Mature security processes should involve leveraging playbooks to guide their responses to potential breaches and ensure compliance with regulations. These playbooks serve as dynamic blueprints, outlining predefined steps, protocols, and best practices tailored to specific scenarios. Harnessing the power of playbooks in cybersecurity not only streamlines incident response but also empowers organizations to preemptively mitigate risks, fortify defenses, and maintain regulatory adherence.
How LogRhythm Case Playbooks Help with Compliance
LogRhythm Case Playbooks make it easier and more repeatable for analysts to respond to incidents and security events within a security information and event management (SIEM) platform. Through the rich feature set of Case Playbooks, analysts can not only create their own playbooks, but modify existing playbooks, as well as attach company policies and procedures to the playbook. All these features let the analyst react faster and more efficiently.
Because Playbooks are a documented set of procedures, they also lend themselves well to performing activities related to compliance requirements. Maintaining proper compliance can be challenging, but implementing more compliance-focused playbooks or taking your existing security-focused use case playbooks and reviewing them for compliance considerations will benefit your company. This will be beneficial for new and inexperienced analysts with less experience with compliance.
Cybersecurity Playbook Examples
In this blog, the LogRhythm Labs compliance research team highlights two examples where Playbooks can help strengthen your compliance maturity and reduce gaps in your compliance. For LogRhythm customers, both Playbooks can be found in LogRhythm Community.
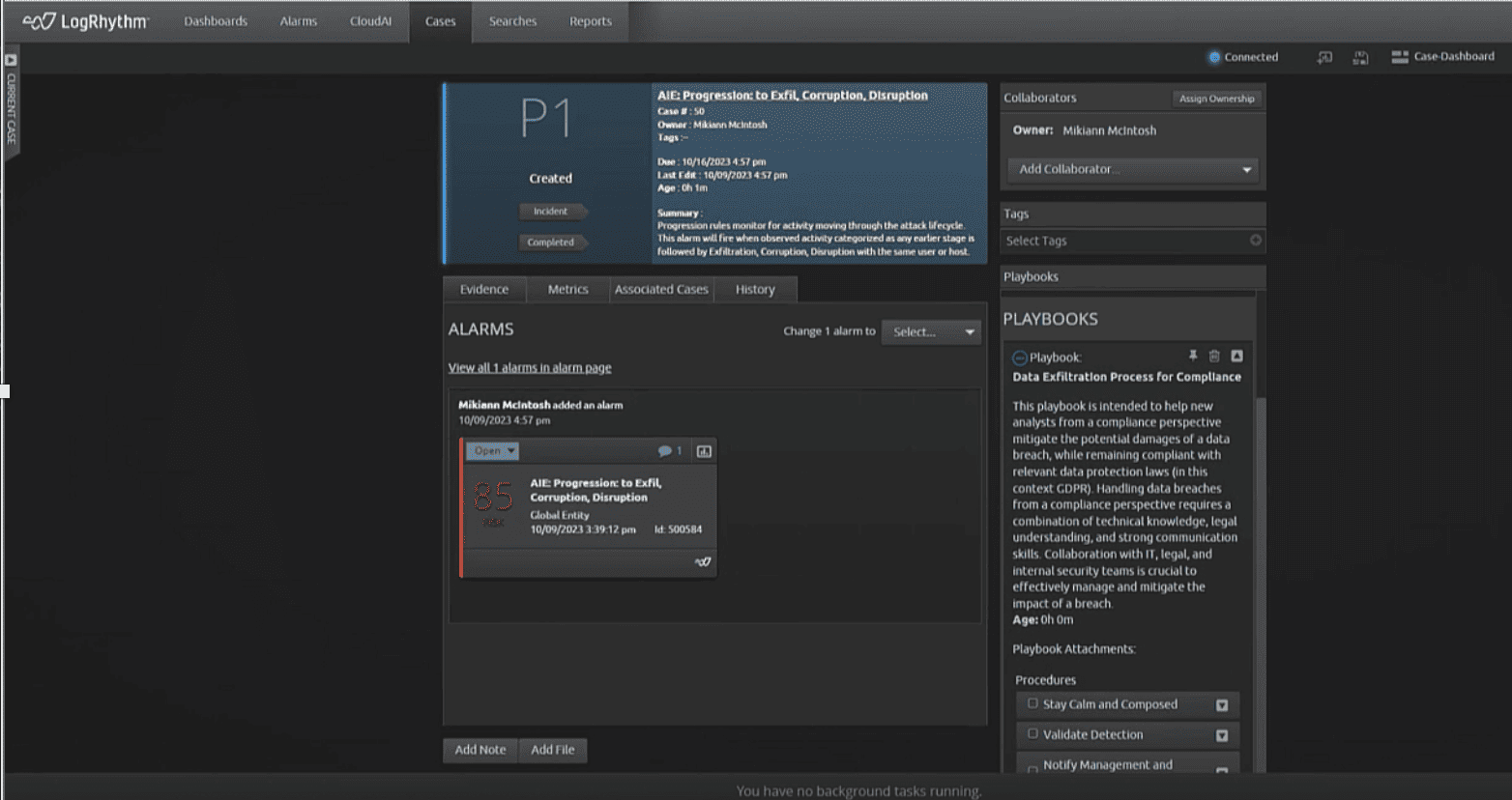
Playbook #1: Data Exfiltration
In this first example, you can observe appropriate actions to consider when tackling potential data exfiltration from a compliance perspective. The goal of this playbook is to provide a template guidance for new analysts when mitigating a detected data breach while remaining compliant with relevant data protection laws/frameworks (in this case GDPR). Data breaches are one of the most common security risks an organization can experience, so it’s pivotal to establish an action plan that alleviates the pressure of singularity and encourages efficient collaboration.
In the context of compliance and technical analysis, here are preliminary and closing steps to consider when building out a reaction plan towards data breaches:
- Stay Calm and Composed
- Maintain a calm demeanor and focus on the task at hand. Security breaches can be stressful, but a composed response is crucial.
- Incident or Event
- Determine if you are investigating an incident or event.
- Identify the Affected Host
- Identify the host involved with the signaled data exfiltration alarm.
- Validate Detection
- Collaborate with the security operations center (SOC) department to confirm the validity of the alert, whether it is a False Positive or a True Positive. Then check if the alarm context aligns with your organization’s policies and expectations regarding data exfiltration.
- Notify Management and Incident Response Team
- If the detection is confirmed to be a True Positive immediately inform your supervisor or the designated incident response team within your organization about the breach. Time is critical so swift action is required.
- Document the Incident
- Start documenting all relevant details about the breach within a breach report, including the date and time it was discovered, the method of breach, affected systems, and the potential impact. Ensure all information is accurate and well organized.
- Activate the Incident Response Plan
- Refer to your organization’s incident response plan and follow the predefined steps for addressing security incidents. This plan should outline roles and responsibilities during a breach.
- Data Breach Notification
- Determine whether it constitutes a data breach as defined by GDPR and other relevant laws. If the breach meets the criteria for notification, work with legal and compliance teams to prepare and submit notifications to regulatory authorities and affected individuals within the required timeframe.
- Communication
- Coordinate internal and external communication efforts. Ensure that affected parties are informed in a timely and appropriate manner. Maintain a record (for example emails, instant messages, etc.) of all communication related to the breach.
- Legal and Regulatory Compliance
- Assist in the collaboration with legal counsel to ensure that all actions taken are compliant with GDPR and other data protection laws/regulations.
- Continuous Improvement
- Continuously assess and improve data security and compliance measures based on lessons learned from the breach and changes in regulations.
Handling data breaches from a compliance perspective requires a combination of technical knowledge, legal understanding, and strong communication skills. Collaboration with IT, legal, and internal security teams is crucial to effectively manage and mitigate the impact of a breach. Please ensure to employ this document as a template and refer to your organization’s policies/best practices when creating your playbook.
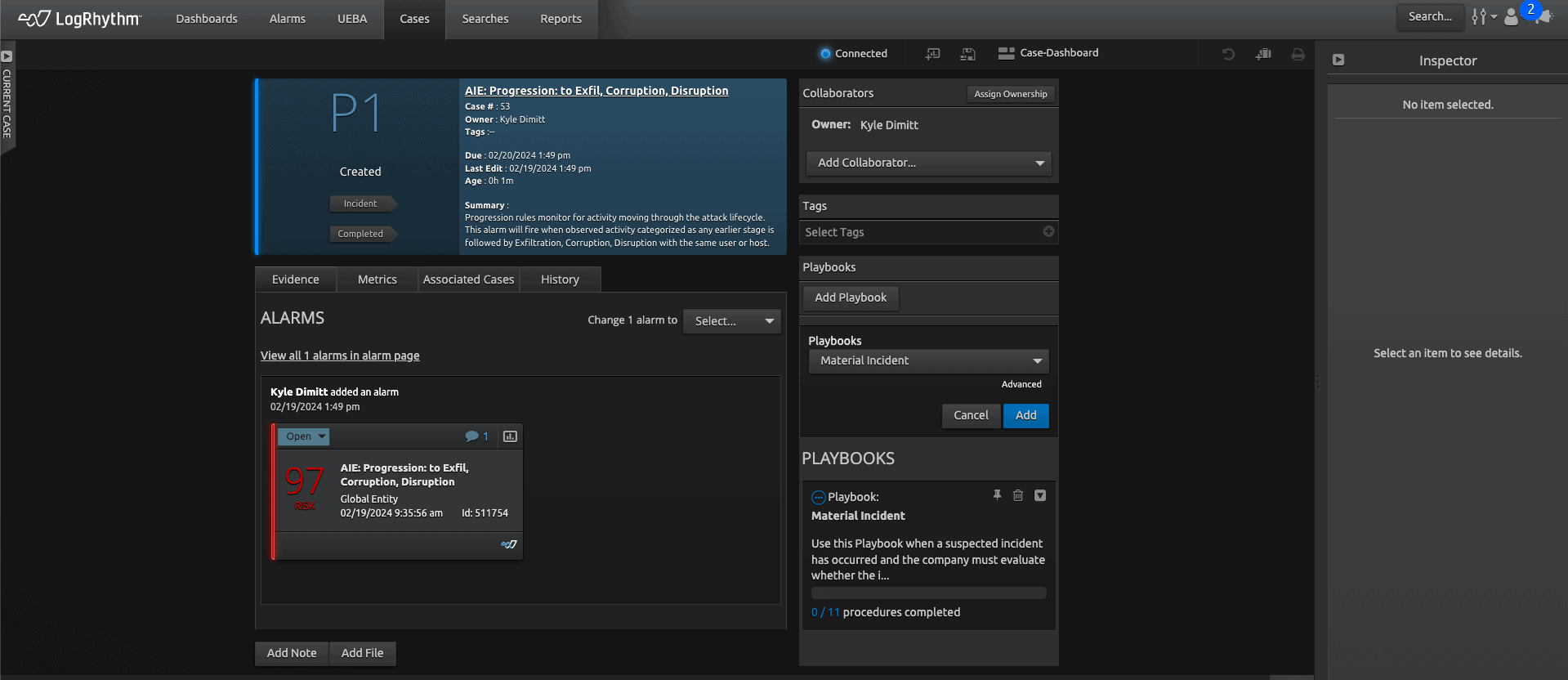
Playbook #2: “Material” Incidents
This second example is related to the SEC’s new rules for public companies around the disclosure of “material” cyber incidents. This has been a popular and often contentious topic amongst industry professionals as the requirements of the new rule have parameters that are open to interpretation, specifically around what constitutes a material incident and the timeline for disclosure.
Materiality, as described by the SEC in the final rule, means that “there is a substantial likelihood that a reasonable shareholder would consider it important.” Once an incident is determined to be material, an organization has four days to disclose. By this definition, materiality is not necessarily a simple financial threshold or set of events that must occur, but a culmination of data points that in aggregate could be material to a reasonable investor. Given the nature of this independent evaluation of materiality, each organization is likely to have a decision maker, or set of decision makers, that evaluates the circumstances to determine the materiality.
Because of this, our playbook template does not provide a step-by-step guide to determining if a given incident is material. This playbook is intended to help security analysts track the path of an incident across internal and external systems, capture related evidence, and communicate that information to appropriate stakeholders for ultimate evaluation of materiality. By following the guidance in this template, the appropriate stakeholders should be informed in a timely manner and have enough evidence to assess materiality and the need to make public disclosures.
- Determine if you are investigating an incident or event
- This step could take further investigation to complete depending on your organization’s definition of event and incident, but is a key delineation that should be made
- Acquire, preserve, secure, and document evidence
- By creating the case it is likely that some evidence related to the incident is already attached, but it is critical to gather all related data into the case for evaluation by yourself and others reviewing.
- Identify the hosts impacted involved with the incident and obtain a forensic image of the system
- The importance of preserving evidence is critical. Additionally, this is a perfect opportunity to make note of whether the systems are in scope for any compliance efforts and make initial contact with those system owners.
- Identify the services impacted
- Document the nature of the impact on any impacted services and the timing related to that impact. This information will help decision-makers evaluate the scope and size of the incident.
- Identify the method of attack
- This step may not be readily apparent but will be important for decision makers to understand and potentially include when disclosing.
- Identify the source of attack
- If possible, identify and document the source of the attack. Use OSINT resources as necessary to source the activity and link it to potential threat actors. Like the step prior, this step may take time, but will also be important for decision makers in evaluating the overall significance of the incident and ongoing risk.
- Disable any affected user accounts
- Any user accounts utilized during the attack, either compromised or newly created, should be tracked and recorded within case. This will be important in both stopping the potential spread of the incident and again tracking the overall scope of what occurred.
- Identify data classification of the data involved
- Identify what data may have been impacted in relation to this incident. Once identified, determine the impact to affected data (read, exfiltrated, modified, deleted) and determine ownership of data. This step can be difficult without a robust and mature data governance program in place, but narrowing down the impacted data involved will again help define the overall scope and potential impact of the incident.
- Notify Security Leader
- By this point it is important to engage the appropriate security and/or compliance leader of the active incident investigation and interim status along with an expected evaluation completion. This will allow decision makers to begin evaluating initial facts and considerations for disclosure.
- Identify how the incident occurred
- Identify how the incident occurred by evaluating method of attack, impacted resources, and evaluation of host logs.
- Provide feedback and lessons learned to reduce chances of a reoccurring incident
- Identify all vulnerabilities that were a part of this incident and provide steps to harden against such vulnerabilities in the future to the system, application, and data owners. Furthermore, provide a summary to the directors of those owners. Depending on the severity of the incident, you may also want to hold a lessons learned meeting with the directors and their managers.
Both examples are prime compliance use-case templates. When considering these playbooks or any other template for compliance purposes, it is important to continuously reevaluate their value, alignment with internal procedures, and reducing duplication.
To learn more about how LogRhythm can help you achieve compliance, visit our webpage overview.
The post How to Leverage Case Playbooks for Compliance appeared first on LogRhythm.
from LogRhythm https://ift.tt/jeMgULS
via IFTTT
No comments:
Post a Comment