The Good | Russian-Based APT28 & LockBit Developer Condemned and Charged by International Enforcement
International law enforcement agencies took a hard stance against GRU-linked threat actors this week with the official condemnation of APT28 (aka Strontium, Fancy Bear, Forest Blizzard) and identification and sanctioning of LockBit ransomware’s administrator and developer.
NATO and the EU, joined by the U.S. and U.K., formally condemned the Russian threat group known as APT 28 for a long-term cyber espionage campaign against various European countries. In particular, Germany and the Czech Republic highlighted an email-based attack last year on various government agencies as well as organizations across the military, air and space, and IT sectors in NATO member countries, NATO fast reaction corps, and Ukraine. APT 28 has also been known to target critical infrastructures in various other EU member states.
The 2023 attack leveraged CVE-2023-23397, a zero-day vulnerability in Microsoft Outlook, to steal credentials, perform lateral movement in victim networks, and exfiltrate sensitive emails from specific accounts. NATO called on the Russian state to “respect their international obligations and commitments to uphold international law and act within the framework for responsible state behavior in cyberspace.”
From the DoJ, the identity of the developer and administrator behind the notorious LockBit ransomware group has finally been unveiled. Russian national Dmitry Yuryevich Khoroshev (aka LockBitSupp and putinkrab) is also being sanctioned by various international enforcement agencies with the U.S. Department of State offering a reward up to $10 million for information leading to his arrest or conviction.
Khoroshev’s sanctioning follows the joint operation earlier this year disrupting LockBit ransomware infrastructure and operations. Before the seizure of its public-facing websites and servers, Khoroshev and his affiliates were instrumental in LockBit’s rise to one of the world’s most prolific ransomware variants and operations, worth billions of dollars in damages and loss.

The Bad | Novel Cuckoo Infostealer Exhibits Spyware Capabilities on macOS Devices
An emerging malware dubbed “Cuckoo” is targeting Apple macOS devices, designed with a dual-purpose of stealing information and acting as spyware. Cuckoo is a universal Mach-O binary capable of running on both Intel and Arm-based Macs. Observed distribution vectors show that the binary is hosted across a smattering of websites that claim to convert music from paid streaming devices to MP3 files for download.
Cuckoo is adept at exploiting osascript to prompt users for their system password and running commands to gather sensitive data like hardware information, currently running processes, and installed apps. It can also take screenshots and harvest from iCloud Keychain (Apple’s password management system), Apple Notes, web browsers, crypto wallets, and popular apps like Steam, Telegram, and Discord.
Infostealers targeting macOS usually do not work towards establishing persistence, but such behavior is crucial to spyware. Cuckoo sets persistence through a LaunchAgent that runs when the user logs in and every 60 seconds during login.
New analysis from SentinelLabs reports a rise in Cuckoo samples and trojanized apps, with new ones appearing daily since the original Cuckoo stealer was first reported late last month. These trojanized apps advertise dubious services and are able to trick users past warnings from Apple Gatekeeper. SentinelLabs also confirms that at the time of writing, the latest version of XProtect (version 2194) is unable to block execution of Cuckoo malware. SentinelOne customers are protected from macOS Cuckoo Stealer.
As a best practice, users should always proceed with caution when downloading apps from unknown, third-party developers. With the rise in malware targeting macOS devices over the last few years, it is essential now to ensure that Macs are fully protected with an advanced security solution just like other operating systems.
The Ugly | Two New F5 Flaws Leave BIG-IP Next Central Manager Open to Remote Exploits & Device Takeover
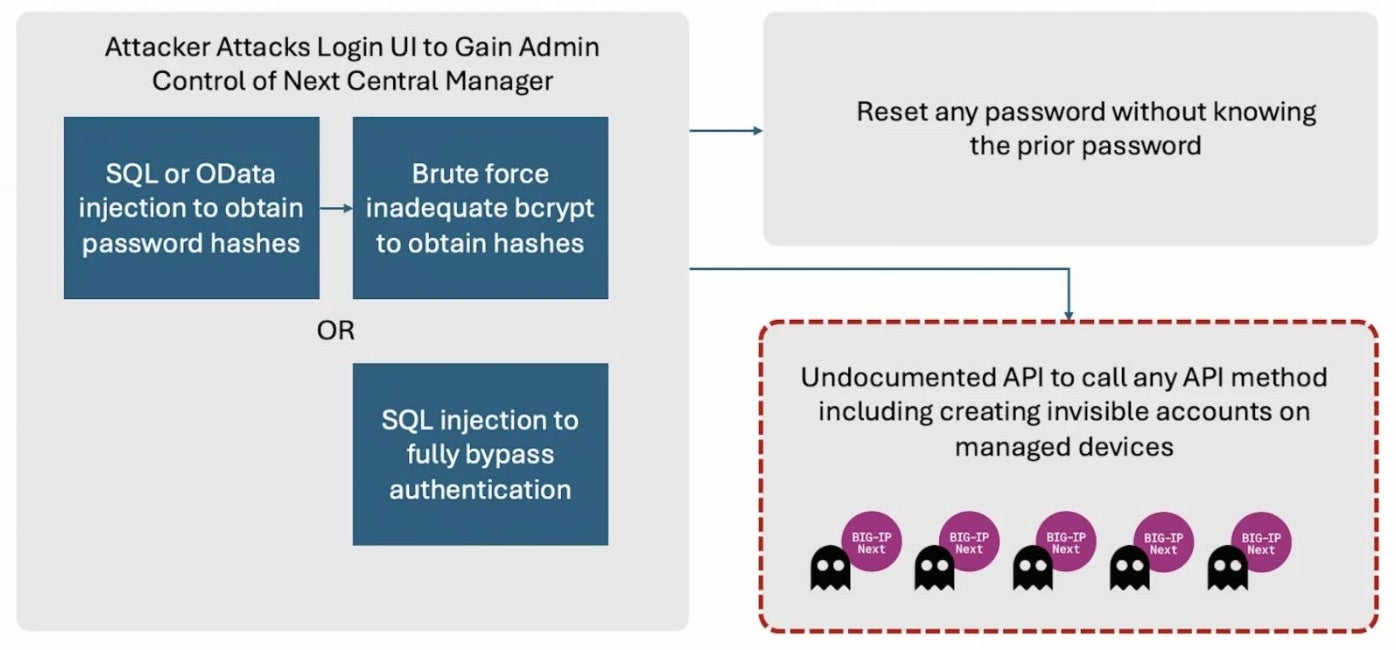
Multi-cloud and application security vendor, F5, has released fixes for two high-severity vulnerabilities found in BIG-IP Next Central Manager, the main component in controlling BIG-IP Next load balancers and app instances in both on-prem and cloud environments. Both CVE-2024-26026 (an SQL injection flaw) and CVE-2024-21793 (an OData injection flaw) could allow execution of malicious SQL commands on unpatched devices through the BIG-IP Next Central Manager API.
In an SQL injection attack, attackers inject the malicious queries into input fields or parameters to manipulate the database to execute unauthorized commands. This can lead to unauthorized access, data leakage, and even complete control over the database. These attacks are often leveraged to extract sensitive information or tamper with data within the database, posing significant risks to the security and integrity of the targeted web applications.
Security researchers have noted how the vulnerabilities would first be exploited to obtain full administrative control of the Next Central Manager before creating rogue administrative accounts hidden from the Manager user interface (UI). These “invisible” accounts would then allow attackers to establish persistence in the environment, even if the legitimate admin account password was reset in the UI and the system patched. F5 has recommended its users to patch immediately, or to restrict Next Central Manager access to trusted users only over a secure network until the updates can be installed.
In the past two years, several critical-level F5 flaws have made headlines. One flaw from October 2023 in the BIG-IP configuration utility allowed remote code execution and another from May 2022 targeted networks across government agencies and private sector organizations, prompting CISA to issue a warning to all Federal Civilian Executive Branch Agencies (FCEB) affected.
from SentinelOne https://ift.tt/m4ctlO0
via IFTTT
No comments:
Post a Comment