For millions of organizations today, source code management platforms like GitHub play a fundamental role in software development, operating as a central hub for both proprietary and open-source code repositories, enabling collaboration, version control and continuous integration and deployment (CI/CD).
In this blog post, we explore the less-discussed side of these essential platforms, where threat actors leverage their features for malicious activities, to stage cyber attacks and steal sensitive data. By understanding the ways threat actors abuse such platforms, organizations can better equip themselves to protect their repositories and mitigate the potential risks associated with code sharing and CI/CD platforms.

Current Threat Landscape | SaaS Abuse On the Rise
The compromise of open-source software projects is becoming more prevalent, with threat actors targeting libraries distributed via package managers and public repositories like PyPI, Crate.io, and GitHub. After infiltrating these trusted resources, threat actors can inject vulnerabilities into widely-used software, potentially compromising the security of many more associated applications and systems.
Beyond the cyber threat on open-source platforms, a broader trend has emerged: Legitimate internet services and critical platforms are frequently exploited by threat actors for malicious activities. GitLab and BitBucket, used for source code management and version control, have also suffered from bugs leading to opportunities for threat actors to gain access to sensitive data, propagate malware, and orchestrate various forms of cybercrime.
Notable Cases of Recent Repo Hacks
Some prominent cyber attacks that leveraged shared code repositories include:
- Pro-Russia hacktivist group NoName057(16) made headlines by leveraging GitHub to host its toolkit and enticing key contributors with payments.
- The Rust development community fell victim to the CrateDepression supply-chain attack, which specifically targeted organizations using GitLab Continuous Integration (CI) pipelines.
- The 3CX SmoothOperator supply chain attack involved pulling encrypted C2 details hidden in icon files hosted in a dedicated GitHub repository.
- The recent ‘everything’ package prank exposed the potential for GitHub to be used in denial-of-service attacks, highlighting the broader repercussions of such abuse on global software ecosystems.
- Secret Gists and
git commitcommands have been used to deliver C2 commands and retrieve malware payloads. - A GitHub leak reported earlier this year impacted major brands like Toyota, Mercedes Benz, Binance, and X (formerly Twitter), exposing sensitive proprietary code and credentials.
1. Hosting Malware & Phishing Campaigns
The most obvious misuse of code sharing platforms is hosting malware in plain sight. Threat actors create repositories that appear benign at first glance but can be used to trick developers into downloading and executing code that holds malware or facilitates phishing schemes. Poisoned projects can help attackers reach far more victims if developers unwittingly build bad code into legitimate software, as well as target specific enterprises.
Robust code review processes are essential for detecting malicious code within repositories. Automated scanning tools can further enhance security by identifying known malware signatures and suspicious patterns. To combat the risk of phishing, educating developers and users about common schemes is crucial, especially when users are interacting with code from untrusted sources.
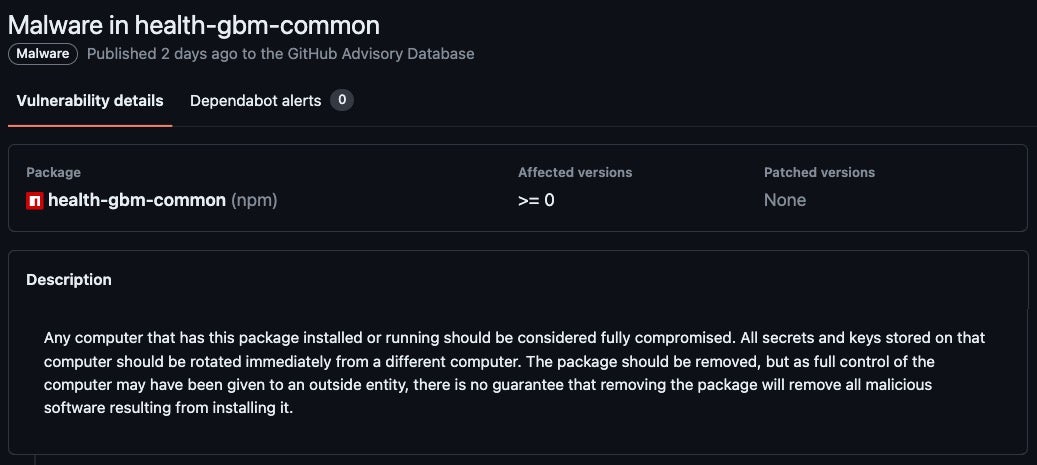
2.Hosting Command & Control (C2)
Public repositories can serve as a strategic platform for threat actors to distribute or host command-and-control (C2) servers, or more commonly to serve as channels by which to distribute C2 URLs, fallback commands or configuration files.
The ability to blend in with legitimate network traffic and sidestep domain block lists makes public code repositories highly attractive. In addition, high uptime and ubiquity of the services make GitHub and similar platforms ideal for attackers’ decentralized C2 infrastructure. Tactics such as dead drop resolvers and obfuscated domains embedded within web services help adversaries to obscure back-end C2 infrastructure from discovery through malware binary analysis.
Organizations can implement network traffic monitoring and anomaly detection systems to help identify unusual patterns indicative of C2 communication. Additionally, leveraging threat intelligence feeds to block known malicious IP addresses and domains associated with C2 infrastructure can enhance defense mechanisms. Defenders should also conduct regular auditing and proactively revoke access for suspicious accounts or repositories.
3. Credential Theft & Supply Chain Attacks
Code repositories have become a prime target for threat actors targeting credential theft and supply chain attacks.
Git repositories can contain not only proprietary code but also sensitive credentials like API keys, passwords, and cryptographic keys.
To defend against such risks, organizations can adopt robust authentication mechanisms such as multi-factor authentication (MFA) and OAuth to safeguard their user accounts and credentials. Implementing a secrets management solution can also support more secure storage and management of sensitive credentials, reducing exposure to potential attackers. Security leaders can also consider deploying code signing and verification mechanisms to ensure the integrity of software supply chains.
4. Cloning & Manipulating GitHub (& Other) Repos
Adversaries may inject malicious code directly into exposed libraries or submit fraudulent pull requests, introducing backdoors, executing code injection attacks, or leverage proof-of-concept code, often itself hosted on public repositories like GitHub.
Attackers have been seen cloning GitHub repositories and adding malicious code to forks designed to infect developer systems and pilfer sensitive files that included software keys.
In another case, suspicious commits in hundreds of GitHub repositories were discovered to be carrying malicious code. All of the commit messages were created by attackers to disguise their exfiltration of secrets to a C2 server before they injected web-form password-stealing malware into JavaScript files.
Regularly updating and patching dependencies is critical for addressing known vulnerabilities and security issues. Security defenders are also advised to stay informed on emerging security alerts providing updates related to third-party libraries used by their organizations.
Software composition analysis (SCA) tools can enhance security by scanning repositories for vulnerable dependencies and automating remediation or flagging issues for manual review.
5. Abuse of GitHub Actions & CI/CD Pipelines
Threat actors have exploited GitHub’s continuous integration/continuous deployment (CI/CD) pipelines and automation features, such as GitHub Actions, to automate malicious activities and orchestrate attacks. By leveraging these capabilities, they deploy malware, exfiltrate data, or execute unauthorized commands within CI/CD workflows.
To combat these risks, enforce least privilege access controls to restrict the execution of CI/CD workflows and automation scripts and reduce the attack surface. Pre-defined templates and secure coding practices can also help prevent injection attacks and unauthorized code execution.
Security teams may also adopt logging and auditing features in order to more thoroughly track changes and activities within CI/CD pipelines. GitHub’s guide to security hardening for GitHub Actions provides further advice, as does CISA’s guide on how to defend CI/CD environments.
6. Distributed Denial of Service (DDoS) Attacks
Public hosting infrastructure and version control systems have been increasingly exploited to orchestrate distributed-denial-of-service (DDoS) attacks. Flooding repositories or services with a high volume of requests disrupts normal operations, degrades performance, and renders services unavailable to legitimate users.
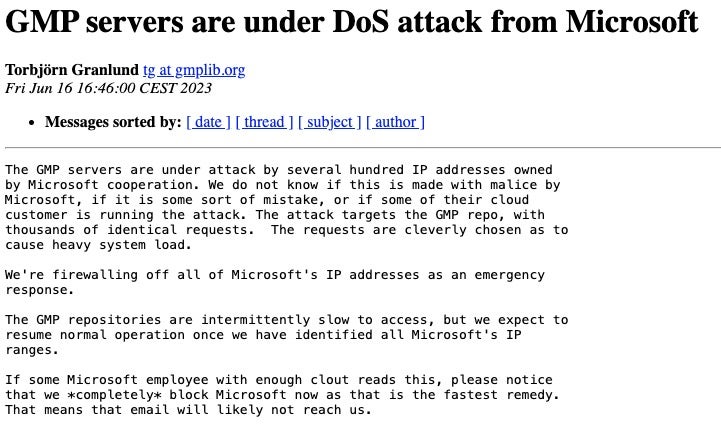
In the case of the GMP project, an open source arithmetic library, servers came under attack by several hundred IP addresses owned by Microsoft, causing a surge of network traffic and slowed associated programs linked to the library to a crawl.
Deploying web application firewalls (WAFs) and implementing rate limiting mechanisms can help mitigate DDoS attacks targeting public repositories and services. Content delivery networks (CDNs) can enable organizations to distribute traffic and absorb volumetric attacks, reducing the impact on GitHub’s infrastructure.
Security teams are also recommended to implement network-level defenses such as traffic filtering and IP reputation blocklisting, which aid in preventing malicious traffic and safeguarding public infrastructure from disruption.
Conclusion
Defending Continuous Integration/Continuous Delivery environments is an essential part of an enterprise’s security posture. Implementing least privilege access controls to restrict unauthorized actions, prioritizing on regularly updating and patching dependencies are key to mitigating vulnerabilities, along with enforcing strong authentication mechanisms to protect user accounts and credentials for resources hosted on source code management platforms.
Utilizing threat intelligence feeds and security monitoring tools designed to proactively identify and respond to suspicious activities are also key to minimizing the risk of exploitation and data breaches. Solutions like XDR can play a large role in protecting organizations from cyber threats originating from public infrastructure abuse and exploitation by providing comprehensive visibility, advanced analytics, automated response, and centralized management capabilities.
Learn more about Singularity XDR by booking a demo with us today, or contacting our expert team directly.
from SentinelOne https://ift.tt/67vJEHx
via IFTTT
No comments:
Post a Comment