This week, SentinelOne launched Singularity Cloud Native Security (CNS), our agentless Cloud Native Application Protection Platform (CNAPP) uniquely designed to assess cloud environments through the eyes of a threat actor. As attackers increasingly target cloud environments, SentinelOne’s latest solution helps organizations better defend against these attacks.
Cloud Native Security (CNS), our agentless Cloud Native Application Protection Platform (CNAPP) uniquely designed to assess cloud environments through the eyes of a threat actor. As attackers increasingly target cloud environments, SentinelOne’s latest solution helps organizations better defend against these attacks.
CNS simulates attack methods to verify exploit pathways, so-called Verified Exploit Paths . In so doing, CNS reduces the noise of the theoretically possible so that cloud security practitioners can focus on fixing what matters most.
. In so doing, CNS reduces the noise of the theoretically possible so that cloud security practitioners can focus on fixing what matters most.
In this blog post, Ely Kahn, VP of Product Management for Cloud Security, AI/ML, and Core Platform, and Anand Prakash, Product Leader for SentinelOne’s Cloud Native Security, explore the value and outcomes of Cloud Native Security. Learn how our agentless CNAPP with a unique Offensive Security Engine is set to help security, developers, and cloud teams collaborate and communicate to radically reduce their cloud and container attack surfaces.
is set to help security, developers, and cloud teams collaborate and communicate to radically reduce their cloud and container attack surfaces.

Think Like An Attacker | The Vision for Cloud Native Security (CNS)
Ely: Anand, could you outline our overall vision for Cloud Native Security (CNS)?
Anand: For me, Cloud Native Security (CNS) is cloud security that Thinks Like An Attacker.
As organizations build and run their multi-cloud and container environments there are many security concerns: OS and application level vulnerabilities, misconfigured cloud services, overly permissive cloud identities, misconfigured container deployments, leaked credentials … the list goes on. Aside from meeting compliance needs and building cross-functional collaboration workflows with other teams, cloud defenders must ensure visibility across the entire estate to build and enforce security policies. They simply have too much to do and insufficient time or resources. On the other side, attackers have a single and clear remit: to find ONE way in.
Cloud Native Security provides a unified view of all the risks listed above and, importantly, applies an attacker’s mindset to a cloud attack surface to highlight which areas of cloud insecurity represent genuinely exploitable risks. CNS communicates the critical areas of your cloud environment where there’s immediate exploitation potential, providing evidence with screenshots and code snippets. We call these Verified Exploit Paths .
.
Sometimes, a CVSS score isn’t sufficient to communicate a risk’s impact. Understanding hundreds of potential theoretical Attack Paths wastes everybody’s time investigating never-exploitable threats. CNS focuses on providing evidence, which not only means no false positives, it helps cloud security teams effectively work with their peers to remediate cloud issues rapidly.
Ely: That autonomous attacker’s mindset is extremely valuable to customers. I think it’s worth talking about how that’s achieving several things for security teams including:
- Identifying which risks are exploitable and which require alert prioritization
- Validating the nature of the risk and providing evidence of the attack vector, which automates the finding deconfliction process
- How the provision of evidence speeds up remediation by providing all teams the “so what” that’s often required to drive action
Now that we’ve got the bigger picture, let’s talk about how Cloud Native Security achieves this.
Instant Visibility and Coverage
Anand: Let’s start with how we first engage with our customers, the onboarding process.
As an agentless CNAPP, CNS onboarding takes minutes, and results are immediate. CNS is an incredibly efficient onboarding wizard that steps customers through onboarding their multi-cloud environments. It provides templates to deploy, and within minutes, allows customers to set up read-access across AWS, Microsoft Azure, Google GCP, Oracle Cloud, Alibaba Cloud, and Digital Ocean.

That’s all CNS requires to return with immediate observability and comprehensive security across cloud infrastructure within minutes. Additionally, CNS automatically detects new accounts, projects, and subscriptions as they’re spun up. This is very important to ensure our customers have complete visibility of their ever-changing estate.
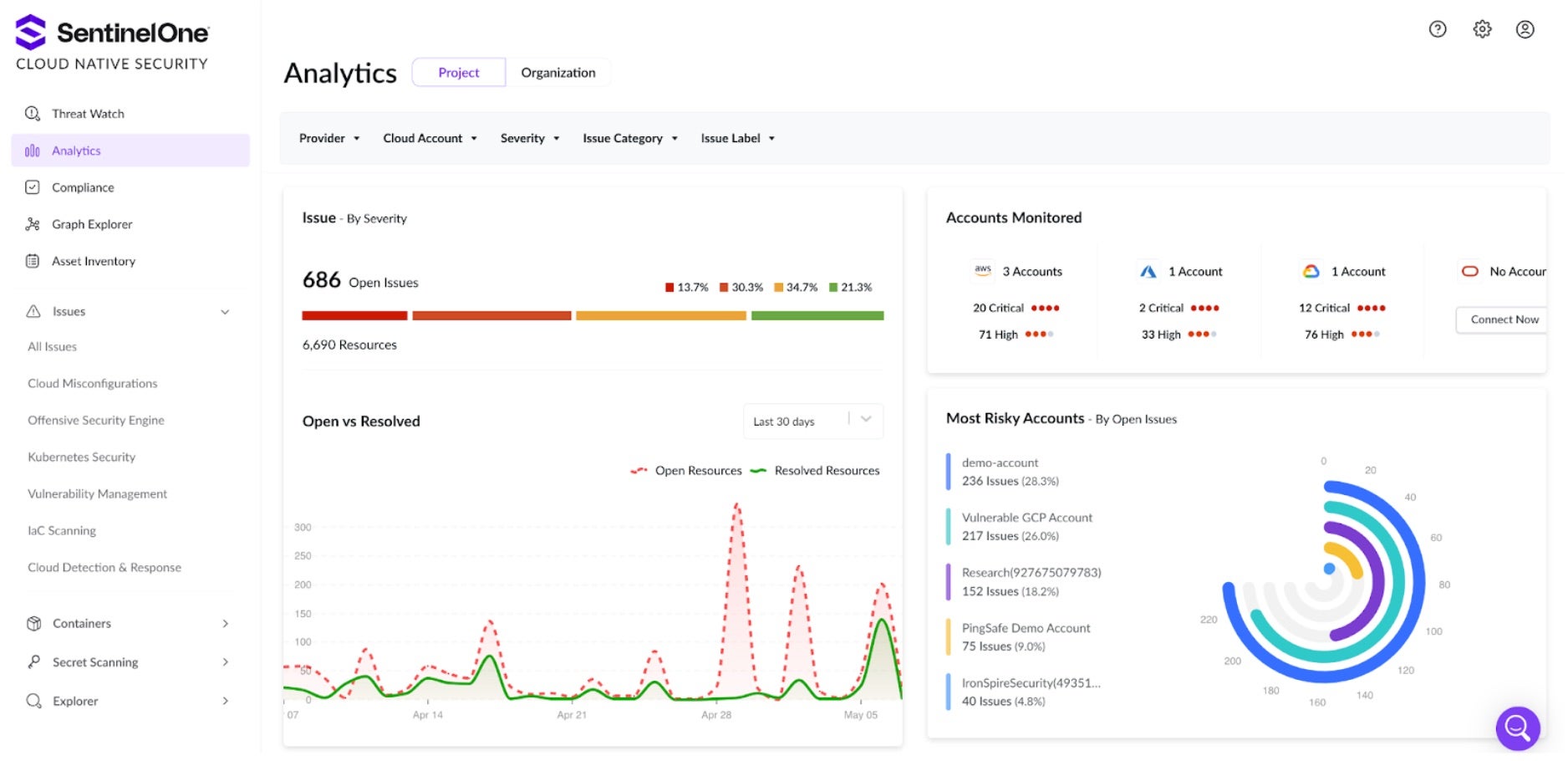
Based on feedback from our customers, they describe a struggle with cloud asset sprawl or, “shadow cloud”. This visibility is the start of all security for me, as you can’t protect what you can’t see, or don’t know if it exists!
CNS provides a full cloud Asset Inventory and an easy-to-navigate graph explorer of the cloud environment. The image below shows the SentinelOne Graph Explorer, which visually analyzes cloud resources. All security issues have a pre-built link view of the potential blast radius of cloud resources affected by an identified vulnerability or misconfiguration. It’s also a convenient and visual method of writing queries or creating custom policies. Any search and view can be converted to reusable security policies in a few clicks.
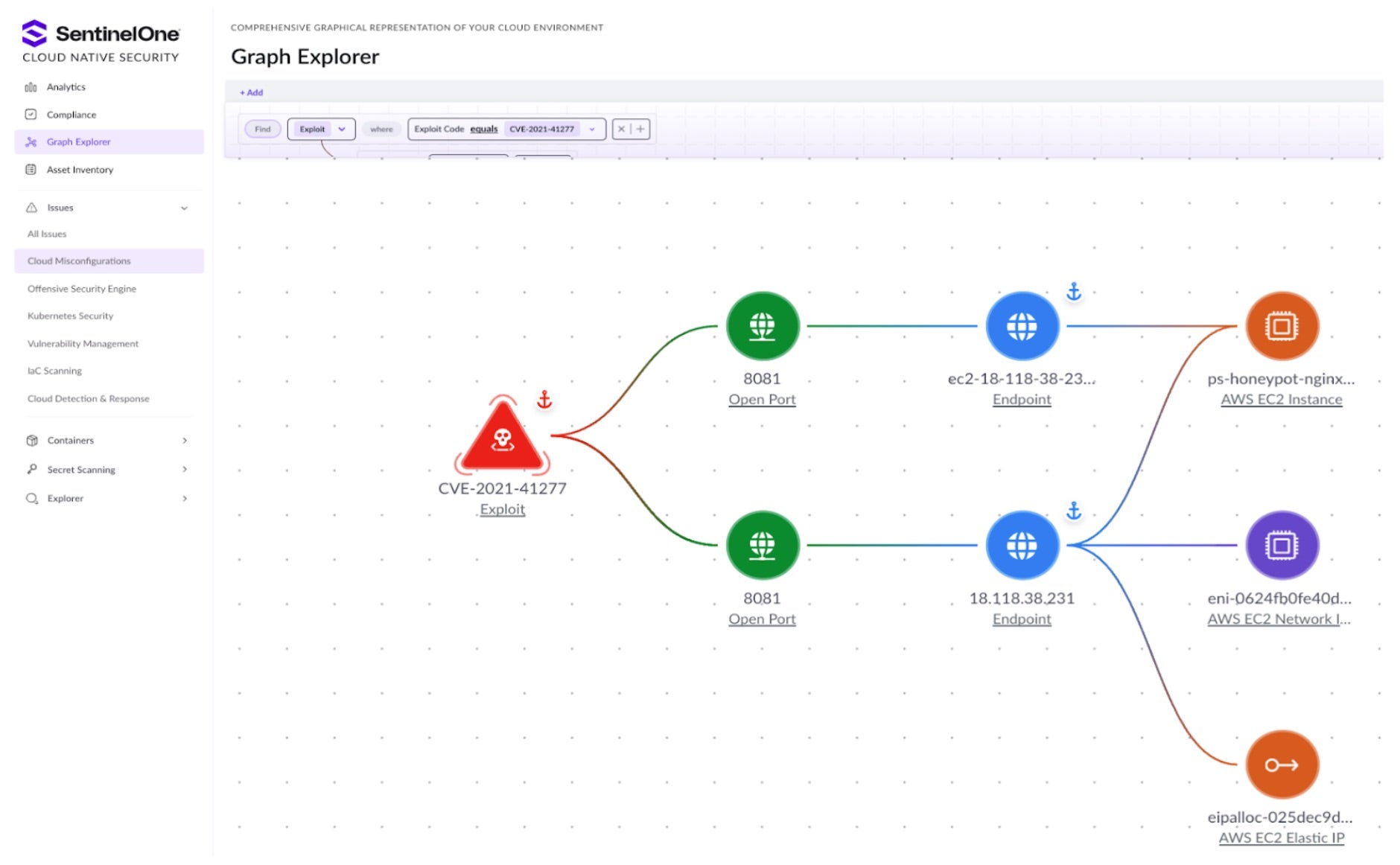
Cloud Security Posture Management (CSPM)
Ely: Let’s move on to misconfigurations. Cloud misconfigurations can often cause trouble for security and cloud teams. Let’s talk about our cloud security posture management (CSPM).
Anand: To help cloud and security analysts hunt for cloud misconfigurations, CNS has over 2,000 built-in checks, including the ability to easily add custom checks. These checks cover a broad range of cloud services and can be quickly searched by severity, cloud provider, or service type.
For each misconfiguration alert, CNS provides details on the nature of the resource and links to the affected resource within the native Cloud Service Provider console. Alerts include a quick description of the misconfiguration and provide an impact statement on why that particular misconfiguration is dangerous. CNS then lists recommended actions for engineers to remediate. Beyond the recommendations, one-click and automated remediation is available depending on the nature of the misconfiguration.
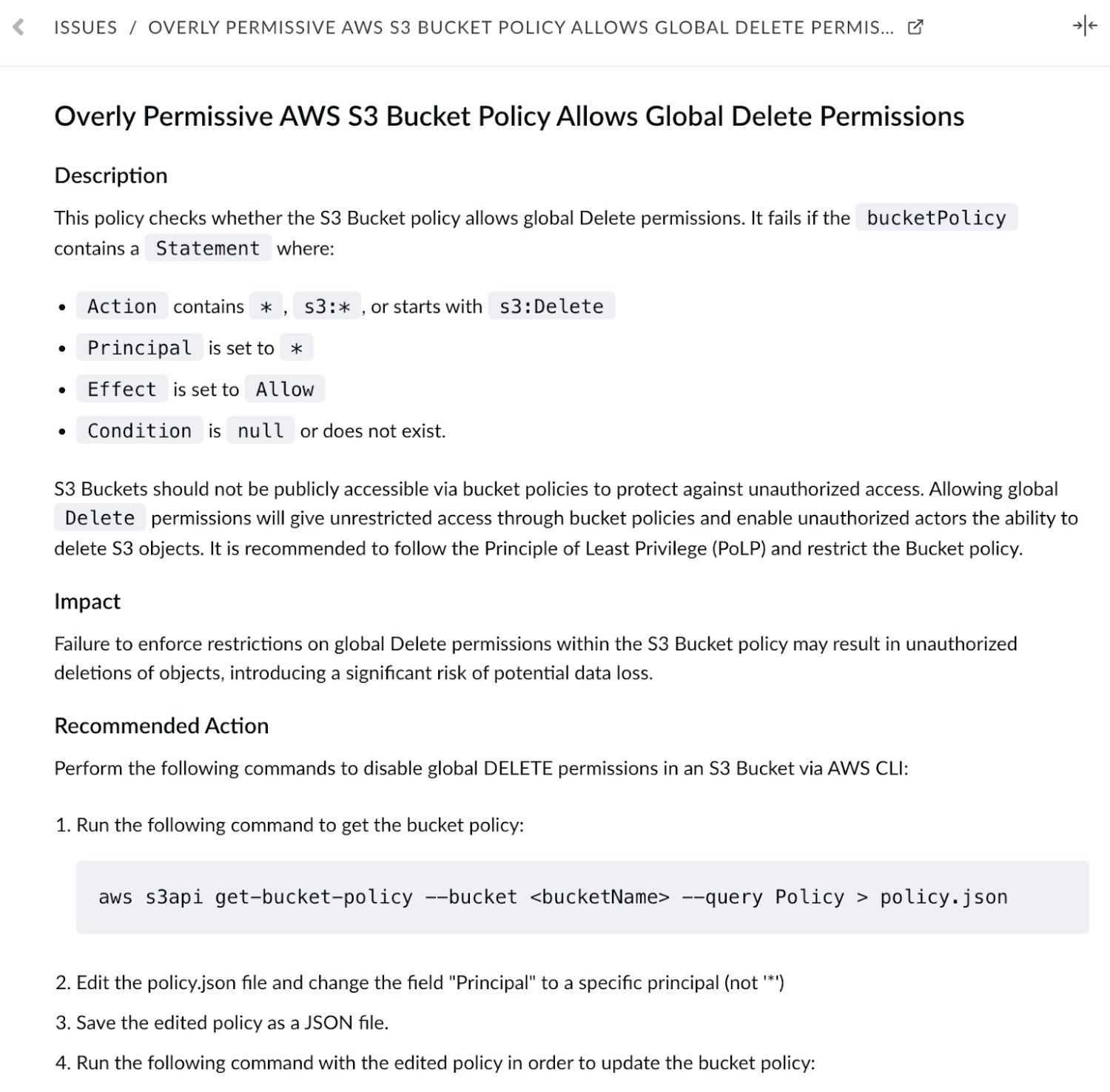
Currently for each misconfiguration, you can assign a particular analyst, apply labels so that analysts can document their progress, and provide an activity overview to allow users to audit actioning. As expected, CNS also integrates with ITSM providers like Jira to provide alerting workflows that your teams may prefer.
Ely: How are we helping customers from a compliance lens? Cloud posture and misconfigurations are often viewed within the context of compliance.
Anand: They are! While attackers don’t care about compliance, it’s a vital business requirement. To help security analysts easily meet their compliance requirements, CNS includes a dedicated dashboard for your chosen compliance standards. It covers NIST, SOC, ISO, CIS, and many more regulatory frameworks. CNS also includes real-time compliance score tracking over time that can help communicate a team’s progress within your organization.
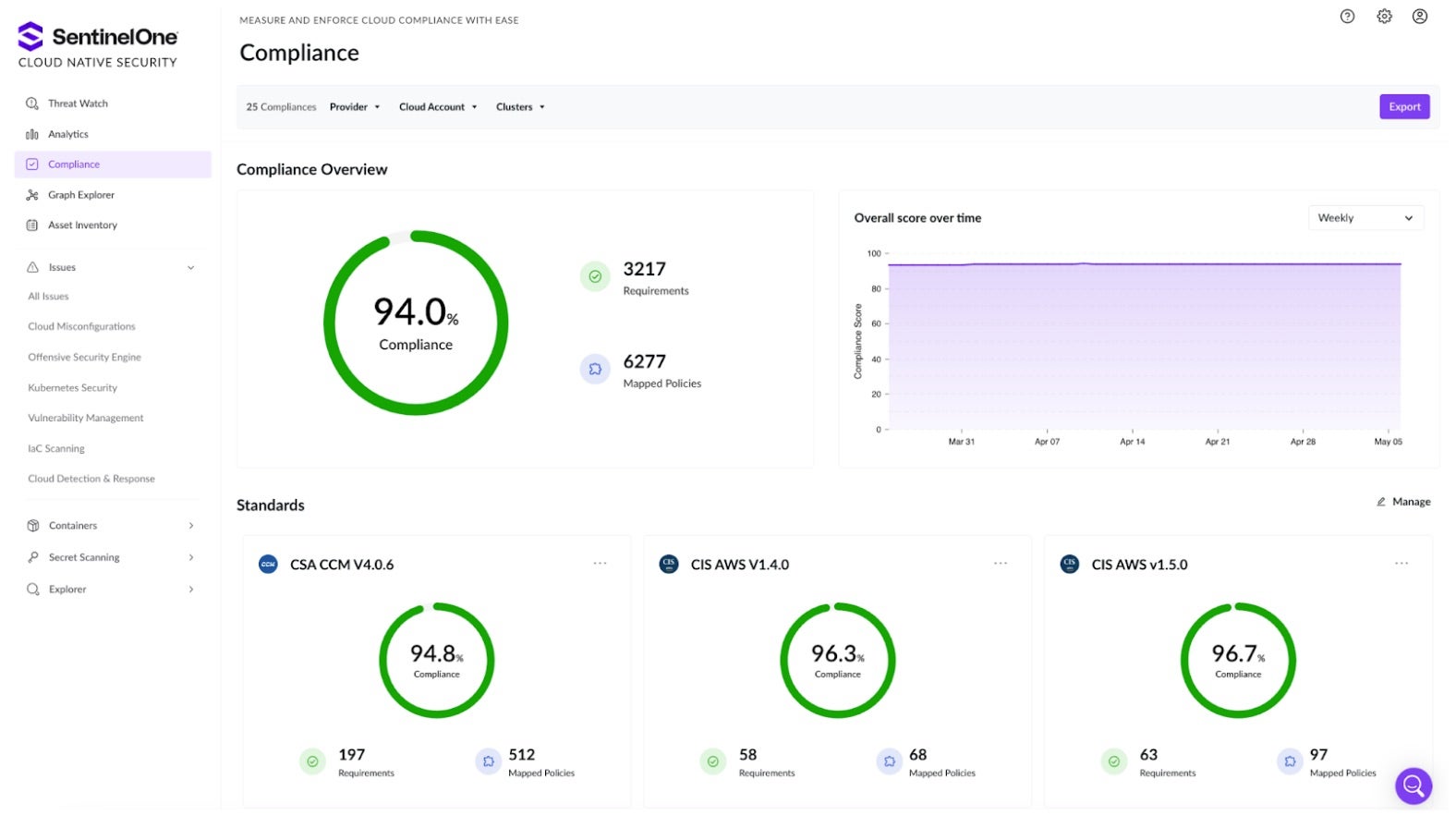
Agentless Vulnerability Scanning
Anand: In addition to contextualizing cloud assets and hunting for cloud misconfigurations, CNS has agentless vulnerability scanning across running virtual machines and containers. Vulnerability Management checks for vulnerabilities in OS packages, libraries, and running applications, to identify potential security risks. This scanning is continuous to provide an up-to-date view of your cloud health. CNS uses a rich repository of known vulnerabilities from 25+ databases, including CISA KEV, CVE, RedHat, NVD, MSRP, Kubernetes Security, OSVDB, and more. This ensures that organizations are safeguarded against new attack vectors, providing comprehensive protection for their entire cloud estate.
Additionally, our Vulnerability Management includes a software bill of materials (SBOM) detailing a resource’s inventory of components, libraries, and dependencies. Like how we handle misconfigurations, each vulnerability alert has a graphical view of the affected resources and can be assigned and tracked. Each vulnerability has details to contextualize the alert including the CVSS score, the EPSS score, and an overview of the Attack Vector, Attack Complexity, Privileges Required, User Interaction, Confidentiality Impact, Integrity Impact, Availability Impact, and Scope.
Ely: The real value is how CNS prioritizes alerts of vulnerabilities which are public internet-facing, and which vulnerabilities are connected to resources that are also misconfigured, which raises the risk profile of those assets. It’s tying together all the features we have discussed so far.
Now we have discussed cloud visibility and asset inventory, hunting misconfigurations with CSPM, and covered Vulnerability Management. These are all security features that assess running cloud environments. How are we helping customers as they build? For misconfigurations, how can we shift our security left?
Infrastructure as Code (IaC) Scanning
Anand: This is where I like to talk about the opportunity of Infrastructure as Code (IaC) Scanning. Many organizations leverage IaC to build repeatable architecture, Golden IaC templates are a great way to prevent resource misconfigurations. CNS identifies pre-production issues in IaC template files like Terraform and CloudFormation.
To enable this, CNS has multiple integrations with popular Version Control Systems to scan those templates and pinpoint misconfigurations before they reach production. Within the DevOps pipeline, we ensure consistent, repeatable, and appropriate configurations are codified according to best practices. This shift-left approach to security enables cloud and DevOps engineers to address issues and ensure best practices within the build phase.
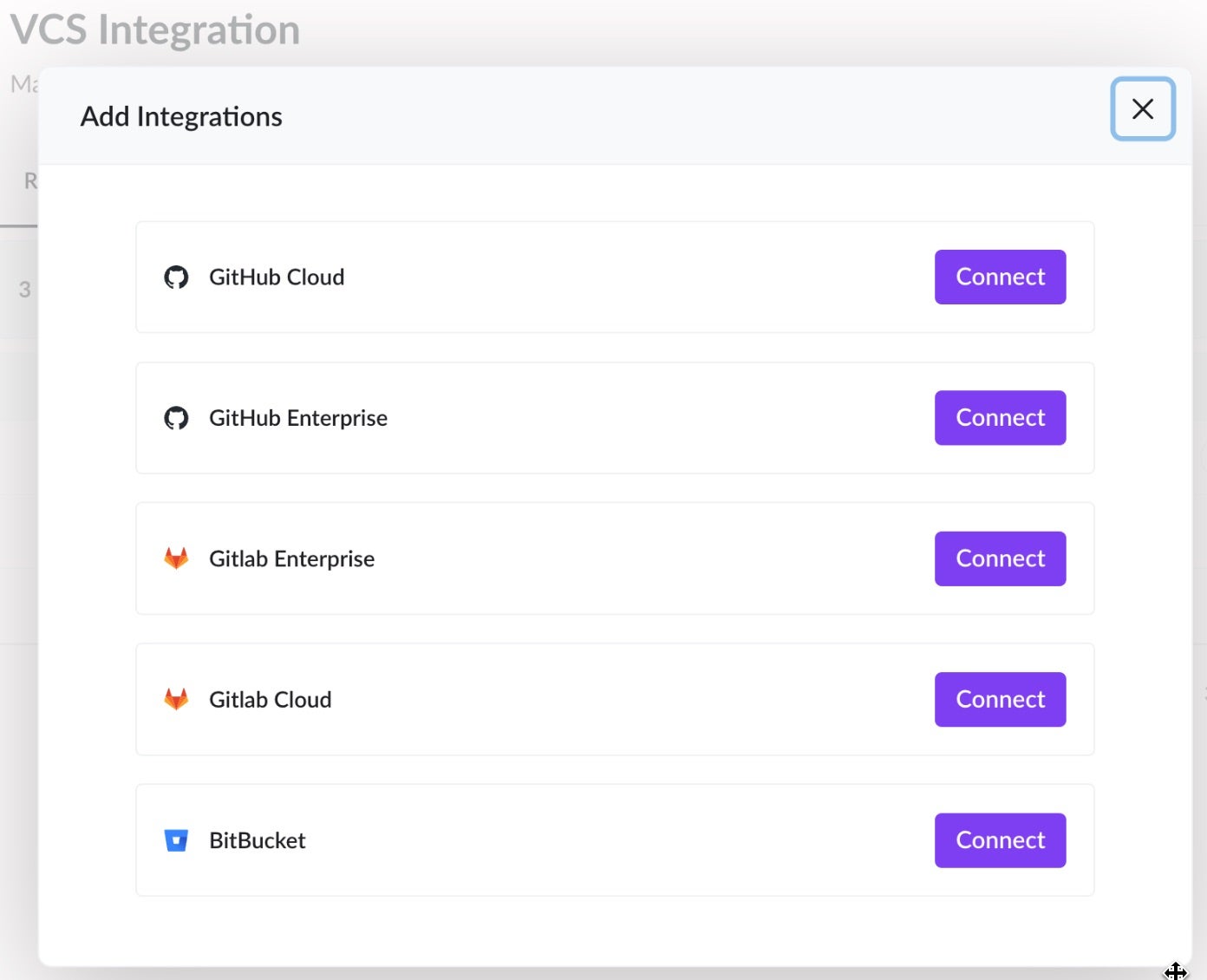
For issues that are not immediately worrisome and exploitable, I always recommend fixing them via the IaC approach, as it is always safer and less intrusive than making changes to live cloud environments.
Container & Kubernetes Security
Anand: For our clients needing container and Kubernetes security, CNS has simple and quick integration with popular CI/CD platforms to enable vulnerability scans of container images as they are built. By providing developers with feedback early in the development phase, security issues can be remediated before they make it to production.
Another way we can help cloud defenders shift their security left is by scanning container configuration files for Kubernetes (including Helm and manifests) to hunt for Kubernetes misconfigurations. Kubernetes is a widely-adopted container orchestration platform, notorious for overly permissive configurations that create unique security challenges for containerized workloads.
Kubernetes Security Posture Management (KSPM) goes well beyond CSPM which is ill-suited to the intricacies of Kubernetes network configurations and interpod communications. Our KSPM spans from the shift-left scan to real-time visibility of clusters and their activity. The KSPM capabilities within CNS deliver comprehensive visibility into workloads, nodes, pods, containers, and the Kubernetes API, enabling continuous monitoring and evaluation of your Kubernetes security stance.
CNS offers insights into your compliance posture, encompassing CIS Benchmarks for EKS, GKE, and AKS, the managed K8s services from the three leading cloud service providers, as well as the CIS Kubernetes Framework. For example, with CNS, customers pinpoint overly permissive roles, and detect namespaces lacking proper labeling to enforce Kubernetes-specific pod security standards.
Another example of CNS security checks across the build lifecycle is Secret Scanning.
Ely: This is so important – compromised credentials remain one of the primary causes of cloud security failures. It can be incredibly easy to leak API keys or accidentally hard code credentials during development, testing and staging, and the risk profile is massive given their power. From an attacker’s perspective, we often see automated repository scans for credentials, as they can appear in clear text. This is an easy point of entry for threat actors to login rather than hack in into a cloud account, or web application, or part of your cloud infrastructure.
Secret Scanning
Anand: That’s exactly right Ely, and this is something I used to build as well as a bug bounty hunter and ethical hacker. We are proud to announce Cloud Native Security leads the industry with over 750 distinct types of secrets and credentials that we scan for across code repositories and configuration files.
CNS periodically scans codebases within build environments and configuration files as well as public and private repositories of the organization, and public repositories of associated developers, to detect and alert on potential exposure of secrets and prevent credential leakage.
By automatically and meticulously scanning each commit, we ensure peace of mind that leakage is detected within seconds. Additionally, CNS flags for any newly created public repositories, ensuring that any fresh codebases are brought immediately to the attention of security teams for scanning and review.
For each Secret alert, alongside the typical impact, recommended action and alerting options, CNS provides a detailed overview of the sensitive data that has been exposed or is at risk. A concise list view with crucial insights including the specific type of the secret, location, with a linked source, and linked code snippet, file name, discovery time and the user who committed.
Crucially, CNS validates each secret alert, indicating if the exposed data is currently considered “valid” or not. This validation has its own timestamp and can be re-run with the click of the button, allowing analysts to validate risk in real time and monitor how remediation de-risks an environment. By clicking on “Revalidate”, the system will re-scan the secret and update its status accordingly. It’s especially useful when teams believe they’ve remediated a detected secret or when they suspect that the initial detection might have been a false positive.
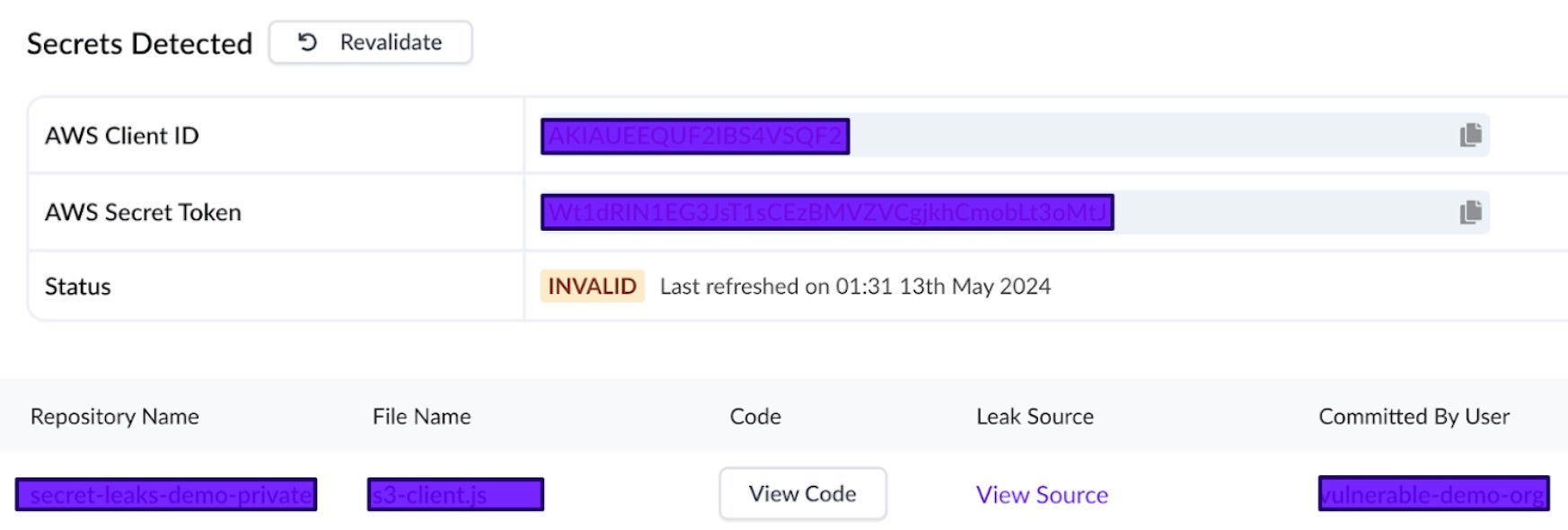
However, CNS also goes a step further. CNS is able to block and prevent credential leakage in real-time, with enforcement mechanisms to ensure secret-free merges.
Finally, CNS has a revolutionary Offensive Security Engine, the industry’s first autonomous red team approach to cloud security. This is the attacker’s mindset that we began our conversation with.
Offensive Security Engine
Anand: Across all of CNS’ findings, the Offensive Security Engine runs to differentiate between the theoretical and the exploitable. To begin, each reported issue includes a trace of the path through which the insecurity was detected. Via this path, CNS simulates attacker methods with de-fanged attacks. CNS then captures the response to validate the impact of an attack and provide evidence of exploitability. This Verified Exploit Path with evidence means that each Offensive Security Engine alert is proof-positive – there’s zero opportunity for false-negatives with these findings. This is prioritization at its finest.
with evidence means that each Offensive Security Engine alert is proof-positive – there’s zero opportunity for false-negatives with these findings. This is prioritization at its finest.
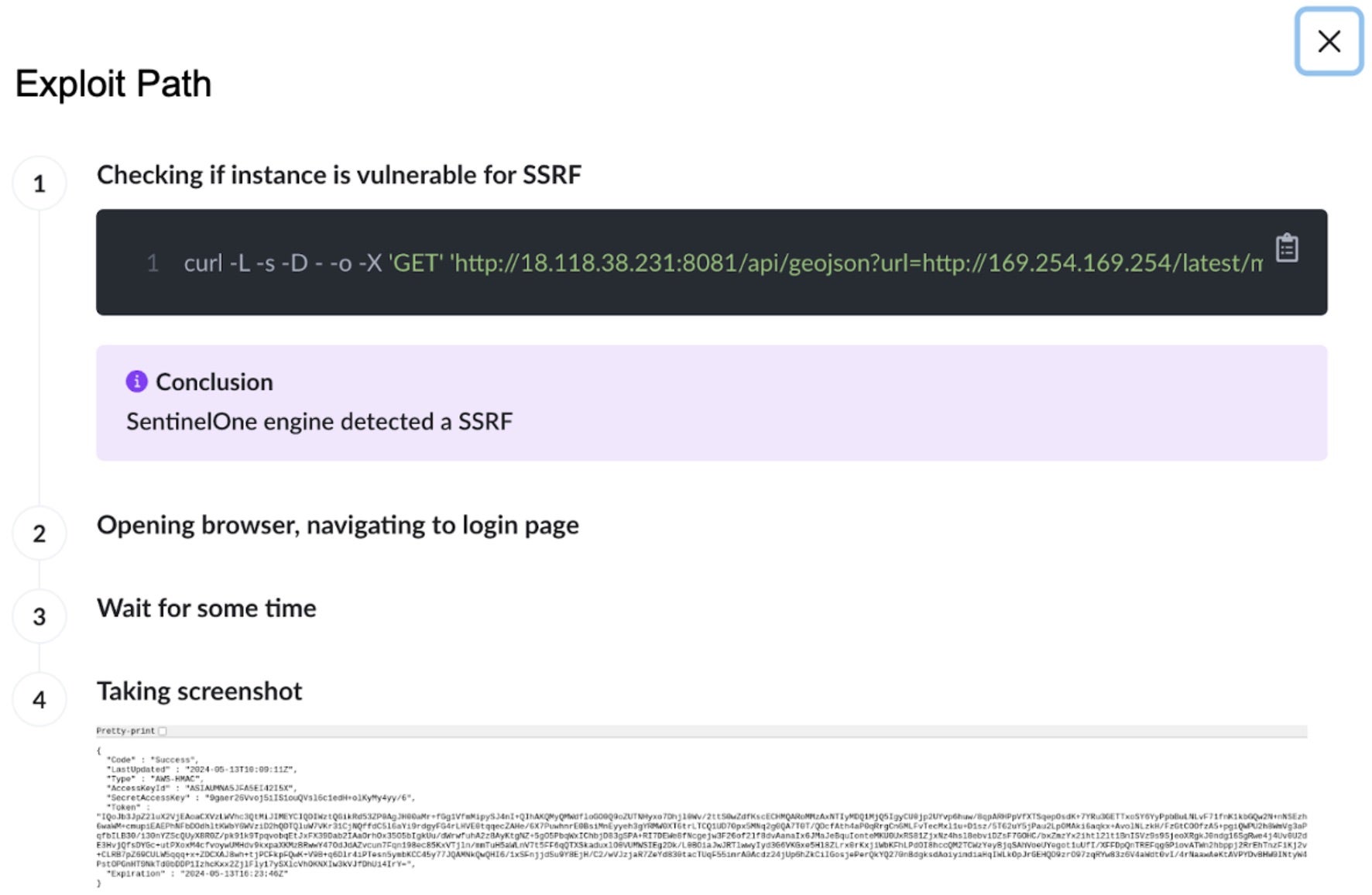
Ely: Again this is a revolutionary approach to cloud security. The Offensive Security Engine allows security teams to contextualize their cloud alerts, cut through the theoretical noise and focus on remediating the truly critical exploitable risks first to have maximum positive impact on the business’ cloud posture.
This is outcomes-focused, autonomous security for cloud defenders. With this launch, the agentless security capabilities are part of the greater whole of the Singularity Platform.
Cloud Security in The Singularity Platform
CNS has native integration to the Singularity Data Lake for investigation and custom detection purposes. The findings are in the universal Open Cybersecurity Schema Framework (OCSF) format. This means CNS alerting and findings can be correlated and combined with telemetry and findings from SentinelOne’s agent-based cloud security, our Cloud Workload Security, alongside our Endpoint Security telemetry and additional partner feeds.
Conclusion | Learn How Cloud Native Security Keeps Clouds Secure
Circling back to outcomes, Cloud Native Security (CNS) tackles the challenges customers face in adopting cloud platforms: sprawling asset footprints, too much noise from security alerting, not enough time, and preventable issues being detected too late.
CNS offers customers a breadth of coverage, supporting all major cloud providers, source code repositories, Kubernetes environments, and CI/CD pipelines. Installation is easy and fast, with near instant visibility in returning cloud assets inventory and assessing for issues.
Most importantly, Cloud Native Security provides evidence-based reporting of issues using a unique Offensive Security Engine. Beyond detecting issues, CNS validates which concerns are genuine with evidence of exploitation.
CNS is set to revolutionize cloud security for modern enterprises and provide security professionals with the tools they need to secure today, tomorrow, and beyond. Saving time and maximizing resources with evidence based Verified Exploit Paths ensures enterprises can focus on business-critical operations and build up a strong and lasting cloud cyber posture.
ensures enterprises can focus on business-critical operations and build up a strong and lasting cloud cyber posture.
Book a demo or contact us today to see how SentinelOne’s Cloud Native Security is set to radically improve enterprise cloud security posture.
 Cloud Security
Cloud Security Cloud Security, the comprehensive, AI-powered CNAPP from SentinelOne.
Cloud Security, the comprehensive, AI-powered CNAPP from SentinelOne.from SentinelOne https://ift.tt/Wqjp32s
via IFTTT
No comments:
Post a Comment