The Good | LockBit Ransomware Gang Locked Down & Chinese Cyber Espionage Ecosystem Exposed
The cybersecurity community saw two valuable developments this week, the first being a hard-won shut down of the notorious LockBit infrastructure, and the second, a rare glimpse into the inner workings of China’s cyber espionage operations.
LockBit has long plagued victims across several critical industries, costing $91 million in losses within the U.S. alone since 2020. In a collaborative effort involving law enforcement from 11 countries and Europol, Operation Cronos dealt a significant blow to the ransomware gang.

Authorities were able to seize multiple darknet domains operated by the gang, disrupting the primary infrastructure that enabled their Ransomware-as-a-Service (RaaS) model. The joint operation also resulted in the arrest of two LockBit operators, the freezing of over 200 cryptocurrency accounts associated with the group, and the development of a LockBit 3.0 Black decryptor tool available for free. The U.S. State Department is also offering up to $15 million in rewards for information leading to the apprehension of key LockBit leaders, group associates, or ransomware affiliates.
In other news, cyber defenders are getting a unique peek into China’s state-sanctioned cyber espionage efforts, which has fostered a competitive marketplace of independent contractor hackers-for-hire over the years. I-Soon, a PRC-contracted company, suffered a data leak where thousands of client-employee messages and dozens of marketing materials were published anonymously on GitHub. While details surrounding the origin and authenticity of the leaked content are ongoing, the event offers much insight into Chinese offensive operations and gives defenders an opportunity to improve their cyber defenses and better understand mature operators within the greater cyber threat domain.
The Bad | Critical ConnectWise ScreenConnect RCE Bugs Exploited in the Wild
Warnings abound this week for ConnectWise customers regarding two critical severity remote code execution (RCE) flaws within ScreenConnect. Tracked as CVE-2024-1708 and CVE-2024-1709, the flaws stem from an authentication bypass weakness in the popular remote monitoring and management (RMM) software, allowing unauthorized access or arbitrary code execution.
It seems that attackers have wasted no time. Just a day after the initial disclosure and with technical details and proof-of-concepts circulating online, both vulnerabilities are confirmed to be under active exploitation. In the case of CVE-2024-1709, an attacker can send specially crafted requests within affected versions to trigger the setup wizard, even when the software is already set up, before creating a new administrator account to take control of the ScreenConnect instance.
Somewhat interesting that only the Windows build of ConnectWise ScreenConnect got a fix.
I hope the vendor has evidence that there's not an individual on the planet that runs the Linux or Mac build of the software.
pic.twitter.com/Zs7wwc6GaP
— Will Dormann (@wdormann) February 22, 2024
Leveraging the path traversal flaw, CVE-2024-1708, an attacker can access or modify files outside of the intended restricted directory. If exploited in tandem, use of both flaws enable attackers to access and manipulate sensitive files and, subsequently, upload their malicious payload outside of the ScreenConnect subdirectory. In the wake of the active exploits, ConnectWise has removed all license restrictions and continues to urge users to update on-premise servers to version 23.9.8 at minimum.
Recent advisories from CISA, NSA, and MS-ISAC highlight the increasing misuse of legitimate RMM software like ScreenConnect for malicious purposes. RMM applications can be used as backdoors for persistence or command and control (C2). Network defenders are reminded to regularly audit remote access tools for abnormal use, patch on time, and put proactive security measures in place to detect intrusions and potential breaches.
The Ugly | German Elections Under Threat by Russian-Linked Influence Operations
SentinelLabs and ClearSky Cyber Security this week unveiled a substantial propaganda and disinformation campaign believed to be orchestrated by a Russia-aligned influence operation network dubbed Doppelgänger. Initiated in late November 2023, the campaign initially targeted Ukrainian affairs but has since expanded its reach to audiences in the United States, Israel, France, and Germany.
Findings from both SentinelLabs and ClearSky expand on Doppelgänger’s rising efforts in spreading disinformation. Most recently, the network’s activities currently focus on employing propaganda and disinformation tactics to influence public opinion, particularly regarding socio-economic and geopolitical matters relevant to targeted German audiences.
Doppelgänger’s latest campaign concentrates on criticizing the ruling government coalition’s support for Ukraine, potentially with the aim of influencing public sentiment ahead of imminent elections. This discovery correlates with latest reports from the German Ministry of Foreign Affairs and Der Spiegel media outlet, which have also raised alarms about potential election interference within Germany.
Doppelgänger’s modus operandi involves an extensive network of social media accounts, primarily on X (formerly Twitter). Network operators also engage in coordinated activities to amplify their messages through a sophisticated infrastructure, including a network of websites hosting propaganda articles designed to mimic legitimate news outlets, coupled with evasion tactics.
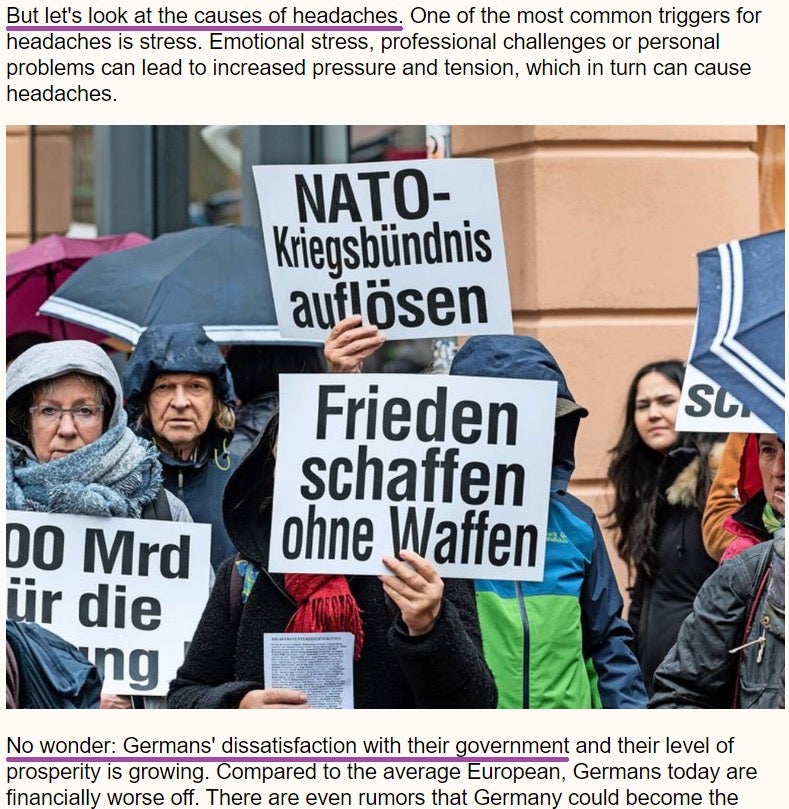
With major elections on the horizon across the EU and the United States, the persistence and evolving nature of Doppelgänger’s campaign speak to more cases of information warfare to come. As threat actors continue to exploit media and trending geopolitical and socio-economic current events, a combination of public awareness campaigns, social media literacy programs, and effective social media security policies will be much needed to minimize the threat of propaganda and disinformation online.
from SentinelOne https://ift.tt/k8HQ3Cx
via IFTTT
No comments:
Post a Comment