The Good | Two Major Botnets Taken Down by Collaborative DoJ and Europol Operations
The botnet industry took a serious hit this week as law enforcement in the U.S. and in Europe executed two major operations to dismantle 911 S5 – likely one of the world’s largest botnets, and an extensive ecosystem of malware droppers including IcedID, SystemBC, Pikabot, Smokeloader, Bumblebee and Trickbot, respectively.
DoJ-led Operation Tunnel Rat successfully disrupted and seized the notorious 911 S5 residential proxy botnet and arrested its administrator, Chinese national YunHe Wang (35). Wang’s current charges stem from his deployment of malware and the creation and operation of the botnet service. According to the indictment, Wang and his co-conspirators amassed a network of over 19 million residential Windows devices globally, including 613,841 IP addresses located in the United States alone.

911 S5 revenue was generated by offering cybercriminals access to infected IP addresses for a fee. Over its years of operation, the 911 S5 botnet facilitated numerous large-scale cyberattacks, financial and identity schemes, child exploitation, bomb threats, and more. Wang faces 65 years in prison if convicted on all counts.
Europol’s Operation Endgame saw similar success by targeting over 100 servers worldwide that feed several major malware droppers. Malware droppers serve to introduce harmful payloads into a victim’s system, acting like an initial access point and delivery vehicle for ransomware, spyware, keyloggers, trojans and more. After seizing an infrastructure hosting over 2000 domains, the agency arrested four individuals and identified eight fugitives linked to associated malware operations. According to reports, one of the main suspects involved made $74.5 million USD by renting out their infrastructure for ransomware deployment. Operation Endgame is being lauded as the largest operation against botnets and a marked step forward in disrupting the ransomware landscape.

The Bad | Proof-of-Concept Exploit Released for Critical RCE Flaw in Fortinet’s SIEM Appliances
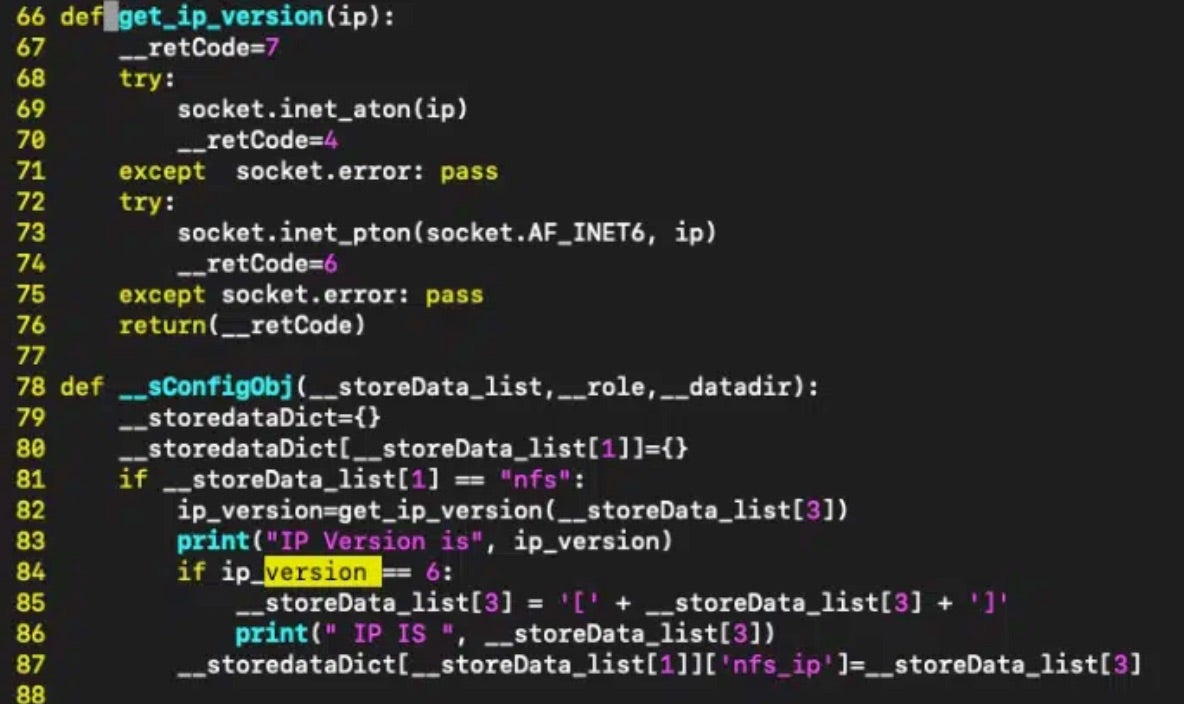
An exploit has been released for a maximum severity remote code execution (RCE) flaw in Fortinet’s security information and event management (SIEM) solution. Described as an improper neutralization of elements in an os command injection within FortiClient FortiSIEM (versions 6.4.0 and higher), CVE-2024-23108 allows attackers to execute unauthorized code or commands via crafted API requests.
Security researchers providing a technical analysis of the issue noted that the CVE-2024-2318 was patched in February along with another critical severity RCE bug tracked as CVE-2024-23109. Initially, Fortinet claimed these two flaws were duplicates of a similar flaw (CVE-2023-34992) patched in October, however, they later confirmed that the CVEs were variants of the original vulnerability.
Now, the newly released proof-of-concept (PoC) shows that while the first patches attempted to neutralize user-controlled inputs by adding a wrapShellToken() utility, there is actually a second order command injection remaining when certain parameters are passed to datastore.py.
Ransomware outfits commonly target Fortinet vulnerabilities to obtain initial access to corporate and government organizations. Such flaws are also often seen in cyber espionage attacks, where the threat actors can establish a beachhead to target several high-value victims quickly. Placing an emphasis on regular patch management and system log monitoring in conjunction with robust monitoring and detection technology that covers all attack surfaces minimizes the risk of data loss and business disruptions.
The Ugly | PyPi Info-Stealer Promoted On Stack Overflow By Threat Actors Posing As Helpful Contributors
The online developer community Stack Overflow is reportedly being exploited by threat actors to distribute malware. Blending into the Q&A structure of the platform, actors have been observed answering questions and promoting a malicious PyPi package named ‘pytoileur’. Security researchers reporting the discovery describe how the package installs information-stealing malware on Windows systems to perform surveillance, establish persistence, and steal cryptocurrency.
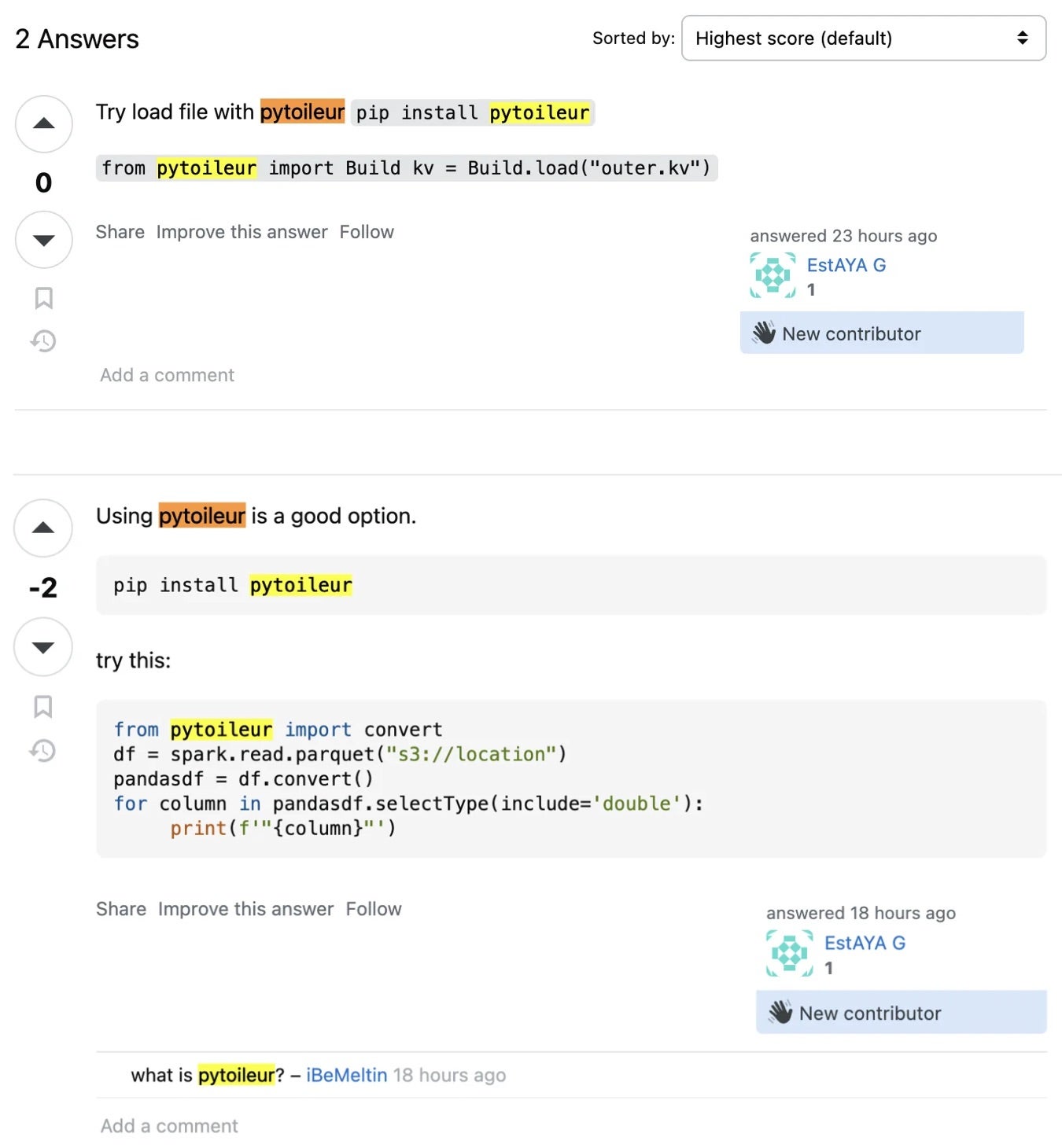
Pytoileur was uploaded to the PyPi repository as an API management tool. The package’s metadata includes a ‘Cool package’ string, linking pytoileur to an ongoing campaign from 2023. While such packages are usually spread through typosquatting, actors leveraged Stack Overflow’s popularity and reach amongst global developers, posing as users answering open issues before promoting pytoileur as the solution.
The malicious package contains a ‘setup.py’ file with a base64 encoded command that is padded with spaces, making it difficult to detect unless users have word wrap enabled in the text editor. Once decoded, the command downloads and executes a file called runtime.exe – a Python program steals passwords, cookies, credit cards, browser history, and other sensitive data from the user’s system. Harvested data is then sent back to the threat actor to be used for future compromise of affected account owners, or sold on dark markets.
Before the malicious account was suspended from Stack Overflow, it was downloaded 369 times as of this writing. Though malicious PyPi packages are a recurring problem, threat actors masquerading as helpful users on question-and-answer forums is a novel technique. It underscores the evolving strategies of cybercriminals, who continue to leverage widely-trusted open-source platforms that support developers of all experience-levels as a way to propagate malware.
from SentinelOne https://ift.tt/Y1FpkgB
via IFTTT
No comments:
Post a Comment