The Good | Extortionist Sentenced to 10 Years For Cybercrimes Against U.S. Medical Clinics
This week, the FBI sentenced Robert Purbeck to 10 years in prison for stealing personal data from over 132,000 individuals across 19 U.S. organizations. Purbeck is also known as “Lifelock” and “Studmaster” online and has been carrying out cybercrimes and extortion attempts since 2017.
Robert Purbeck, who hacked into the computer servers of the City of Newnan, a Griffin, Georgia, medical clinic, and 17 other victims across the United States has been sentenced to federal prison. https://t.co/2YI90s9mCk pic.twitter.com/mEzUT6Z0ie
— US Attorney NDGA (@NDGAnews) November 13, 2024
Hospitals and clinics hold mass amounts of personally identifiable information (PII), payment data, and other sensitive patient details easily sold on dark markets. Purbeck bought network access to a medical clinic’s server, using the stolen credentials to pilfer the personal information of 43,000 patients including names, addresses, birth dates, and social security numbers. The following year, Purbeck again purchased illegal server access, this time to a police department, to get 14,000 individuals’ worth of PII as well as various police reports and files.
In July 2018, he targeted an orthodontist, demanding a ransom in Bitcoin payment under the threat of selling patient data. Court documents noted that Purbeck went as far as threatening to sell the PII of the orthodontist’s underaged child and harassing his patients over email and text messages. Purbeck is now ordered to serve three years of supervised release and pay over $1 million in restitution to his victims in addition to his 10-year sentence.
Data theft and ransomware attacks in healthcare can lead directly to patient endangerment, causing delays in procedures and tests, increased complications in care, and longer stays in hospital. As healthcare entities move towards digitalizing their records and systems, robust security focusing on threat detection, real-time monitoring, and identity security can protect sensitive data from being compromised.
The Bad | Chinese APT Volt Typhoon Revives Botnet to Attack Outdated SOHO Routers
Nearly a year after an FBI-led takedown of its botnet, China-aligned Volt Typhoon is rebuilding its KV-Botnet malware network. Known for maintaining persistent access to critical U.S. infrastructure, Volt Typhoon’s botnet initially failed to revive in February but was then seen in August exploiting a zero-day vulnerability. Now, the hacking outfit’s primary strategy is compromising outdated SOHO (small office/home office) routers using MIPS-based malware and webshells, which communicate over non-standard ports to evade detection.
The KV-Botnet, dubbed ‘JDYFJ Botnet’ by researchers for the self-signed SSL certificate found in infected devices, currently targets Cisco RV320/325, Netgear ProSafe firewalls, DrayTek Vigor routers, and Axis IP cameras. Since September, Volt Typhoon has infected 30% of internet-exposed Cisco RV320/325 devices, though the specific vulnerabilities being exploited are still unknown. As of this writing, the group’s latest efforts have been to route malicious traffic covertly using compromised, legitimate infrastructure as a proxy. Command servicers are currently hosted across platforms like Digital Ocean, Vultr, and Quadranet to ensure resilience.
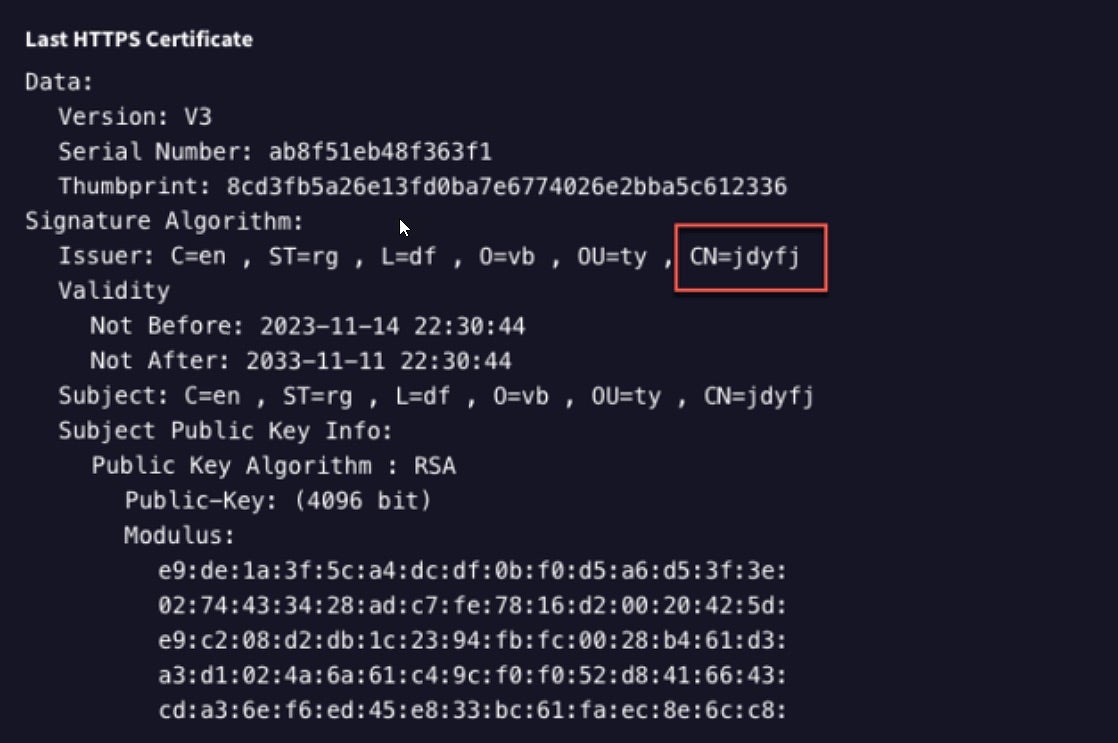
The threat group uses a compromised VPN device in the Pacific southwest to route traffic between Asia and the Americas – a deliberate geographical choice that speaks to Volt Typhoon’s base of operations. All of the recent activity from Volt Typhoon signals their return to operations worldwide, building back up the scale of their botnet to what it was prior to its seizure earlier in the year.
Admins managing SOHO businesses can replace outdated and unsupported routers, place new routers behind firewalls, restrict admin panel access, and stay up to date with firmware updates to mitigate risks associated with Volt Typhoon’s return.
The Ugly | Iranian APT Targets Aerospace Industry Using Fake ‘Dream Job’ Lures
Threat actors continue to capitalize on global labor gaps, banking on making contact with unsuspecting applicants to deliver malware or steal information. Similar to DPRK ‘Dream Job’ campaigns that have surfaced in recent years, an Iranian-based threat actor known as TA455 has been targeting the aerospace sector with fake job offers since September 2023. TA455 is a sub-cluster of APT35 (aka TunnelVision) and affiliated with Iran’s Islamic Revolutionary Guard Corps (IRGC).
In February, the threat group launched a series of highly-targeted campaigns on the aerospace and defense industries across the Middle East. Historically, TA455 has also been observed employing front companies to engage with victims professionally, usually through spoofed Contact Us pages and impersonation via AI-generated photos.
The latest report on this campaign notes the similarities between TA455 tactics and those of Lazarus Group, such as job lures and DLL side-loading. This hints at the possibility of tool-sharing or outright mimicry to avoid attribution. TA455 operations are also observed using fake recruiting sites (careers2find[.]com) and LinkedIn profiles to distribute malware-laden ZIP files that contain an executable (SignedConnection.exe) and malicious DLL file (secur32.dll). The DLL file is a trojan loader dubbed ‘SnailResin’ designed to execute the SlugResin backdoor to enable credential theft, privilege escalation, and lateral movement.
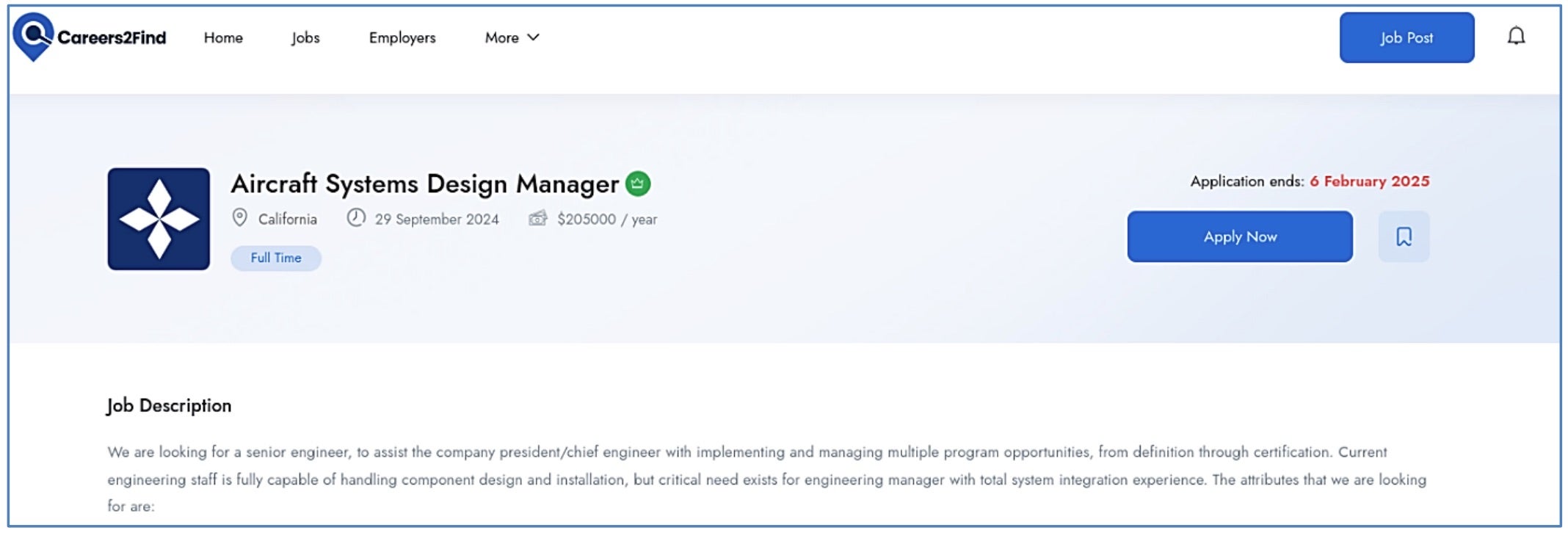
TA455’s multi-stage, social engineering attacks highlight the continued use of job-themed lures, which exploit individuals’ career ambitions through platforms like LinkedIn and personal email to bypass corporate security defenses. These tactics are especially effective as job hunting is often kept private from employers, increasing risk. As similar tactics continue to be used by many APT groups globally, organizations can focus on educating their employees about the dangers of unsolicited job offers and social media interactions, as attackers can easily impersonate legitimate contacts.
from SentinelOne https://ift.tt/5R3kYQn
via IFTTT
No comments:
Post a Comment