Securing critical data is a vital security focus for IT ops and SecOps. Data is exploding at an unprecedented rate. Arguably, it is the target of most cyberattacks to either hold data hostage, leak it, or otherwise intentionally expose it for nefarious processes. Let’s look at zero-trust principles and how organizations can implement better data security using a multi-layer strategy.
Principles of zero trust
Organizations worldwide are recommended to adopt an ideology called zero trust. With zero trust, several methodologies help to protect your data. Note the following directives with zero trust:
- You need to verify everything explicitly
- There are no assumed “trusted” devices or users
- Assume that you have a hacker in your network. Yes, seriously, you need to assume your environment is breached, which helps to set the expectations for handling security
If you can apply these principles to your data, it will accelerate your adoption and move to a zero-trust environment.
Understanding data states
One of the essential concepts to understand when dealing with data security is that data exists in different states. Depending on the state the data is in, different means may be available or used to protect your data from breaches. Note the following:
- Data in transit
- Data in use
- Data at rest
When data is transmitted across the network, it is considered in transit. When data moves, it can be potentially exposed to risks and vulnerabilities within the local network or across the Internet. Encryption “in-flight” is often used to encrypt data as it moves across the network.
Data in use is data that is being actively accessed or used. When data is in use, it can include reading, processing, or making changes. When you think about data “at risk”, this is truly what data in use is. After all, it is open to the user and the app they are using to interact with the data. Organizations can implement data protection policies to help protect data that is used or accessed.
Data at rest is data that is inactive. When data is not being used or moving across the network, it is at rest on storage. In this state, it is at less risk than when it is being used, in motion, or in transit. At-rest disk encryption ensures that data stored on disk is encrypted.
Classify and discover your data
When thinking about data security, it is important to discover and classify all data assets. Organizations are amassing large amounts of data, and this trend is growing exponentially.
Due to the enormous amount of data, businesses can’t discover and classify all data using manual means. Instead, automated data discovery and classification tools, along with a few manual methods, are critical.
Automated discovery and classification tools like those in Microsoft 365 solutions allow organizations to discover and classify data using automation. It puts them in a much better position to explicitly implement a zero-trust principle of verifying.
What is sensitive data?
Not all data is deemed as “sensitive”. Sensitive data usually falls into specific categories. It is important to realize that data may need to be protected differently depending on its status and whether it is deemed sensitive.
Sensitive data may also be different types of information for various organizations. However, sensitive data is generally any information you need to protect from unauthorized access. In addition to technology-based protections, physical security may also be needed.
Organizations may deem data sensitive due to the following:
- Personal privacy
- Regulatory or compliance requirements
- Intellectual property
- Ethical or legal requirements
Protecting sensitive data
With the enormous amount of potentially sensitive business-critical data, organizations must understand which data is sensitive and apply proper controls and access policies to this data. Again, you can’t correctly control or create access policies if you don’t first classify and discover your data with the right tools.
Tools like Microsoft 365 have sensitivity labels that essentially apply a virtual stamp on a piece of data that denotes sensitive data. These sensitivity labels are like metadata that isn’t visible to the apps that consume the data but can be easily integrated into zero-trust workflows.
For instance, once a sensitivity label is applied to an email, document, invite, or other data, the protection settings configured for the sensitivity label are automatically applied. These labels may be used to:
- Control access to content or apply encryption
- Mark the content as sensitive
- Protect content in containers
- Apply labels automatically to files and emails
- Set default link types
Below is a sensitivity label applied to an email message.
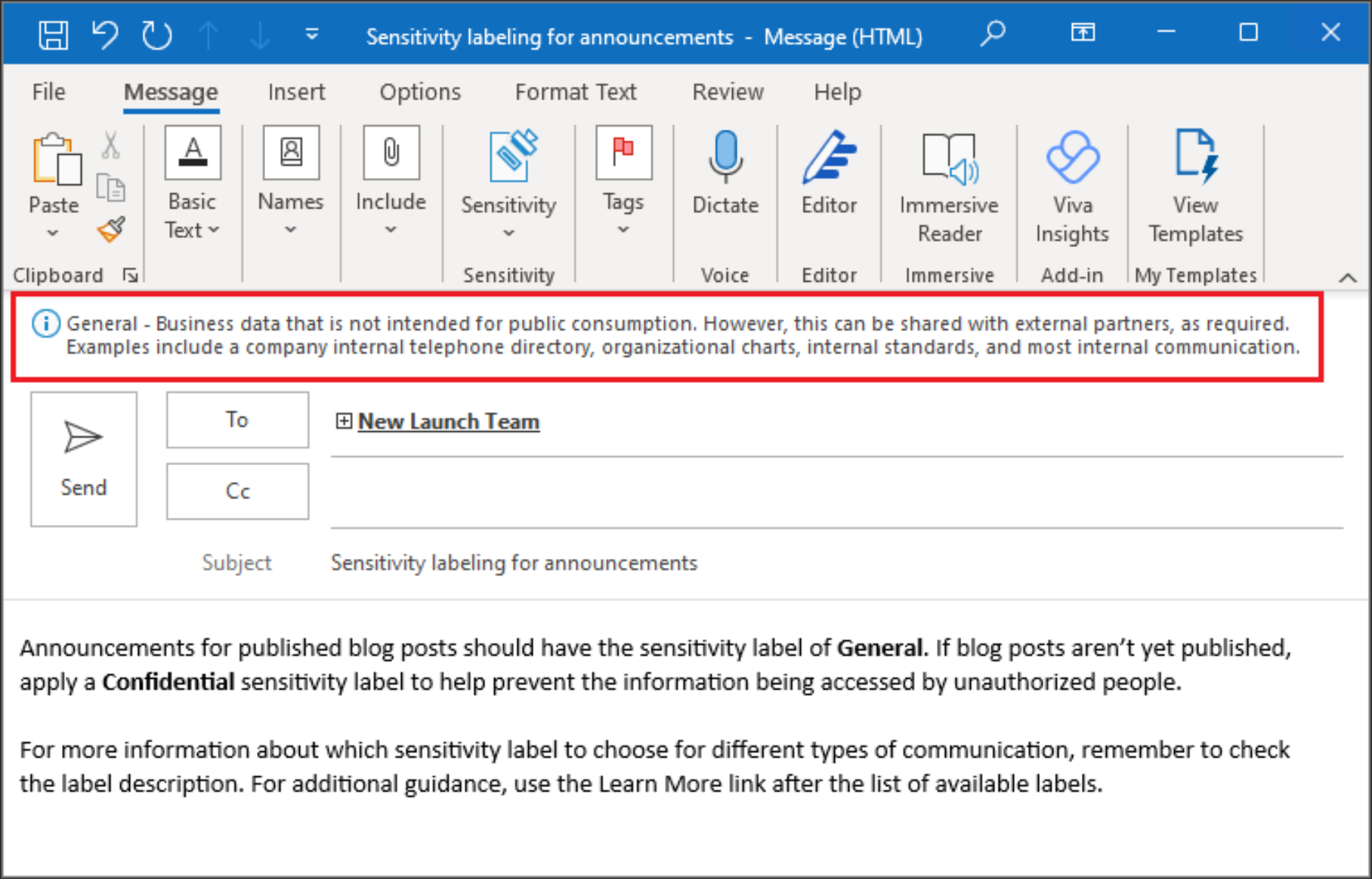
Data loss prevention
A crucial part of protecting sensitive data is ensuring that users do not inappropriately share sensitive data with those who shouldn’t have access to it. The practice of making sure others don’t have access to sensitive data and users can’t overshare this type of data is called data loss prevention (DLP).
Again, only manual attempts by administrators to prevent improper sharing generally come up short. Today, organizations leveraging SaaS solutions like Microsoft 365 need automated solutions for DLP.
Microsoft Purview is Microsoft’s solution in M365 that allows admins to apply policies to define how data is identified, monitored, and protected.
Purview uses deep content analysis to understand the true nature of the content and not just a simple text scan. What does the content analysis use to determine whether or not data is sensitive?
- Keywords for primary data matches
- Regular expressions and internal function validation
- Secondary data matches that are close to the primary data match
- Machine learning algorithms to detect content that matches DLP policies
Microsoft Purview is a solution that is available for setup from your Azure Portal and allows onboarding your environment into Purview for DLP policies.
Here is an example of alerts generated with a policy match on an end-user client machine.
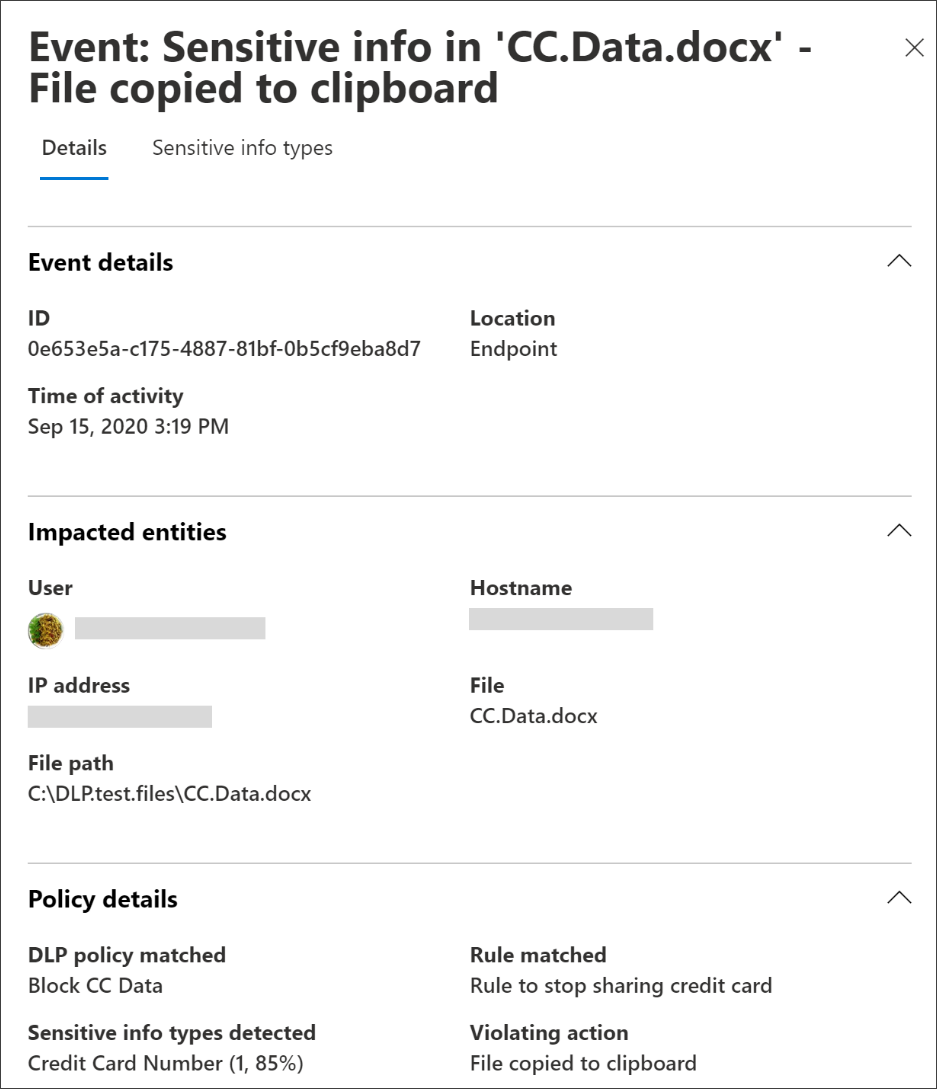
Depending on which DLP controls Microsoft service, there is some disparity between how the DLP scans run in the Microsoft 365 cloud.
For example, in SharePoint and OneDrive, DLP scans existing and new items and generates alerts when matches are found with a DLP policy. In Exchange, only new emails are scanned, and an alert is generated if a DLP policy matches. It does not scan previous emails.
BitLocker encryption
Another core data security requirement is ensuring data at the endpoint is secured. BitLocker is a standard encryption solution from Microsoft that encrypts entire volumes of data. BitLocker encryption helps to ensure that data remains secure if the device is lost or stolen or is not properly recycled.
Data is inaccessible due to the BitLocker encryption in place, even if the drive is moved to another computer or an attacker runs a software tool against the drive.
Modern BitLocker encryption also works with the Trusted Platform Module (TPM) to help further secure data. With the TPM device, BitLocak can lock the machine startup process until a PIN is supplied from a user or a startup key is inserted.
Device encryption is a new feature in Windows that allows BitLocker encryption to be enabled automatically. Unlike traditionally enabling BitLocker, device encryption is enabled automatically to protect the device. BitLocker is initialized on the OS drive as part of a clean installation of Windows that supports the Modern Standby or HSTI security requirements.
Wrapping up
Modern data security requires organizations to consider many aspects of their data security strategy. It starts with understanding what data you have, where it is located, whether it is sensitive, and automating much of this process using robust technology tools. Also, tools like Microsoft Purview can be used to apply DLP policies and BitLocker encryption to secure data at rest and on end-user client devices. Data is the new gold, and only organizations that use and protect it correctly will succeed and thrive.
from StarWind Blog https://ift.tt/nbRMQga
via IFTTT
No comments:
Post a Comment