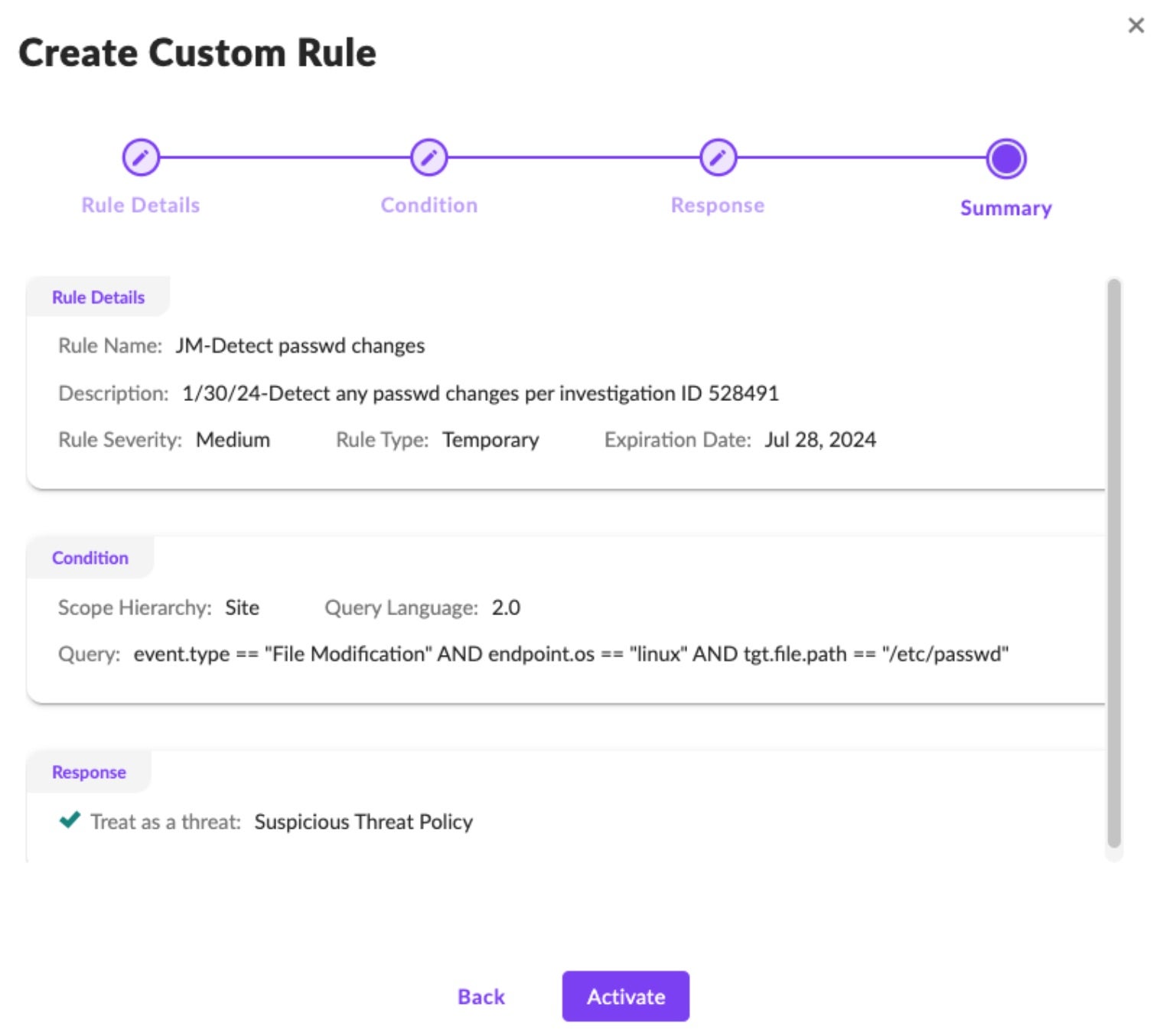
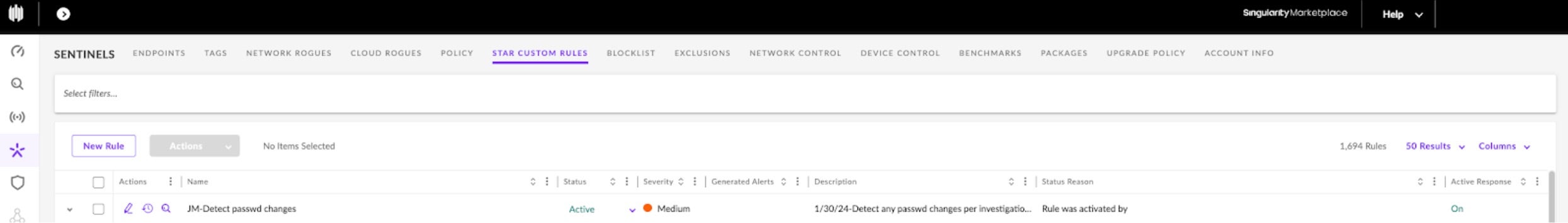
If creating a rule seems simple, great. That is the intention. A list of your custom rules can be found within the SentinelOne management console by navigating to Sentinels on the left navigation pane, and then selecting the STAR CUSTOM RULES tab as shown below. Here, we find the newly created rule, “JM-Detect passwd changes”. We will reference this rule later in the blog when we examine an example detection.
Best Practices for STAR Rules
Customers of Singularity Complete are entitled to use up to 100 STAR rules with the option to purchase additional rules in packs of 300 up to a maximum of 1000 STAR rules per customer.
To maximize the effectiveness of STAR rules, organizations should follow these best practices:
- Tune Queries for Accuracy: Firstly, be sure to fine-tune queries to generate a narrow and relevant list of true-positive matches. This ensures that alerts are focused on actionable threats. For example, if a query creates hundreds of results, narrow the time frame or add more search parameters to the rules to create more tightly focused results.
- Save Queries as Custom Rules: Convert successful queries into custom rules, allowing continuous monitoring and automated response.
- Iterative Rule Refinement: Let a STAR rule run for a period and then investigate its generated alerts (i.e., matches). Refine the rule to further narrow the results based on feedback and analysis so that the final match is laser-focused on the specific condition you desire. This iterative approach ensures optimal threat detection.
- Automated Mitigation: Once your rule is finely tuned and its results meet expectations, select an Auto Response to automatically mitigate identified threats. This proactive approach achieves bespoke, rapid cloud threat detection and response for your unique use case.
By following these best practices, organizations can harness the full potential of SentinelOne’s STAR rules.
Example: STAR Rule Detecting a Change to /etc/passwd
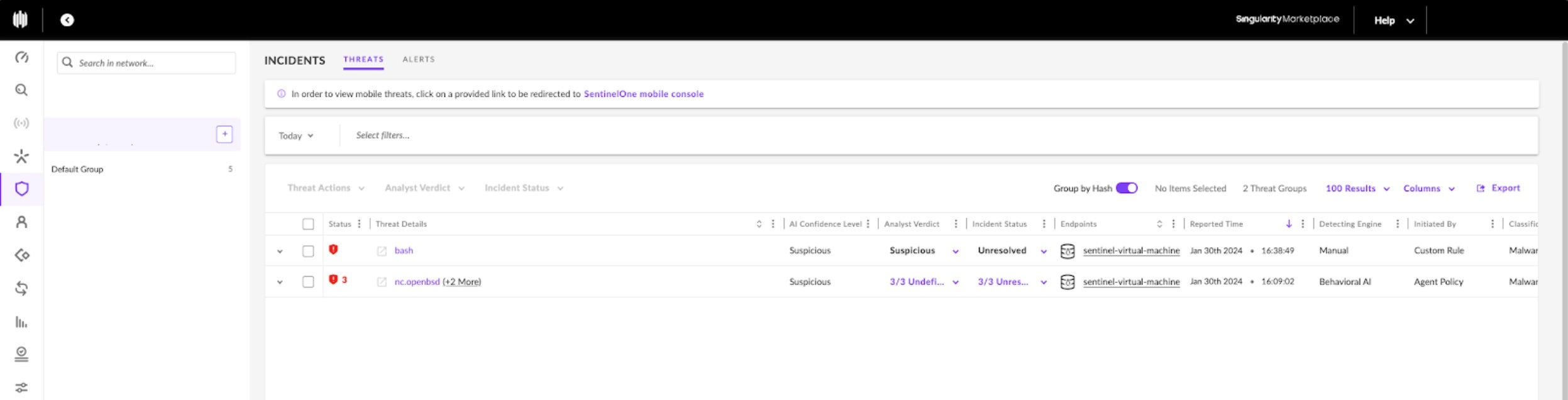
Earlier we created a STAR rule, “JM-Detect passwd changes”, which triggers a ‘Suspicious’ alert anytime a file modification was made on a Linux VM’s /etc/passwd file path. Now that the rule has been created, its custom detection logic is pushed to all CWPP agents within the scope.
Looking at the Incidents panel, we see two detections labelled ‘Suspcious’, one made by the STAR rule and which relates to a bash script.
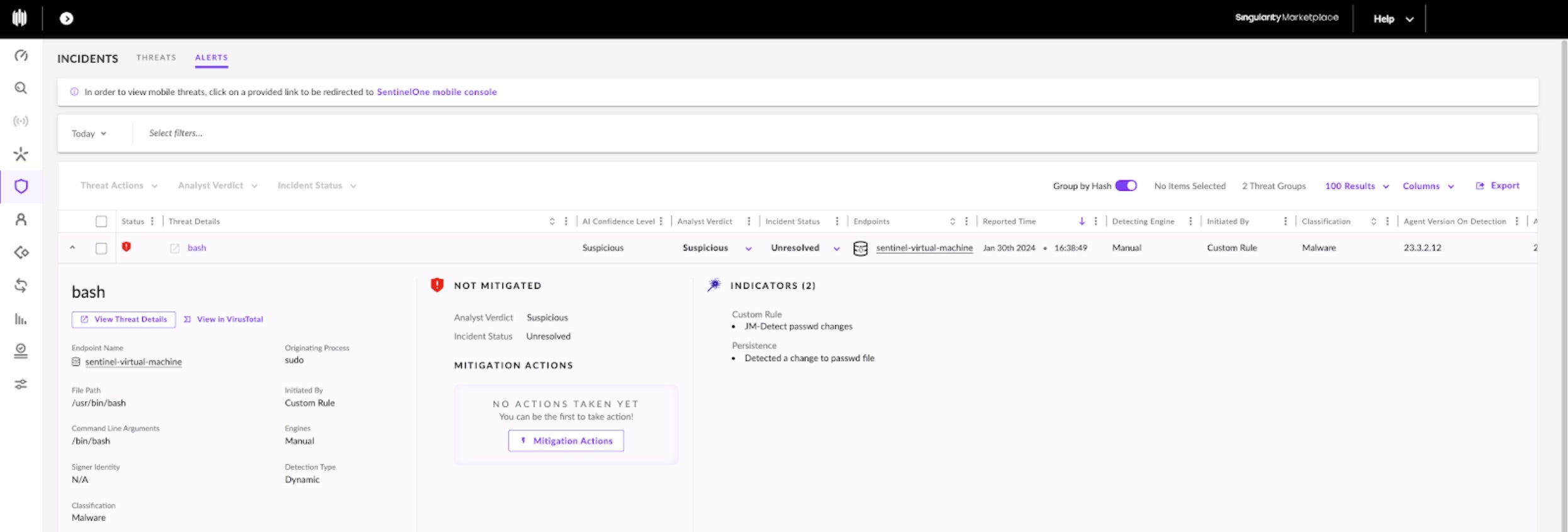
By clicking on the incident, we see expanded details. Here, a threat actor ran a bash script which began by escalating privileges via the sudo command, the originating process. The STAR rule detected a change to the VM’s passwd file.
Keep in mind that the rule was configured to use the Suspicious Threat Policy, which is Detect Mode, which is why the Incident Status is marked Unresolved or NOT MITIGATED. Had the rule been invoked under the Malicious Threat Policy and the policy set to take a mitigating action (such as process kill), the response action would have been automated, thereby offloading the overburdened security analyst.
Here again, we take a moment to emphasize the careful decision making behind the choice of automated response action. The flexibility and control are yours. The combination of agent and agentless cloud security capabilities are a powerful, transformative mechanism in creating better cloud security outcomes.
As a next step, the security analyst would surely initiate a mitigation action, which is easily done directly in the SentinelOne management console via the ‘Actions’ button in the upper right of the Incidents pane. Quite likely they would also open a security ticket, document their findings and actions, and inform the DevOps owner for this Linux VM.
Conclusion
One of five engines in SentinelOne’s real-time CWPP solution, the STAR Rules Engine triggers alerts on custom logic matching of security telemetry, as well as optionally automating prescriptive response action. In this way, the STAR Rules Engine becomes a force multiplier for the cloud security operations team. It works alongside the other local engines to deliver real-time cloud threat detection and response that far exceeds the limited abilities of agentless CWPP.
To learn more about the value of real-time, AI-powered CWPP in your cloud security stack, head over to the solution homepage, or see how Singularity Cloud Workload Security works with a 2-minute guided walk-through here. Whenever you are ready, connect with one of our cloud security experts for a personalized demo.
from SentinelOne https://ift.tt/AYbzq52
via IFTTT
No comments:
Post a Comment